A p2p penetration synchronization method and system
A technology for synchronizing systems and penetrating time, applied in the network field, can solve the problems of high probability of P2P penetrating failure and achieve the effect of increasing the probability of success
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
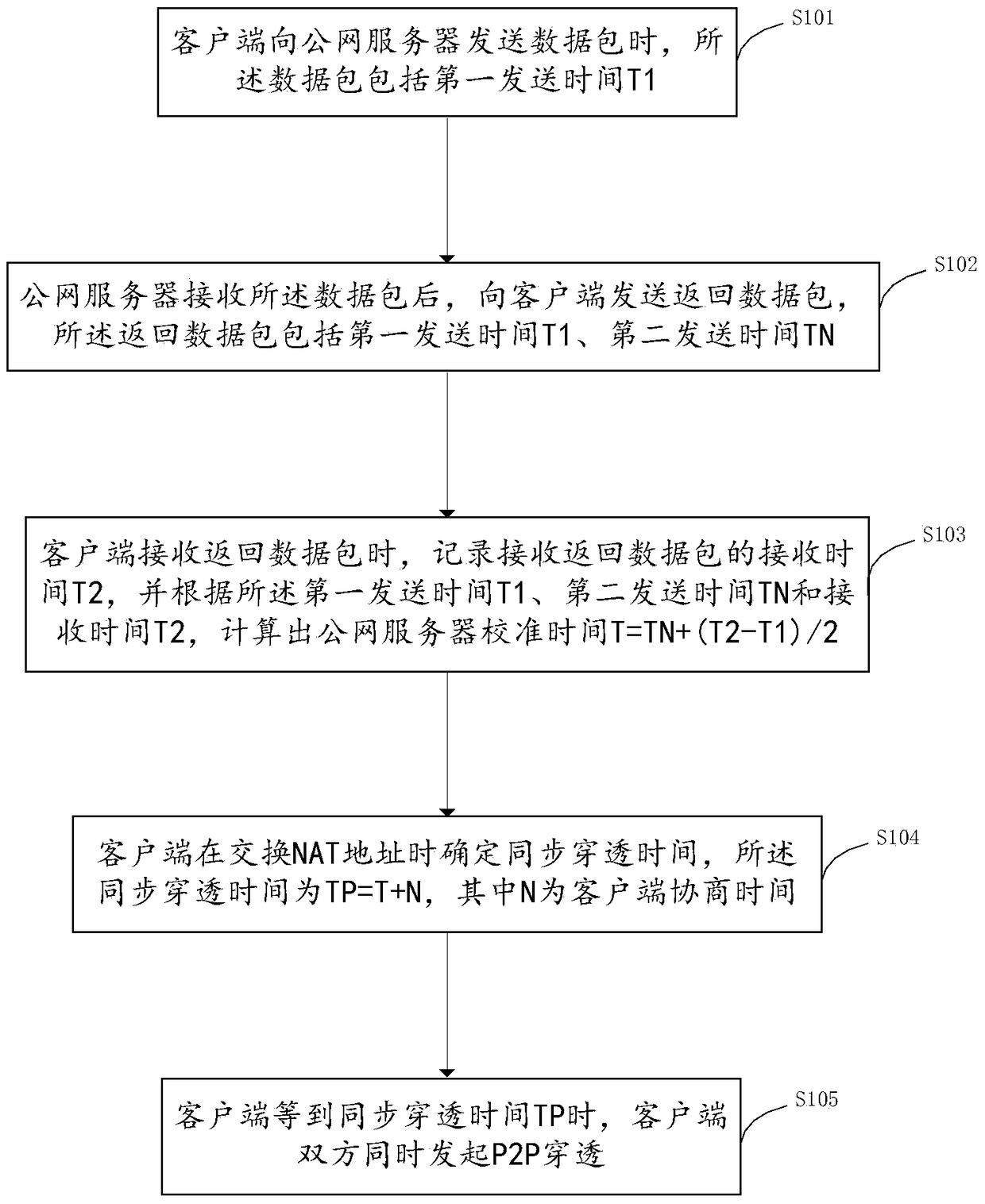
[0025] figure 1 The P2P penetration synchronization method provided by an embodiment of the present invention is shown, the method includes the following steps:
[0026] S101. When the client sends a data packet to the public network server, the data packet includes a sending time T1.
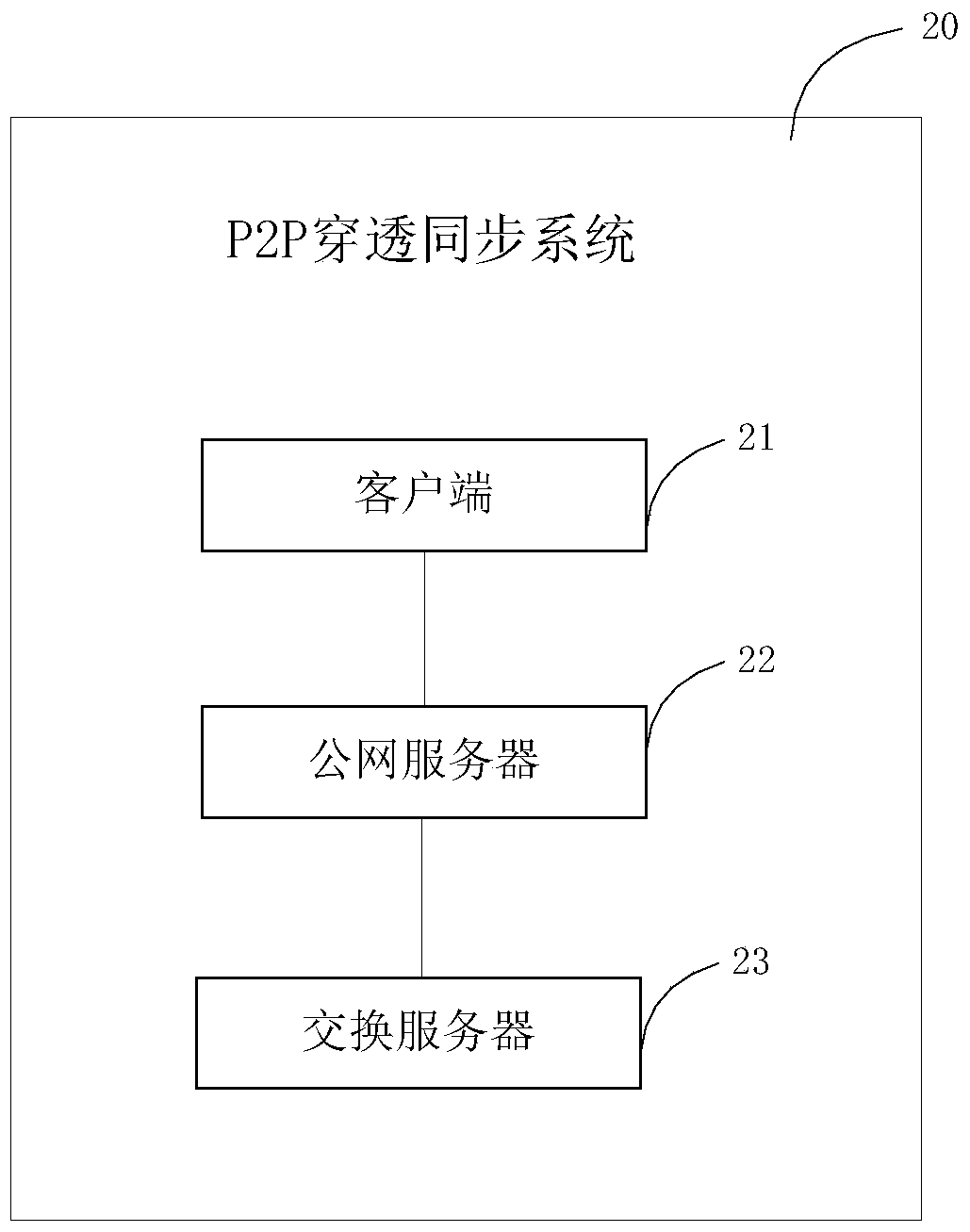
[0027] In this step, start the public network server and the exchange server, and start the P2P clients, that is, client A and client B. When client A sends a data packet to the public network server, the data packet includes the sending time of the data packet T1, and the data packet also includes the local IP address and port of the client.
[0028] S102. After receiving the data packet, the public network server sends a return data packet to the clien...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com