Database generalization safety protection method
A technology of security protection and database, applied in the field of information security, can solve the problems of being unable to discover unknown intrusion behaviors and low false positive rate of detection models, so as to improve the overall security protection capability and reduce the false negative rate and false negative rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
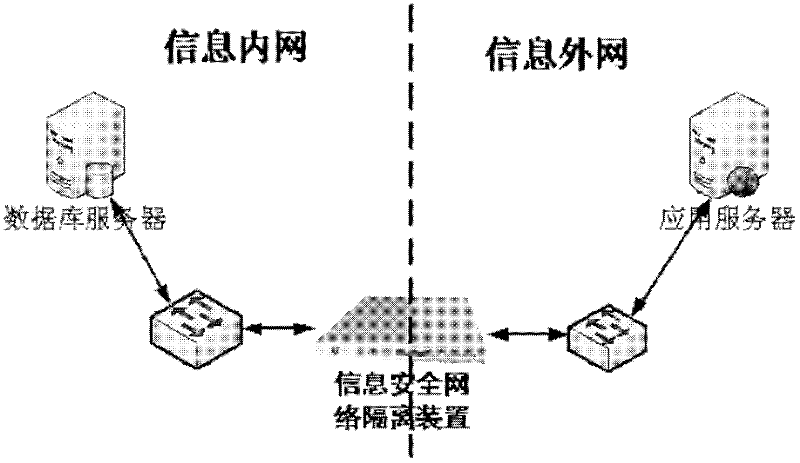
[0034] The following is a typical implementation of the database security gateway as an information network isolation device.
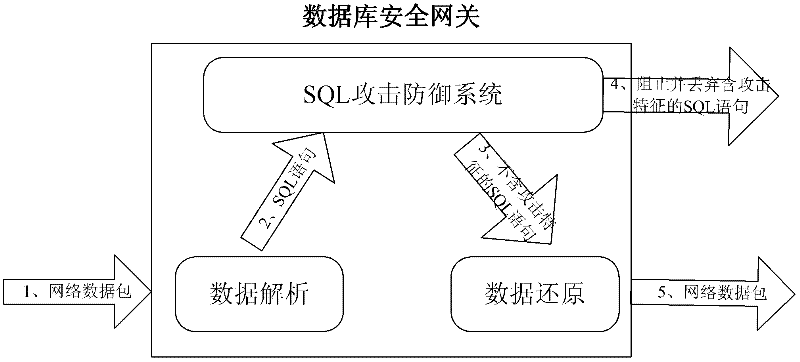
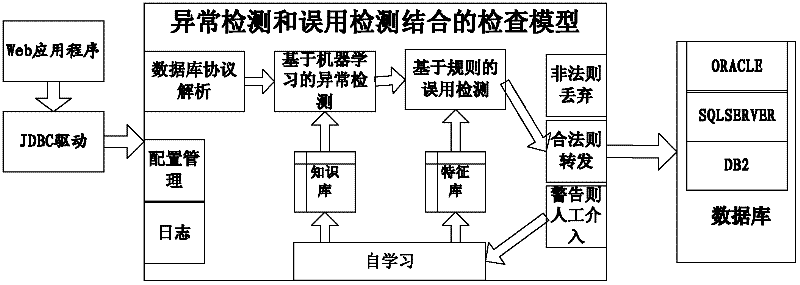
[0035] The database security gateway isolates the trusted information intranet from the untrustworthy information extranet. It must ensure that the SQL communication between the information intranet and the information extranet passes through the database security gateway for SQL detection. The database security gateway is a special device to protect the database to meet the needs of network partitioning according to the security level. Its core technology adopts a comprehensive database protection method based on the combination of abnormality and misuse. The solution of the invention can filter the network flow for accessing the Oracle / SQLSERVER database, only allow a specific application server to access a specific database server through a specific program, and control the content and behavior of the client program to access the database service.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com