Decentralized control system attack intrusion detection device and method thereof
A decentralized control system, intrusion detection technology, applied in general control systems, control/regulation systems, program control, etc., can solve the problem of high false negative and false positive rates, limited equipment resources, and increased network security threats and risks. and other problems to achieve the effect of reducing the false negative rate and false positive rate and ensuring the accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
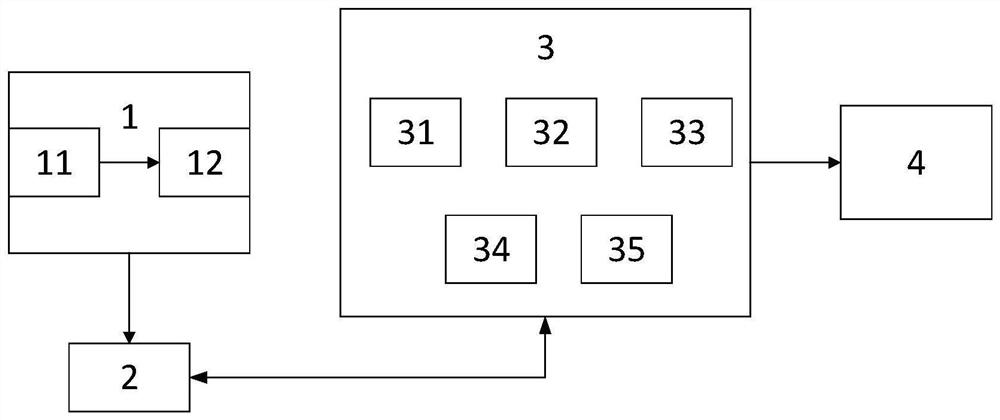
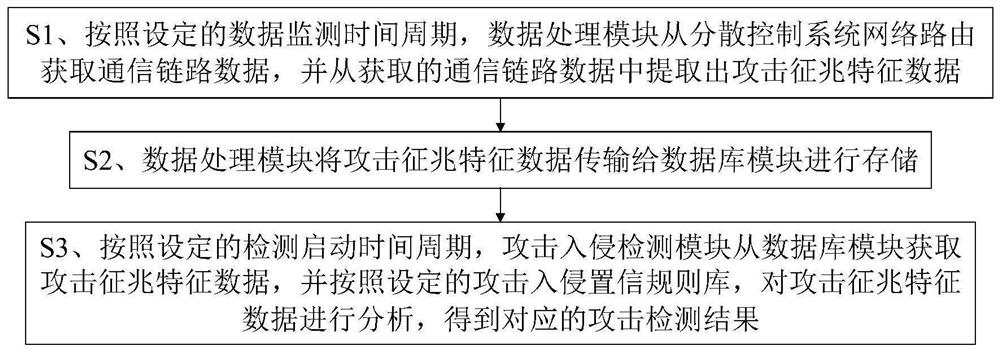
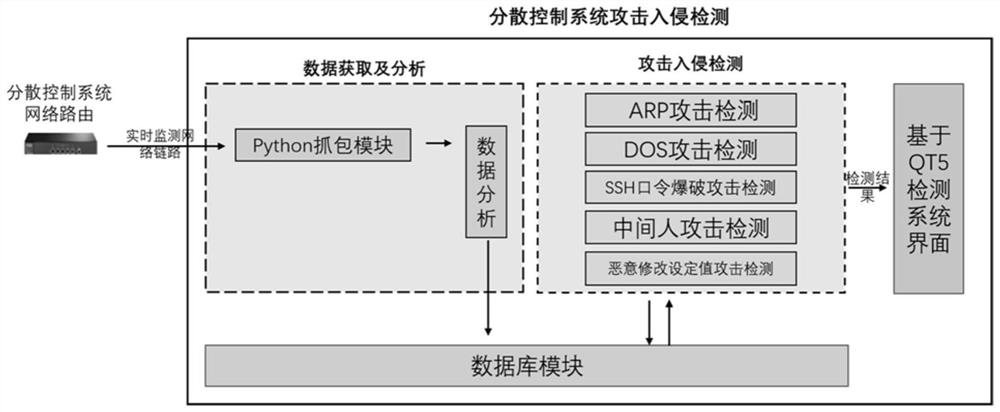
[0036] Such as figure 1 As shown, a distributed control system attack and intrusion detection device includes a data processing module 1 connected to a distributed control system network router, the data processing module 1 is connected to a database module 2, and the database module 2 is bidirectionally connected to the attack intrusion detection module 3, and the data The processing module 1 obtains communication link data from the distributed control system network router, and extracts attack symptom characteristic data from the communication link data;
[0037] The attack intrusion detection module 3 is used to analyze the attack symptom characteristic data according to the set attack intrusion confidence rule base, and obtain the attack detection result;
[0038] The database module 2 is used to receive and store the attack symptom characteristic data output by the data processing module 1, and receive and store the attack detection result output by the attack intrusion d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com