Stealing situation processing and optimizing method and system applied to burglar proofing of node B
A base station and stealing technology, applied in electrical components, wireless communication, etc., can solve the problems of wasting manpower, false alarms of anti-theft software systems, and inability to notify in time, and achieve the effect of flexible methods, reduction of redundant links, and optimization of processing functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the drawings.
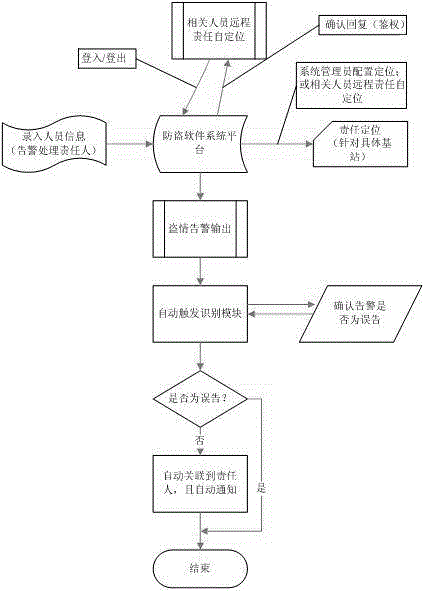
[0027] The processing flow of the present invention is as attached figure 2 As shown, in terms of the responsibility of the base station, first, the personnel information involved, such as name, mobile phone, etc., is manually entered in the anti-theft software system platform as the central software system through the authority of the system administrator. This information defines the scope of the responsible person. Responsibility designation adopts a combination of two modes: First, the system administrator directly designates the responsible person for different base stations on the system, the purpose is to designate the long-term responsible person for the base station; Second, the relevant personnel can use SMS via mobile phones Log in to the base station in the same way, log out by SMS, and cancel the responsibility association. The purpose is for short-term temporary managem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com