Data protection unit applicable to embedded system
An embedded system, data protection technology, applied in digital data protection, electrical digital data processing, instruments, etc., can solve the problem of difficulty in establishing the connection between plaintext and ciphertext, and achieve easy expansion, high security, and reasonable design. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
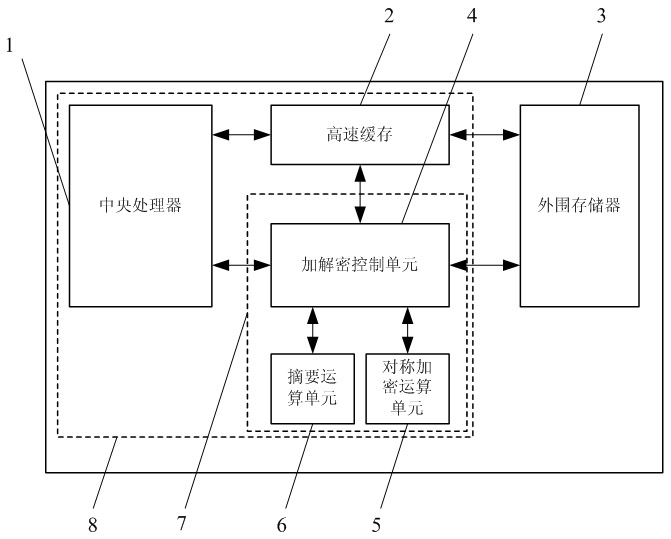
[0031] The present invention implements a data protection unit 7 suitable for embedded systems, which will be further described below in conjunction with the accompanying drawings.
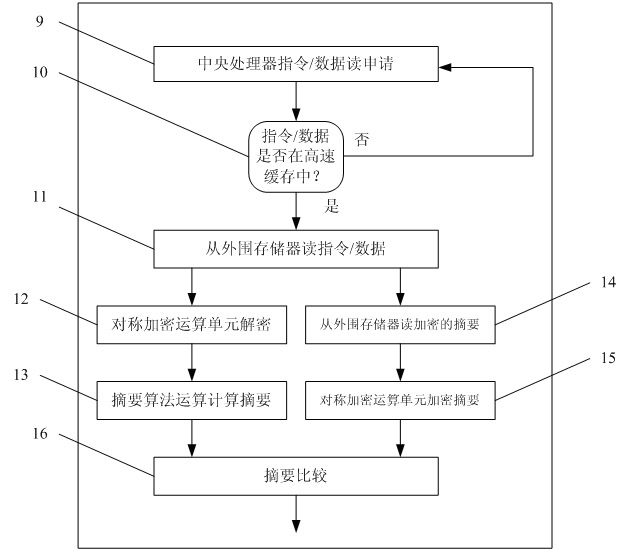
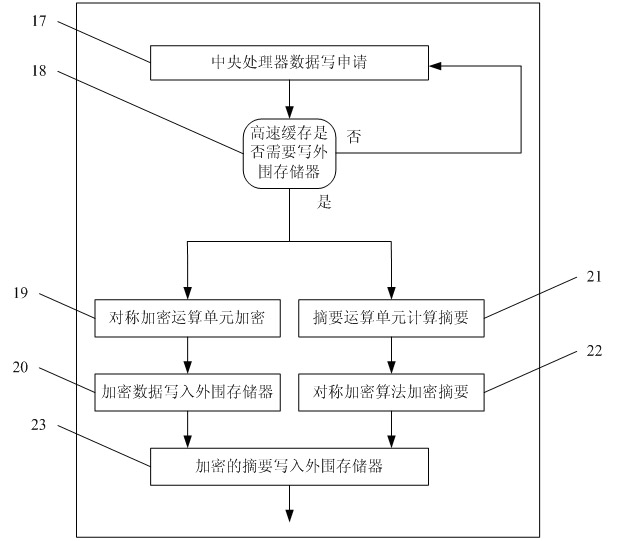
[0032] The embedded system includes a processor unit 1, a cache memory 2 and an off-chip memory 3. By adding an encryption and decryption control unit 4, a symmetric encryption operation unit 5 and a summary operation unit 6 in the embedded system, the confidentiality of software and data is realized and integrity verification.
[0033] Using the method of command customization, by configuring the encryption and decryption control unit 4, the entire data protection unit 7 can work in four modes, which are respectively:
[0034] No protected mode. It does not provide data confidentiality and integrity verification, and is generally used in occasions that do not require high program security. The system performance is the best in this mode.
[0035] Confidentiality verification mode. Provides dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com