Method and device for protecting software security
A software security, source file technology, applied in the computer field, can solve the problems of relying on the software and hardware environment, poor compatibility of anti-tracking technology, and difficulty in protecting software security, etc., to achieve the effect of improving security, increasing the workload and complexity of tracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
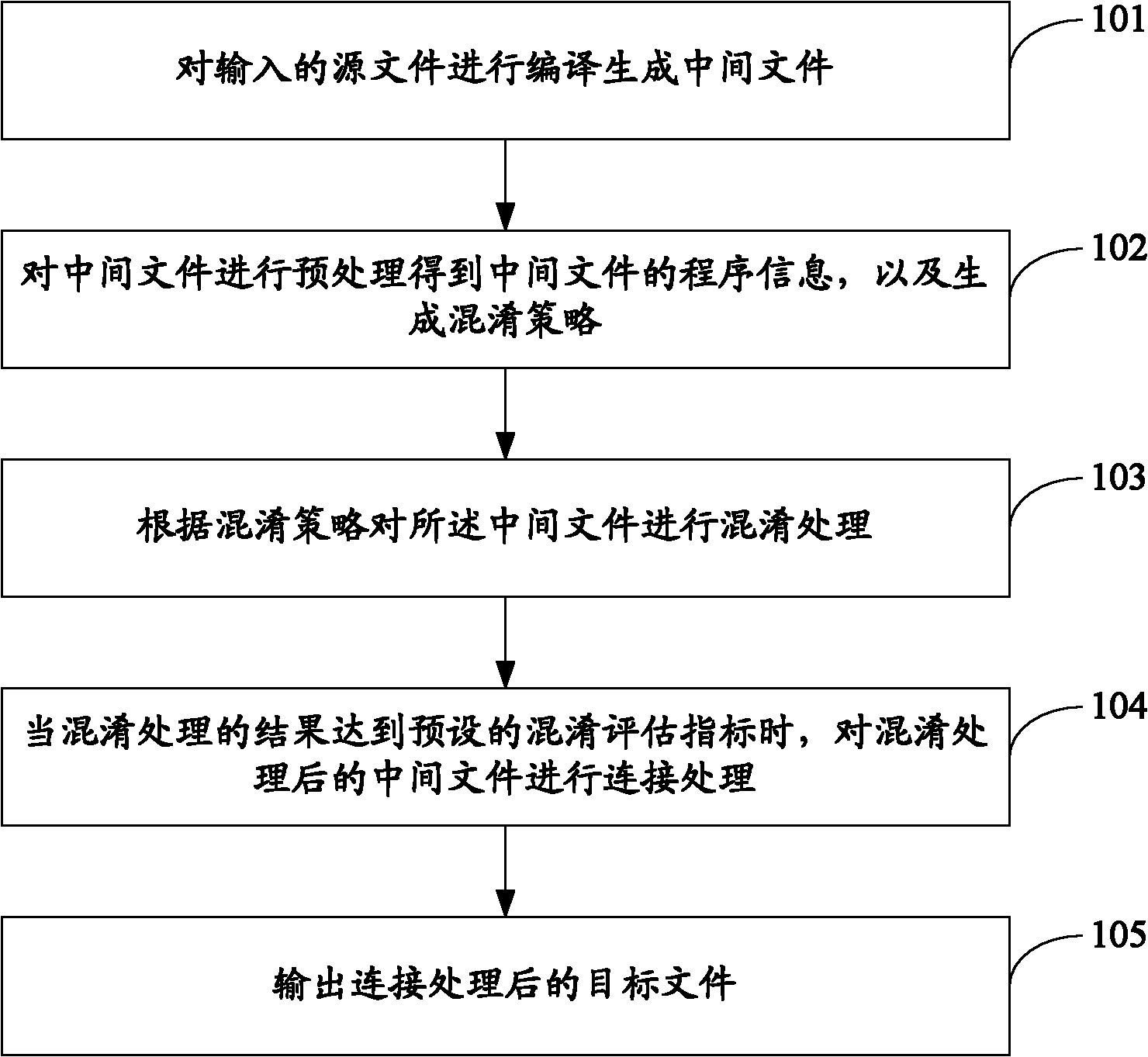
[0049] see figure 1 , which is the flow chart of the first embodiment of the method for protecting software security in this application:
[0050] Step 101: Compile the input source file to generate an intermediate file.
[0051] Among them, the intermediate files include: symbol table, control flow and assembly instructions.
[0052] Step 102: Preprocessing the intermediate file to obtain program information of the intermediate file, and generating an obfuscation policy.
[0053] Wherein, preprocessing the intermediate file includes: performing process analysis, data flow analysis and data dependency analysis on the intermediate file.
[0054] Wherein, the obfuscation strategy may be generated according to pre-set obfuscation parameters, and the obfuscation parameters may include obfuscation strength and obfuscation elasticity. Specifically, different obfuscation strengths and confusion resiliency are obtained according to needs, and the obtained obfuscation strength and c...
no. 2 example
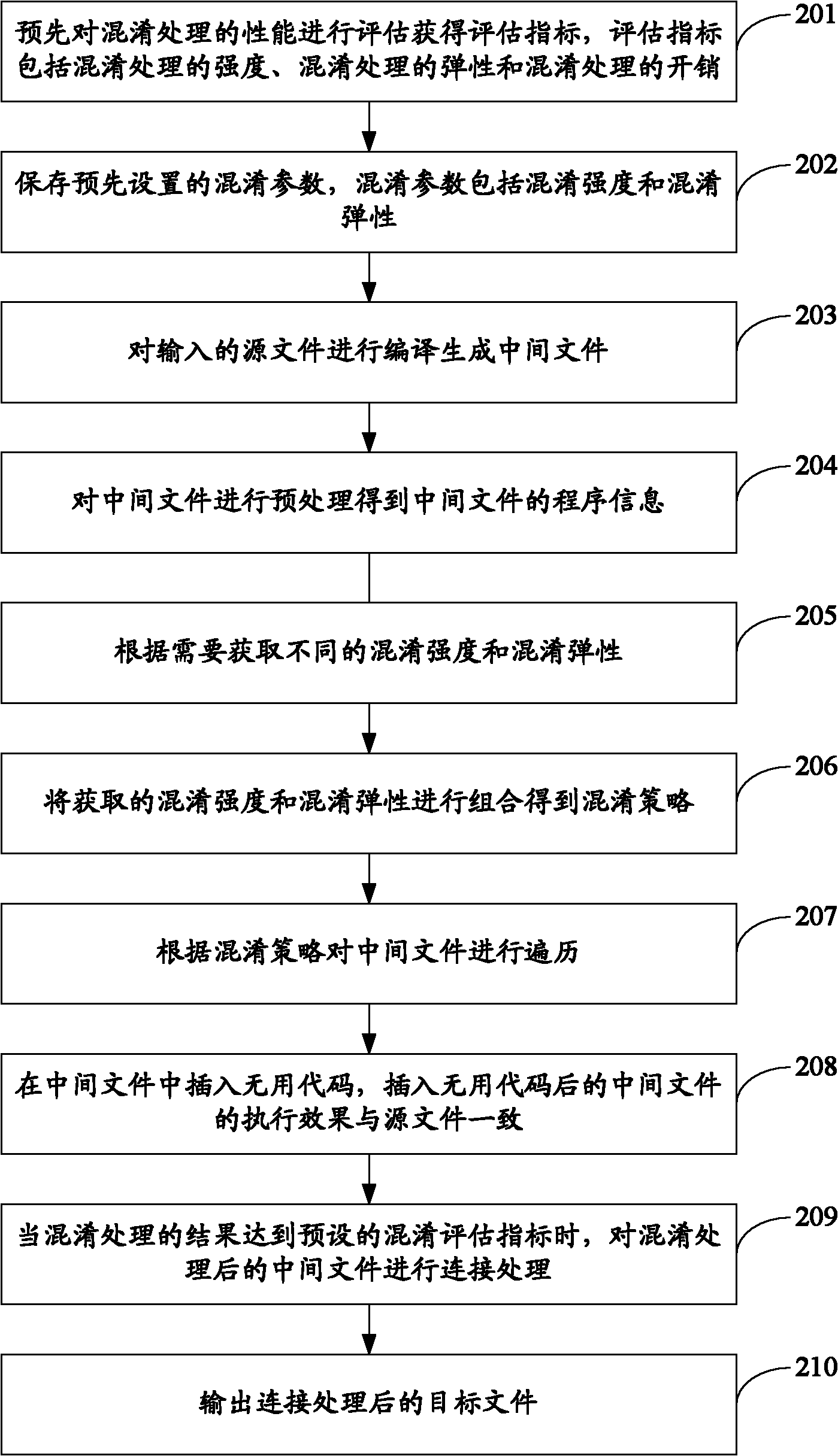
[0060] see figure 2 , which is the flow chart of the second embodiment of the method for protecting software security in this application:
[0061] Step 201: Evaluate the obfuscation performance in advance to obtain an evaluation index, the evaluation index includes the intensity of the obfuscation processing, the flexibility of the obfuscation processing, and the overhead of the obfuscation processing.
[0062] The technique for obfuscating code is a special compilation technique that converts a source program P into an object program O(P). 0(P) has the same external behavior as P, but the code is more secure. The requirements for obfuscation can be described as:
[0063] Let T be a transformation from the source program P to the target program 0(P), if P and 0(P) have the same observable behavior, and satisfy the following two conditions: ①If P cannot terminate or terminates with an error state , then 0(P) may or may not be terminated; ②Otherwise, 0(P) must be terminated a...
no. 1 example
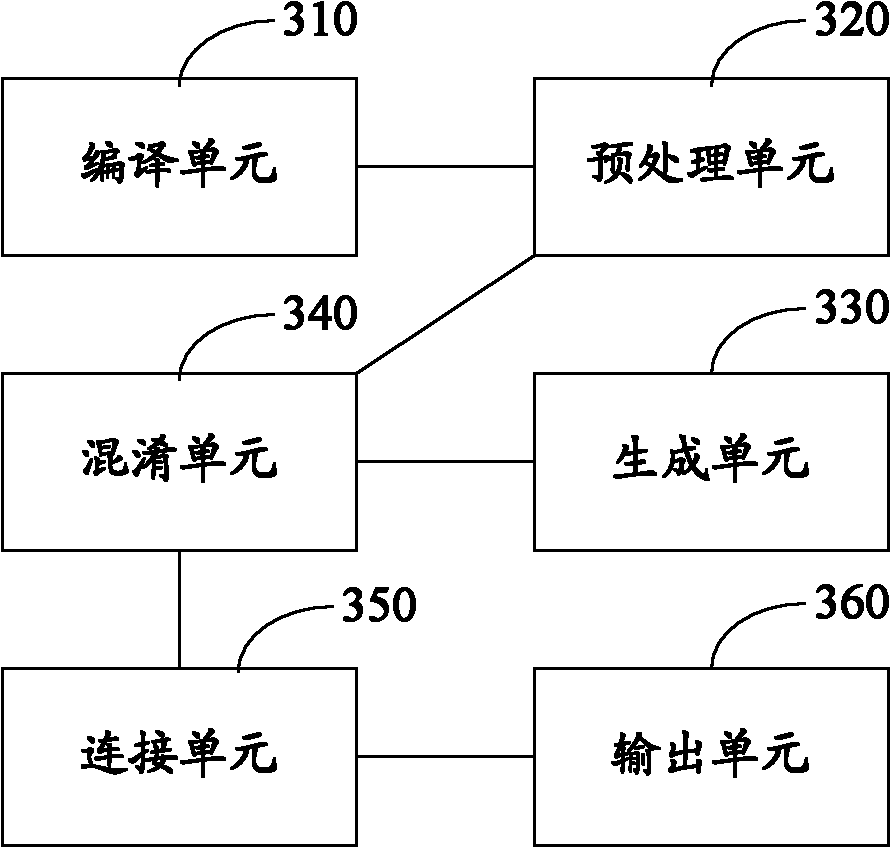
[0086] see image 3 , which is a block diagram of the first embodiment of the device for protecting software security in this application:
[0087] The device includes: a compilation unit 310 , a preprocessing unit 320 , a generation unit 330 , an obfuscation unit 340 , a connection unit 350 and an output unit 360 .
[0088] Wherein, the compiling unit 310 is configured to compile the input source file to generate an intermediate file;
[0089] A preprocessing unit 320, configured to preprocess the intermediate file to obtain program information of the intermediate file;
[0090] A generating unit 330, configured to generate an obfuscation strategy;
[0091] An obfuscation unit 340, configured to obfuscate the intermediate file according to the obfuscation policy;
[0092] A connection unit 350, configured to perform connection processing on the obfuscated intermediate files when the result of the obfuscation processing reaches a preset obfuscation evaluation index;
[009...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com