Information privacy and identity authentication method and digital signature program
A technology of information security and symmetric cryptographic algorithm, which is applied in the fields of computer software, network communication and information security, and can solve the problems of inability to cope with close voyeurism, low operation efficiency, and lack of consideration of hardware diversity support of cryptographic devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
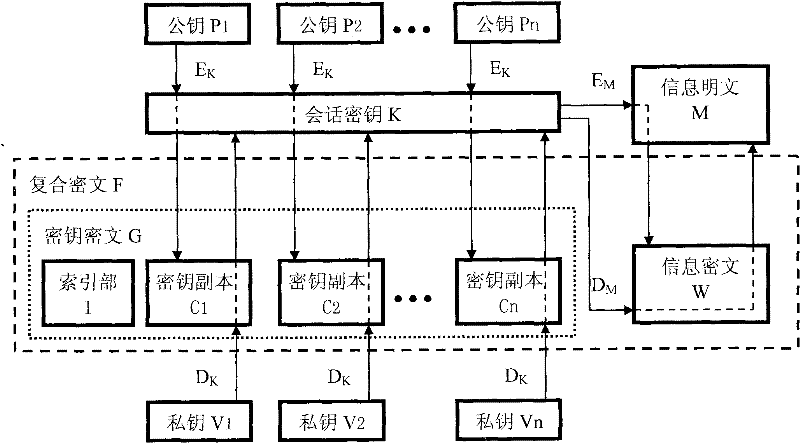
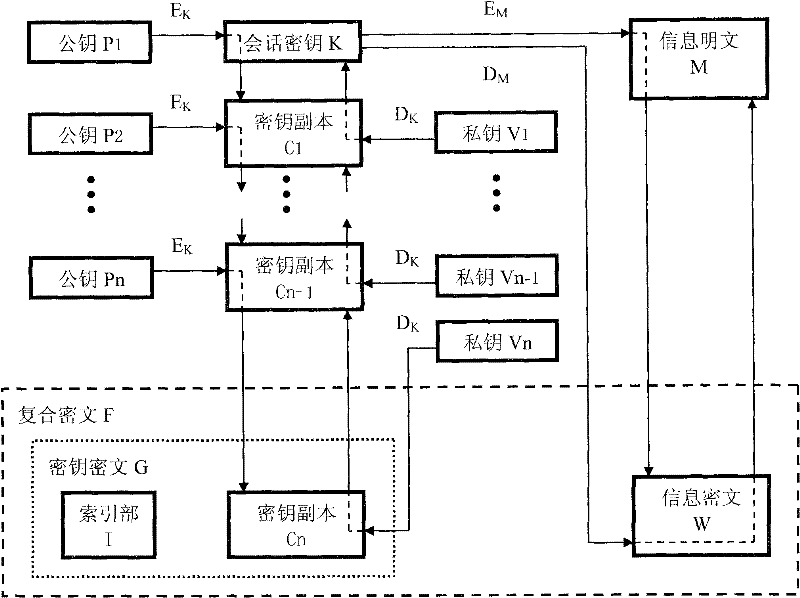
[0023] An embodiment of the information security method of the present invention. Compile a utility program with a Windows dialog box structure, named "information security program". The main operation interface structure of the program, such as image 3 Shown. The program integrates a cryptographic device product with a USB interface called "Crypt Golden Armor", loads its supporting API dynamic link library, and calls its programming interface functions to implement encryption and decryption functions. In response to equipment change messages, the program automatically detects the access and removal of the cryptographic device, and provides a criterion for the availability of the cryptographic device for encryption and decryption operations. Program function interface, refer to image 3 design. Program function flow processing, refer to figure 1 with figure 2 achieve. The symmetric algorithm for encrypting information uses AES; the asymmetric cryptographic algorithm for en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com