System and method for implementing security protection of PIN code
A PIN code and security protection technology, applied in the field of network security authentication processing, can solve problems such as security risks, and achieve the effect of improving security and preventing replay attacks
Active Publication Date: 2011-01-05
INDUSTRIAL AND COMMERCIAL BANK OF CHINA
View PDF1 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In view of this, the main purpose of the present invention is to provide a system and method for implementing security protection of the PIN code, to overcome the defect of using plain text in the PIN code authentication process of the current USBKEY, and to solve the problem of PIN code input on the keyboard, client side, etc. The potential safety hazards in memory storage and interface access, etc., realize the effective protection of PIN code, and further improve the security of USBKEY
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
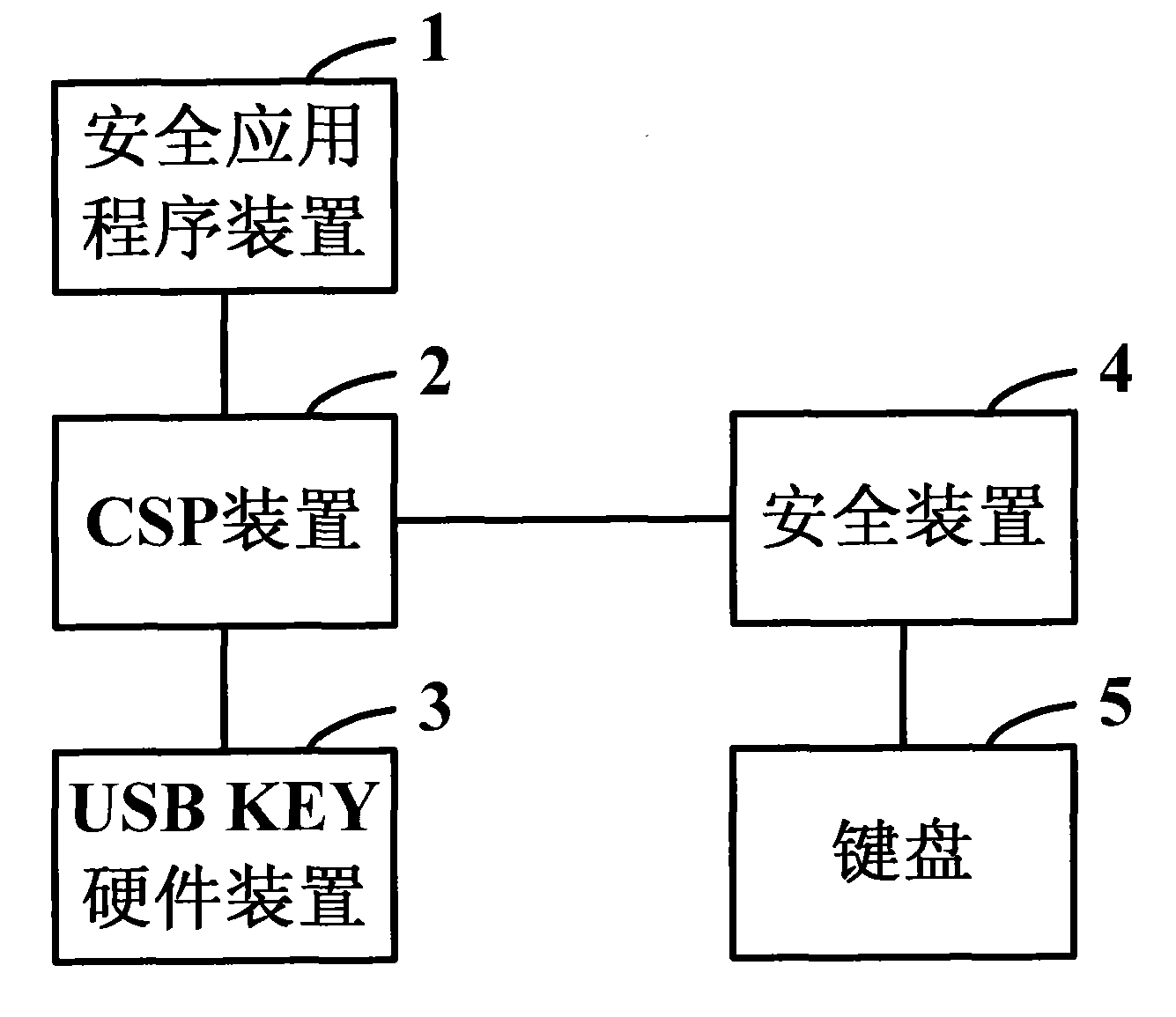
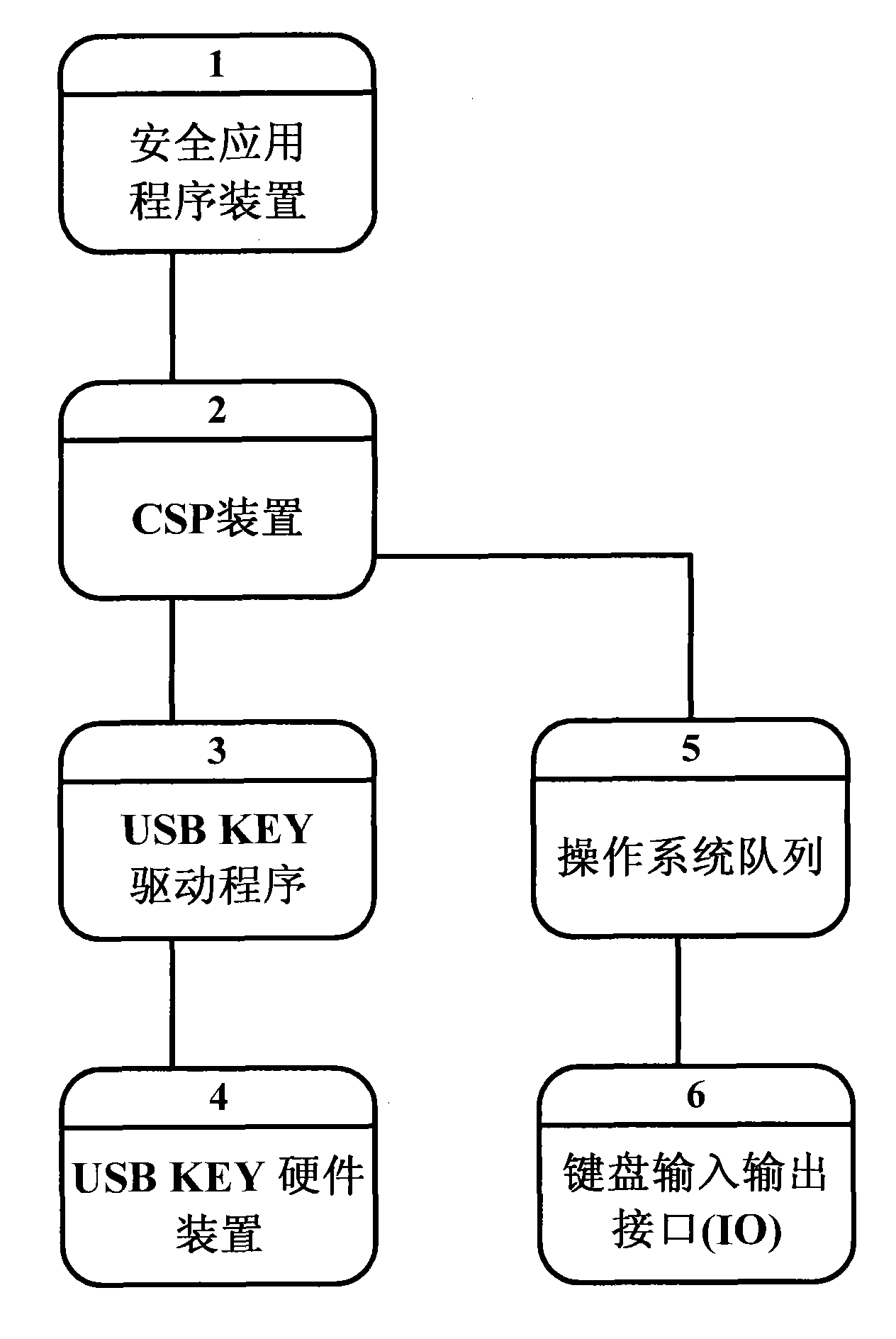
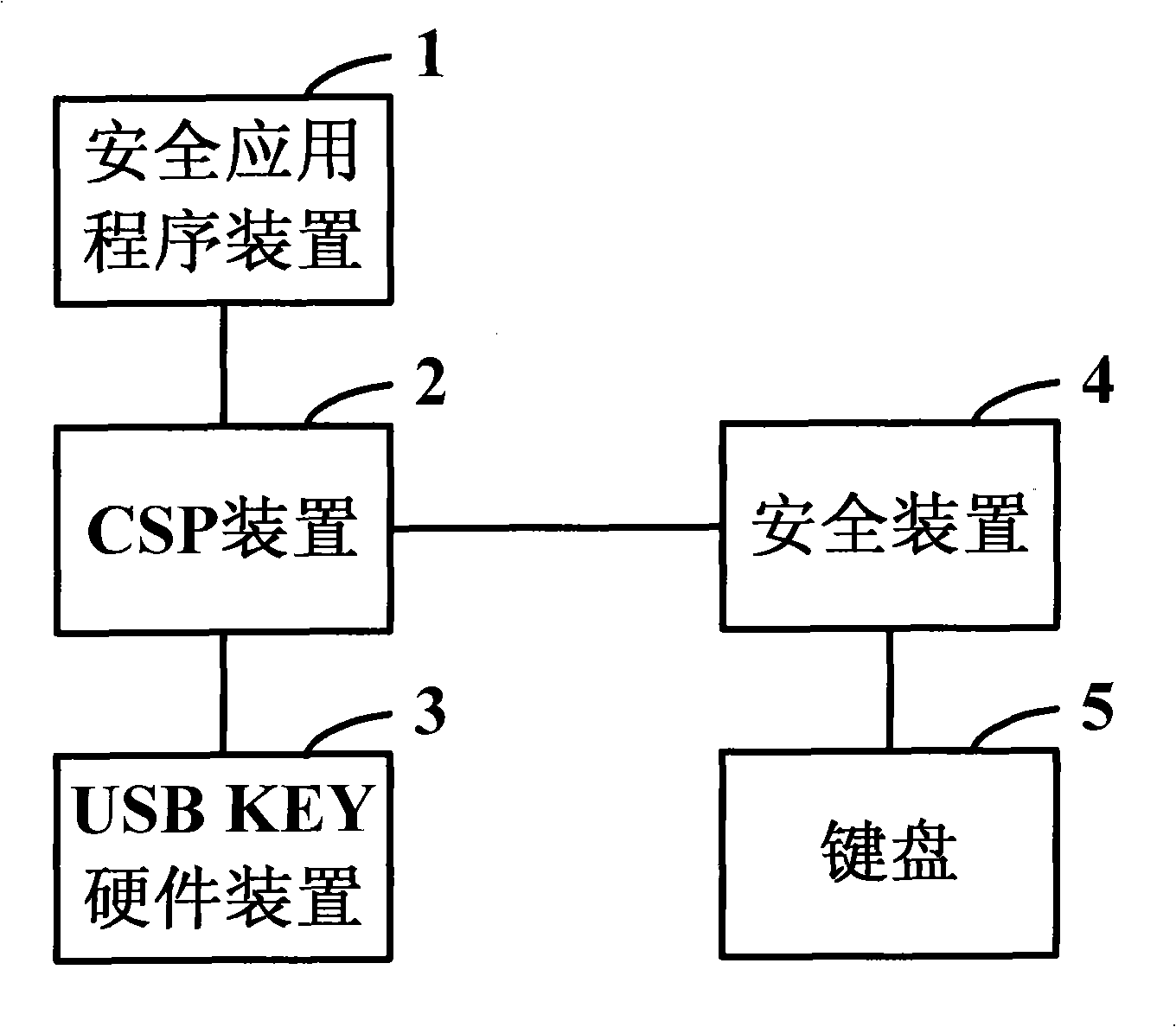
The invention discloses a system and a method used for protecting a PIN code. When the PIN code of the user requires verification, USB KEY hardware equipment generates random numbers and submits the numbers to completely-self-protected equipment, and then the completely-self-protected equipment sends the numbers into security equipment. The security equipment pops up a PIN code input prompt box into which the user inputs the PIN code by a keyboard. The security equipment guarantees the safety of data transmission between the user keyboard and the security equipment. After inputting the PIN code, the user clicks OK. The security equipment abstracts and processes the random numbers and the PIN code input by the user, and returns the outcome data after abstracting and processing to the completely-self-protected equipment. The completely-self-protected equipment sends the outcome data after abstracting and processing to the USB KEY hardware equipment for verification. The invention solvesthe potential safety hazards caused by a plaintext method adopted in the PIN code verification process of the existing USB KEY software equipment, thus realizing effective protection of the PIN code,and improving the safety of USB KEY further.
Description
A system and method for realizing security protection of PIN code technical field The invention relates to the technical field of network security authentication processing, in particular to a system and method for realizing security protection of a PIN code. Background technique With the rapid development of my country's online banking, various attack techniques and methods aimed at stealing funds emerge in an endless stream, and the attack methods are refurbished, which poses a serious threat to the security of online transactions. At present, the online banking of my country's commercial banks mostly uses digital certificates in terms of security authentication. The carriers of digital certificates currently include USBKEY, chip card, etc., for example: the application number is 200410028723.9 (patent name: device for encrypting and authenticating online banking data and method) patent application discloses a device and method for online banking security authentication ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L9/32H04L9/38
Inventor 王凯刘明潘葛桐
Owner INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Patsnap Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com