Intelligent protocol parsing method and device
A technology of protocol analysis and intelligent analysis, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as protocol in-depth analysis errors, difficulty in accurate protocol analysis, and inability to match, so as to improve accuracy and strong versatility of the method , the effect of high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0051] Embodiment 1 (BitTorrent protocol static feature):
[0052] %13BitTorrent%20Protocol can identify the BitTorrent protocol or the BitTorrent message type in the software communication process using the BitTorrent protocol, which can be used as a static identification rule for the BitTorrent protocol;
[0053] Create BITTORRENT protocol static identification rule set:
[0054] The text must contain the string "Bittorrent";
[0055] etc., as the actual packet sample is:
[0056] GET / announce? info_hash=%OD%40_%F3%0A%269%81%94%B9 / %B80%5EC%8A%8
[0057] A%9A%9C%E5&peer_id=Plus---tL3l5oWGtwZ9o&port=9096&uploaded=0&dow
[0058] nloaded=0&left=28742712&event=started HTTP / 1.0..Host: btfans.332
[0059] 2.org:8000..Accept-encoding:gzip..User-agent:BitTorrent / Plus!
[0060] II 1.02 RC1....
[0061] However, it is difficult to judge the specific software or version in some cases. For example, if an IP packet is found to carry the protocol static feature "HTTP", it is very l...
Embodiment 2
[0062] Embodiment 2 (BitTorrent protocol behavior characteristics):
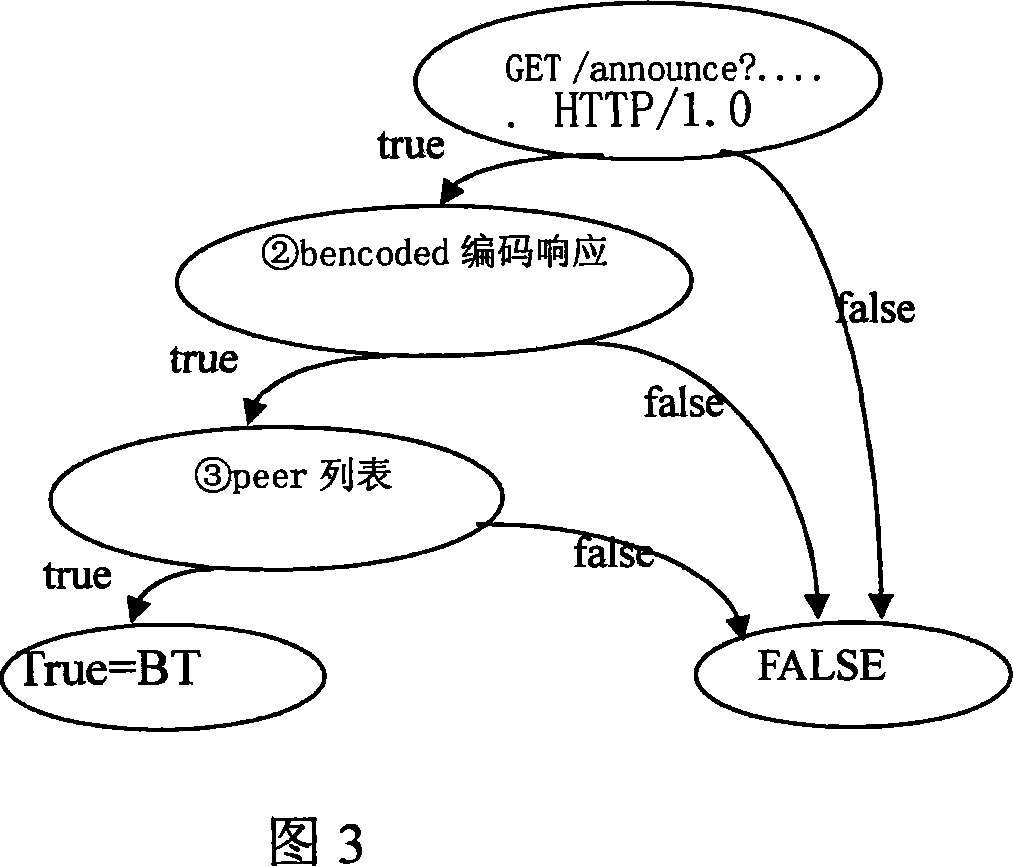
[0063] First use the track HTTP protocol to interact with the tracker server:
[0064] 1) The client sends an HTTP GET request to the tracker
[0065] The feature of this step is: GET / announce.....HTTP / 1.0 sends a GET request to Tracker, including the keyword Bittorent:
[0066] 2) The tracker returns the information of the downloader of the same file to the other party. The feature of this step is: the address and port of the dictionary list Peers encoded with bencoded.
[0067] 3) The BitTorrent client sends a connection request according to the obtained peer list. The feature of this step is: the connection request for each peer includes the keyword "BitTorrent".
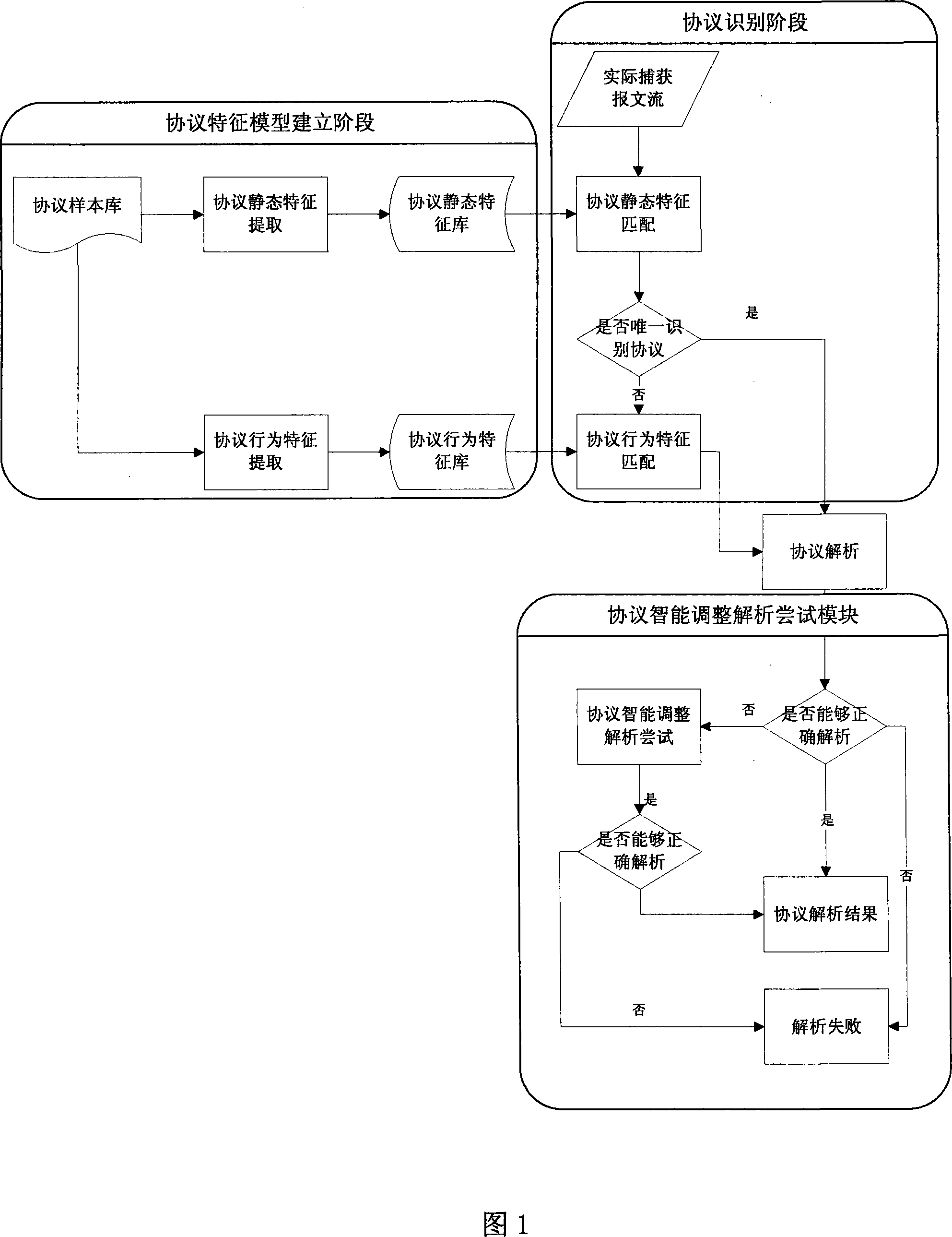
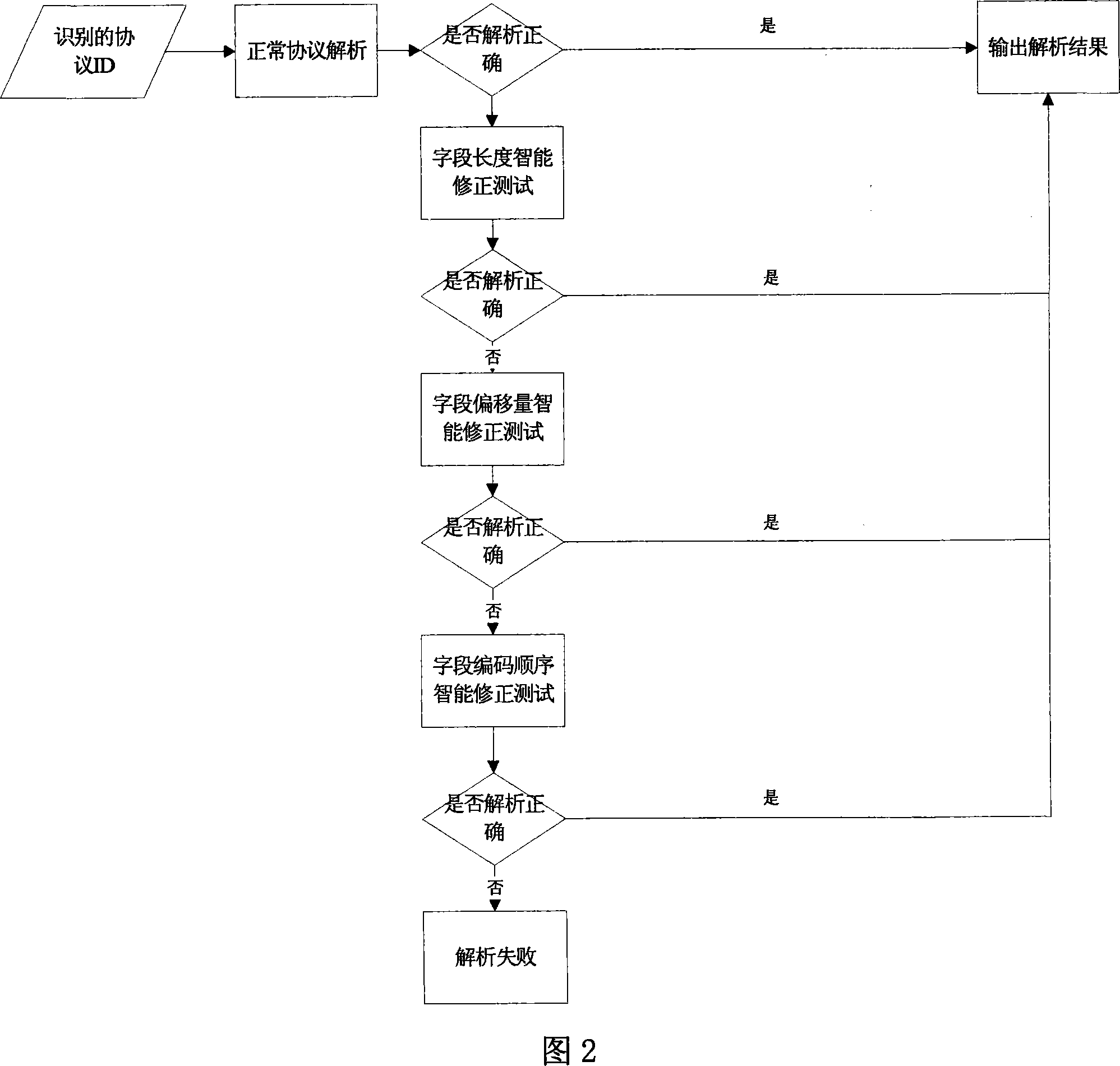
[0068] Protocol feature extraction; feature extraction is mainly divided into two steps, the first is static feature extraction of protocol data packets. This part mainly relies on a single data packet to make a preliminary judgment on the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com