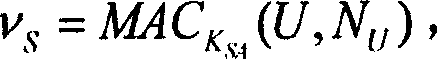Conversation key safety distributing method under wireless environment
A session key, wireless environment technology, applied in key distribution, can solve problems such as many exchange rounds, protocol failure, and difficulty in implementing authentication and key agreement mechanisms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
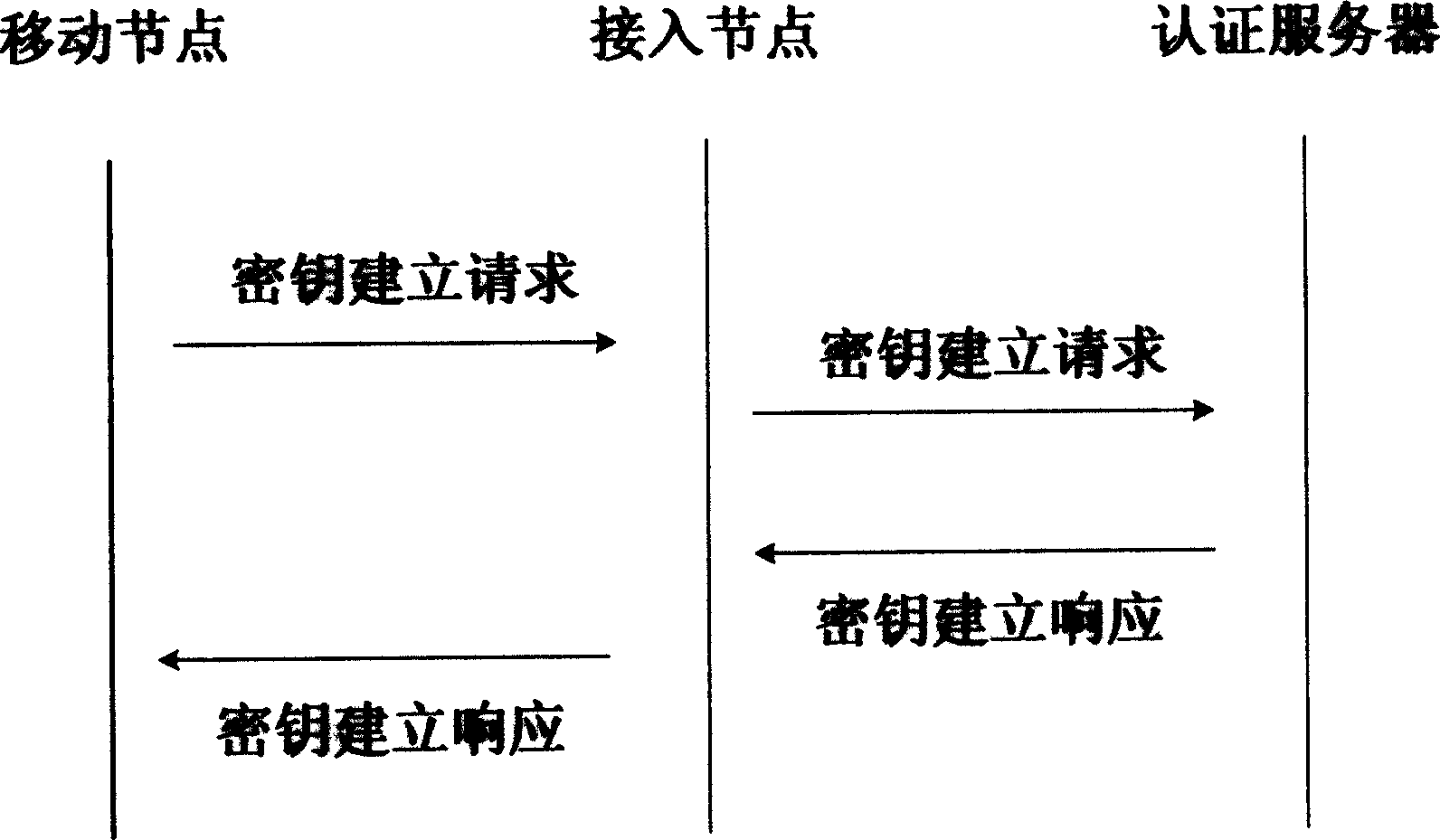
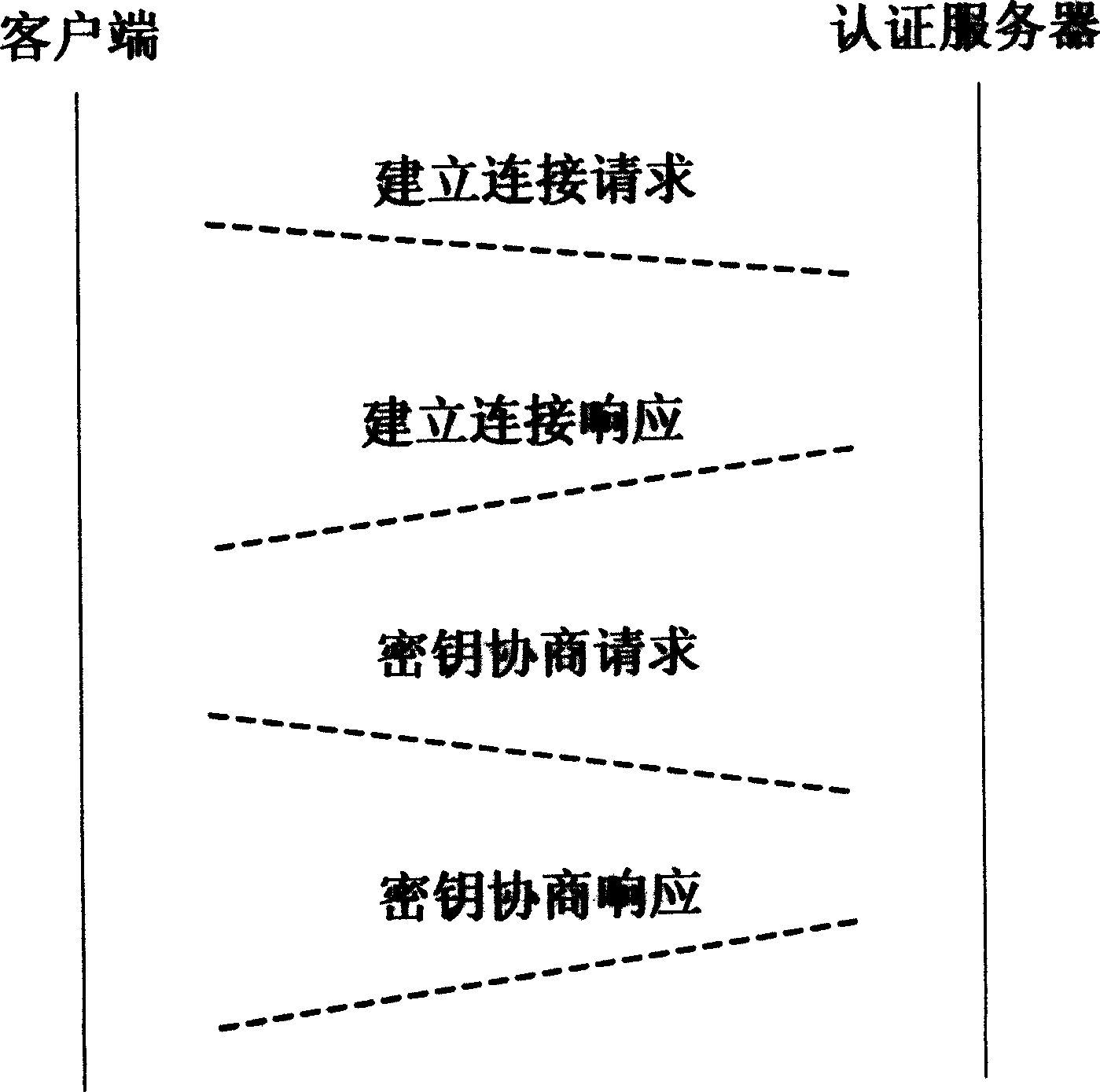
[0060] For now, wireless mobile terminal devices cannot undertake large public key calculations, and the huge number of users also makes it difficult to cope with the public key infrastructure that has not been widely deployed. The pre-shared key is used for authentication, and the link between them is best protected by symmetric key operation. However, with the development of modern wireless networks, access points and authentication servers have higher computing power, so public keys can be used for authentication between them, and the links between them should be considered to be more flexible. And secure public key computing method for protection. In addition, the designed protocol should have a complete security proof to ensure its security. To this end, the present invention adopts the following specific implementation methods.
[0061] In the present invention, the reliable authentication server ASU uses two different encryption methods to send the session key respect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com