Attestation method and safe identification method for network identity
A technology of network identity and authentication method, applied in the field of network identity authentication, can solve the problem of inability to implement, dare not release data easily, and achieve the effect of avoiding deception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical content, features and effects of the present invention will be described in detail below in conjunction with the preferred embodiments given in the accompanying drawings.
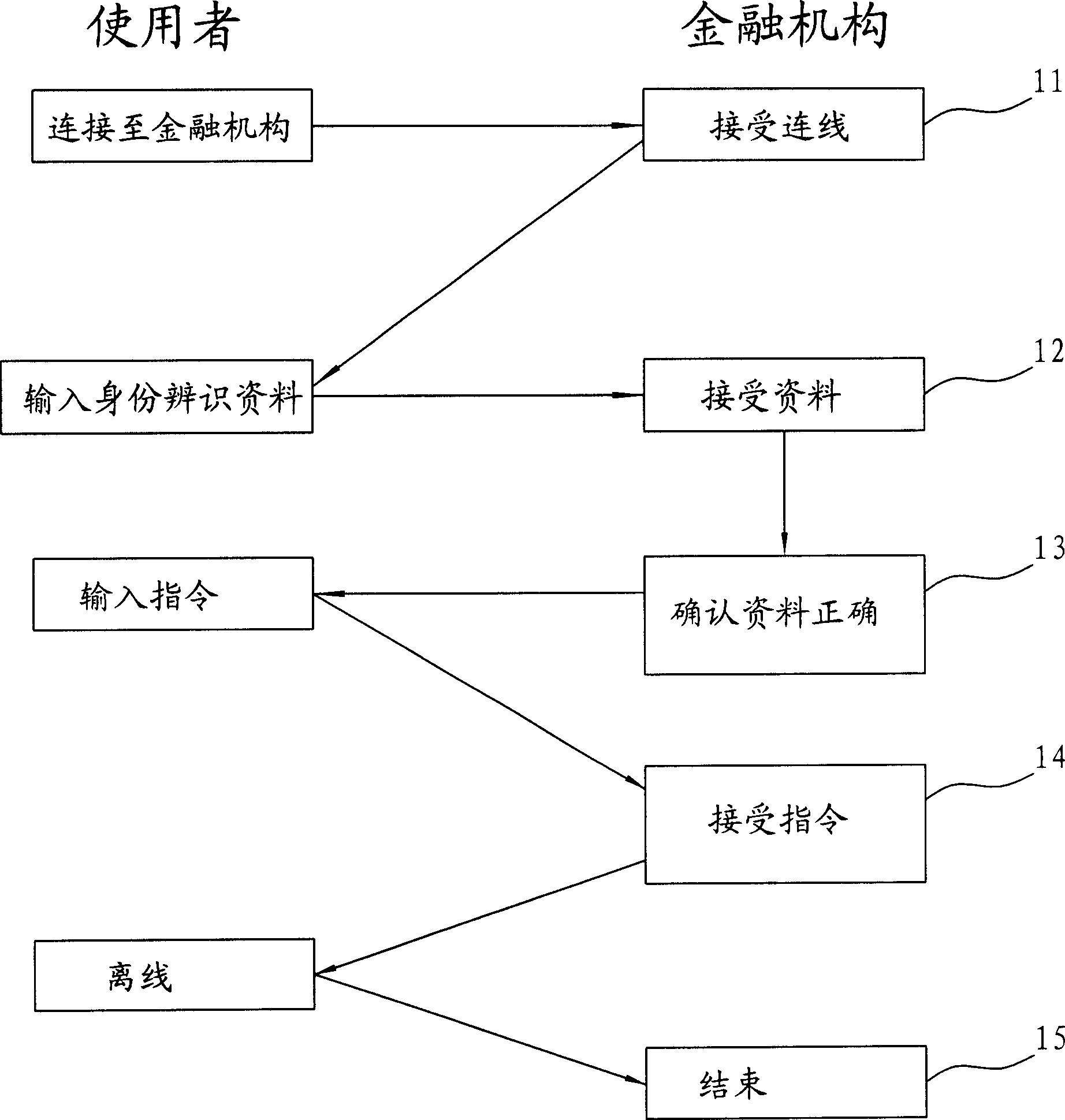
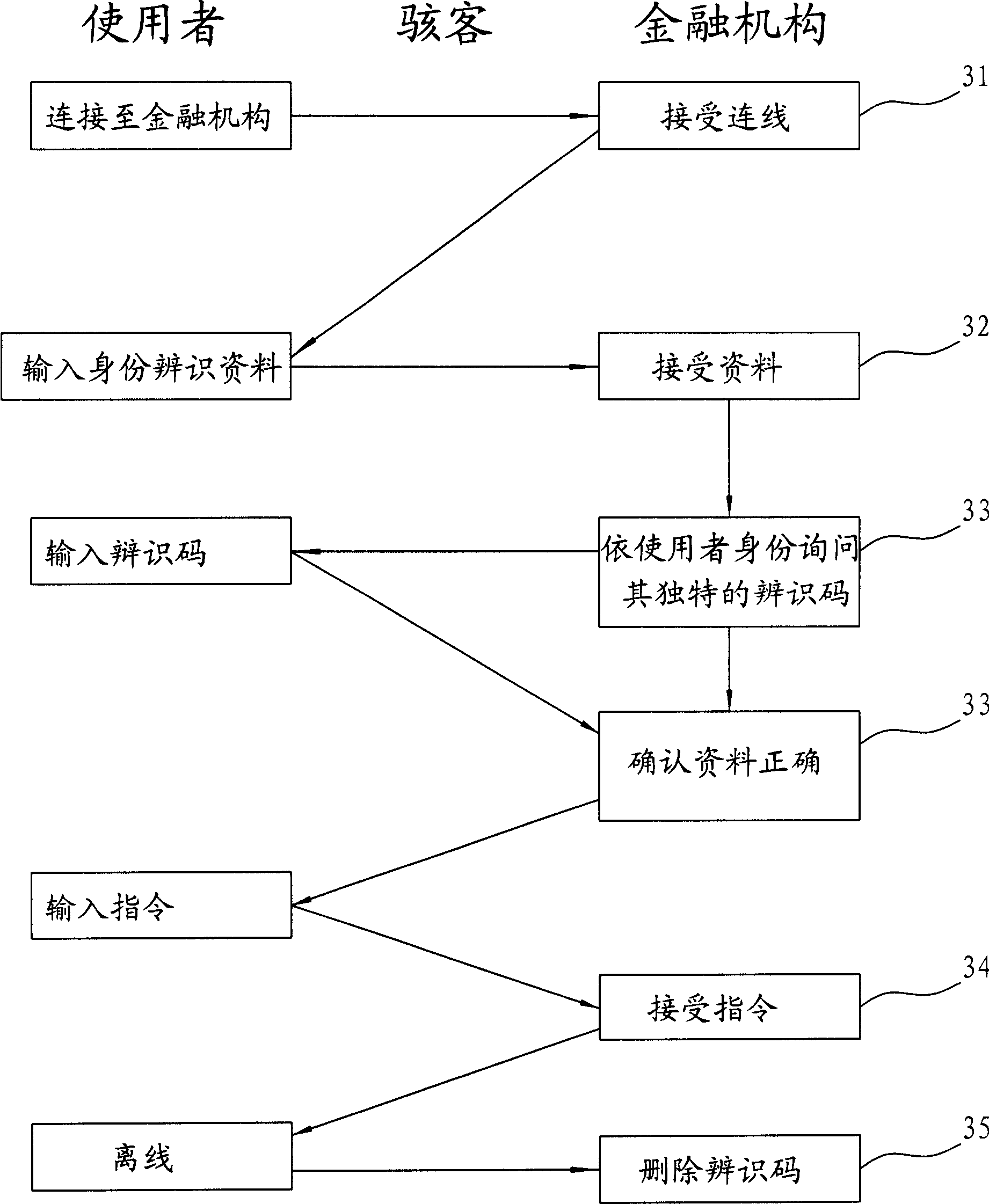
[0039] like figure 2 As shown, the Chinese invention patent application No. 200410037286.7 proposed by the applicant provides a method for identity authentication with a password library, which requires the user to bring a password machine or a password card in addition to memorizing his own account password. Store a certain number of identification passwords on the memory card or password card of the machine, and each password has a fixed corresponding address. When a financial institution accepts the user's connection in step 31, it then requires the user to input such as name, ID card number, identity authentication password and other identity identification data; and after the server confirms that the above information is correct in step 33, it will choose any password address to i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com