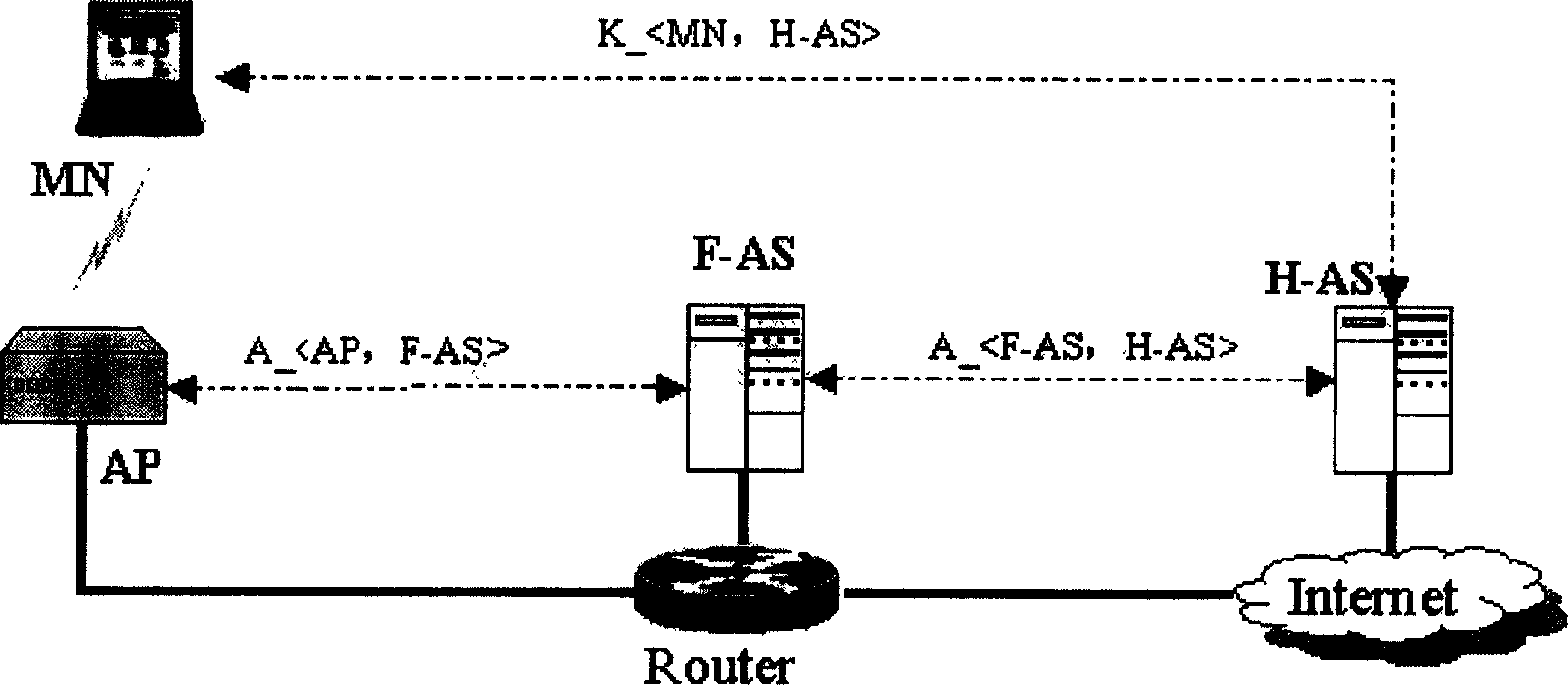
Radio LAN security access method based on roaming key exchange authentication protocal
A wireless local area network and authentication protocol technology, applied in the field of wireless local area network security access, can solve the problems of loss of security properties, difficult operation, inability to provide identity protection and session key consistency, etc., to achieve user identity protection and improve protocol performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
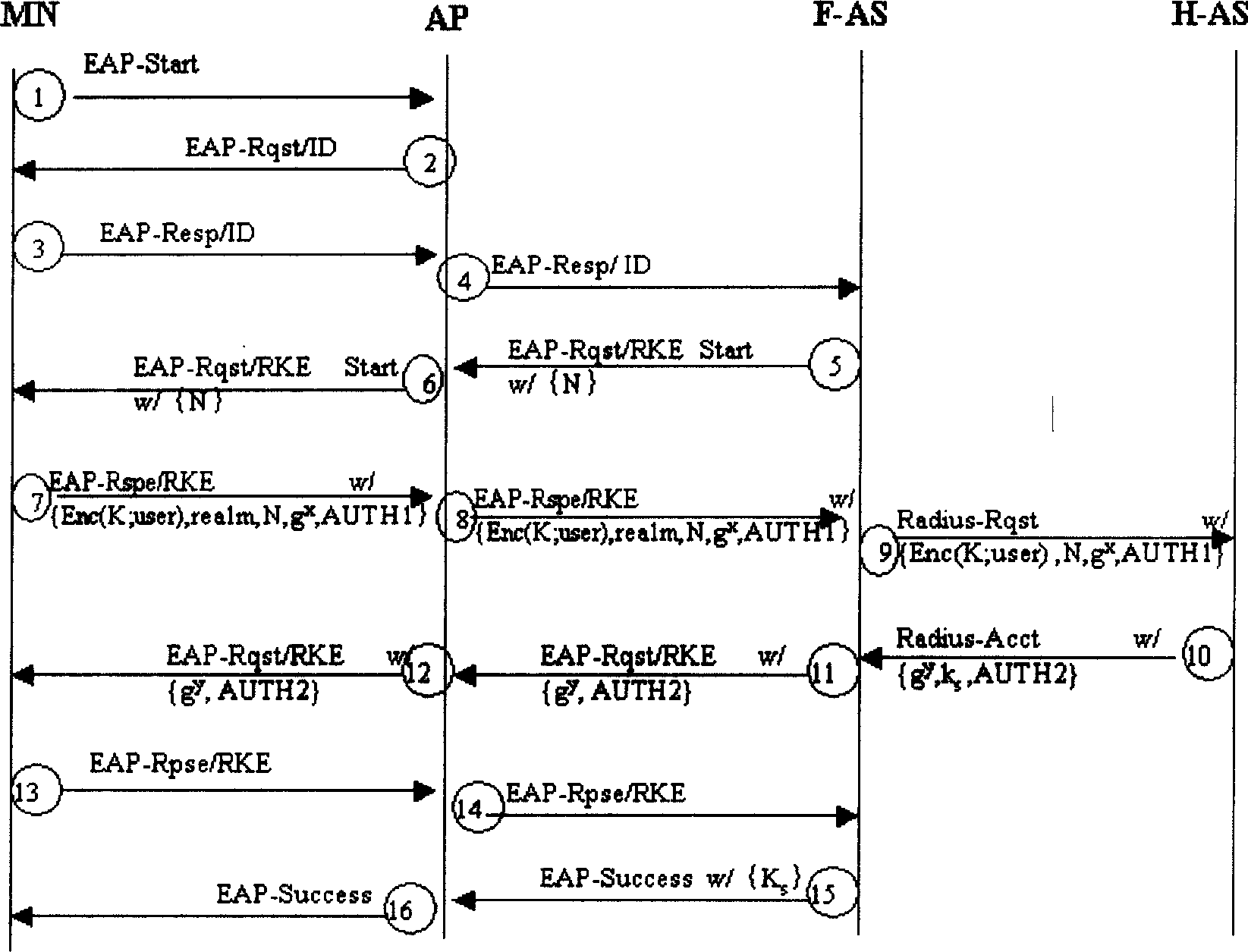
[0138] exist figure 1 In the identity authentication process shown, another implementation manner of encrypting the identity of the mobile node MN is:
[0139] The mobile node MN associates its identity user with a random number m, such as cascading user and m or performing XOR operation on user and m, and then uses the public key g of the home authentication server H-AS a encryption. Send the encrypted identity and random number to the home authentication server H-AS.
[0140] exist figure 1 In the identity authentication process shown, another implementation of the identity authentication of the home authentication server H-AS is:
[0141] The home authentication server H-AS uses its private key a to sign, and generates the identity authentication message of the home authentication server H-AS.
[0142] EAP-RKE performance comparison
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com