Vulnerability detection processing method and device, computer and readable storage medium
A processing method and vulnerability detection technology, which is applied in the computer field, can solve problems such as false positives of vulnerability scanning, inability to obtain virtual machines, and low efficiency of virtual machine vulnerability detection, and achieve the effect of improving accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
test Embodiment 702
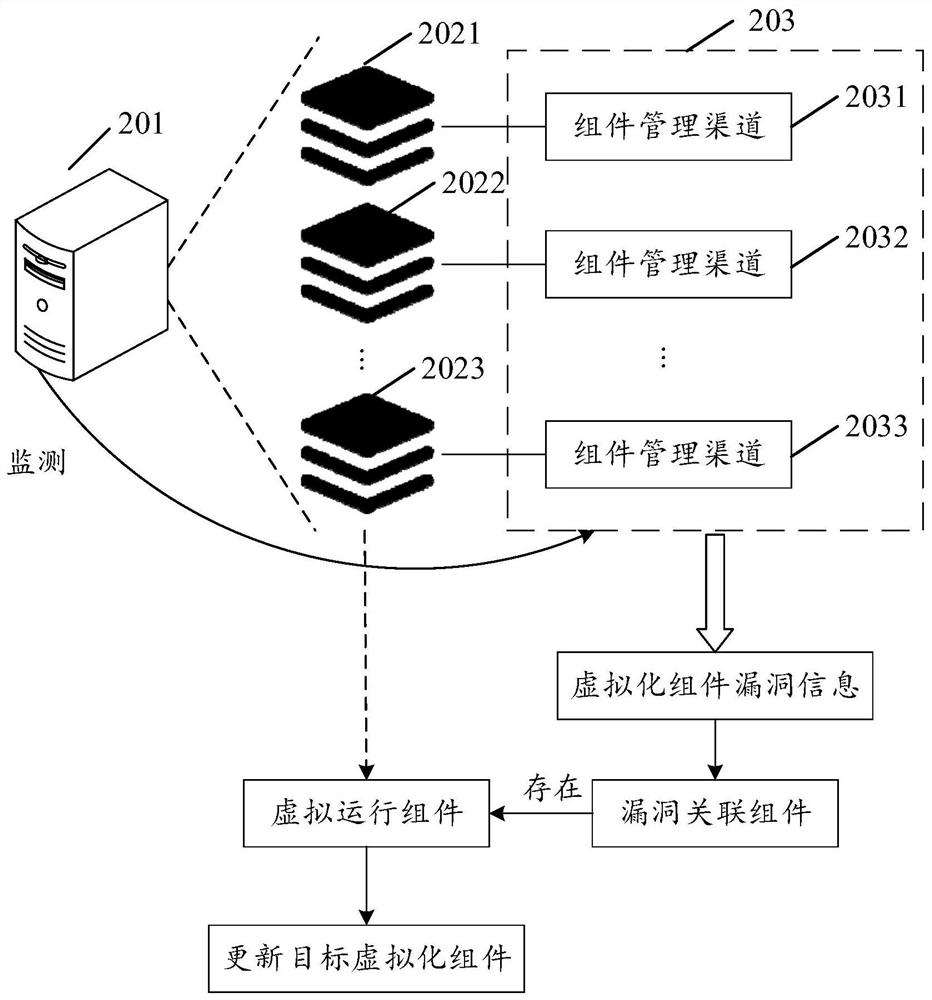
[0159] Specifically, see Figure 7 , Figure 7 It is a schematic diagram of a code function test scenario provided by an embodiment of the present application. like Figure 7 As shown, the host generates a code test case 702 according to the repair program code 701, runs the code test case 702, and performs a case test on the repair program code 701. If the use case test for the repair program code 701 passes, then the repair program code 701 Perform grayscale processing to obtain a grayscale test code 703 . The host computer updates the target virtualization component according to the grayscale test code 703 to obtain the grayscale virtualization component 704, and the grayscale virtualization component 704 is to be released. In 705, the computer device whose usage frequency of the virtual platform is less than the usage test threshold is determined as the test device 7051, and the grayscale virtualization component 704 is sent to the test device 7051 to be released, so th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com