Code injection detection method and device, electronic equipment and readable storage medium
A technology of code injection and detection method, which is applied in the field of code injection detection method, electronic equipment and readable storage medium, and device, which can solve problems such as easy bypass and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0082] To facilitate the understanding of this embodiment, a code injection detection method disclosed in the embodiment of the present application is firstly introduced in detail. Wherein, the method is applied to the server. figure 1 shows a flow chart of a code injection detection method provided by an embodiment of the present application, as shown in figure 1 shown, including the following steps:
[0083] S101: Obtain a specified field in the HTTP traffic generated when the client accesses the server, so as to use the specified field as a character string to be detected.
[0084] S102: Use the first decoding method to first decode the character string to be detected, and use the first decoding result as the first character string; the encoding method corresponding to the first decoding method is the first encoding method.
[0085] S103: Use the second decoding method to perform the second decoding on the first character string, and use the second decoding result as the ...
Embodiment 2
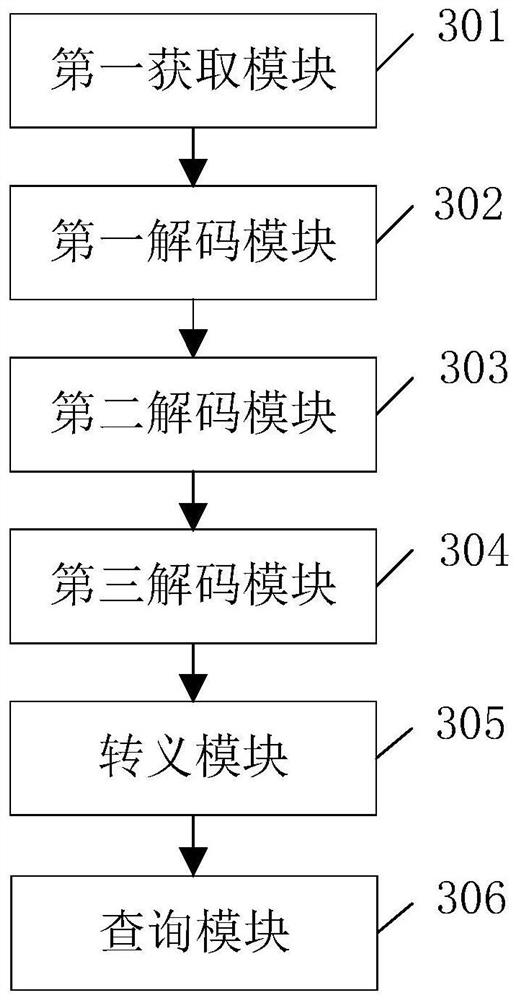
[0136] Based on the same technical concept, the embodiment of the present application also provides a code injection detection device, image 3 A schematic structural diagram of a code injection detection device provided by an embodiment of the present application is shown, as shown in image 3 As shown, the device includes:
[0137] The first obtaining module 301 is used to obtain the specified field in the HTTP flow generated when the client accesses the server, so as to use the specified field as a character string to be detected;
[0138] The first decoding module 302 is configured to use a first decoding method to first decode the character string to be detected, and use the first decoding result as the first character string; the encoding method corresponding to the first decoding method is the first encoding Way;
[0139] The second decoding module 303 is configured to use a second decoding method to perform a second decoding on the first character string, and use the s...
Embodiment 3
[0169] Based on the same technical concept, the embodiment of the present application also provides an electronic device, Figure 4 shows a schematic structural diagram of an electronic device provided by an embodiment of the present application, as shown in Figure 4 As shown, the electronic device 400 includes: a processor 401, a memory 402, and a bus 403. The memory stores machine-readable instructions executable by the processor. When the electronic device is running, the processor 401 communicates with the memory 402 through the bus 403. , the processor 401 executes machine-readable instructions to execute the method steps in Embodiment 1.
[0170] Refer to the description of Embodiment 1 for specific implementation method steps and principles, which will not be described in detail here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com