Authorization token generation method and third-party application association method
A technology of authorization token and target application, which is applied in the Internet field, can solve problems such as user information leakage, and achieve the effects of improving security, increasing the difficulty of decryption, and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
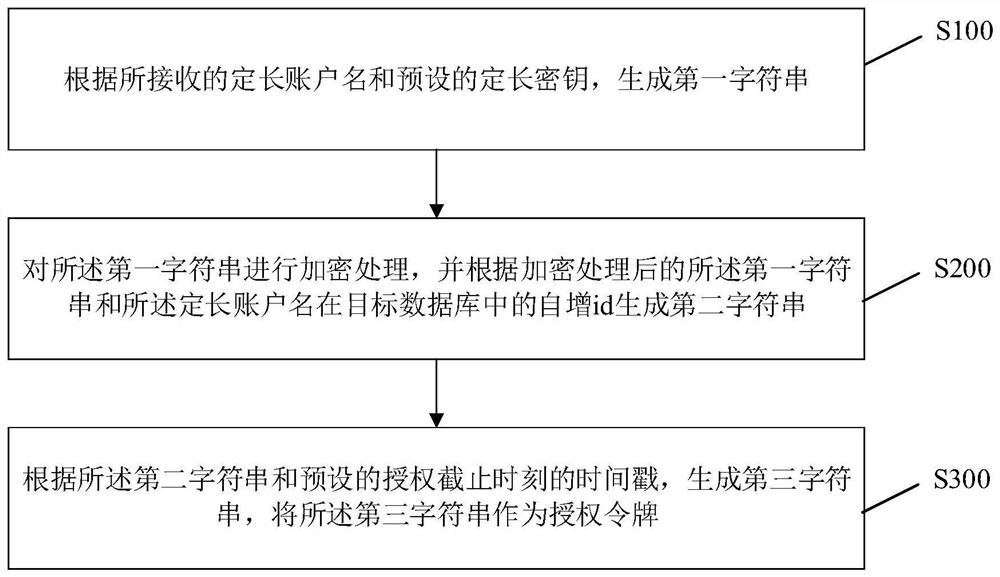
[0025] This embodiment provides a method for generating an authorization token, which is applied to a target application, figure 1 It is a flowchart of a method for generating an authorization token according to an exemplary embodiment of the present application. Such as figure 1 As shown, the method of this embodiment may include the following steps:
[0026] S100: Generate a first character string according to the received fixed-length account name and a preset fixed-length key.
[0027] S200: Encrypt the first character string, and generate a second character string according to the encrypted first character string and the self-incrementing id of the fixed-length account name in the target database.
[0028] S300: Generate a third character string according to the second character string and the preset time stamp of the authorization expiration time, and use the third character string as an authorization token.
[0029] Through the above steps, during the process of gene...
Embodiment 2
[0036] This embodiment provides a method for associating a third-party application, which is applied to a target application, and may include: responding to an authorization request sent by a third-party application, generating an authorization token by using the method for generating an authorization token as described above; The authorization token is sent to the third-party application to authorize the third-party application, so that the third-party application adds the authorization token to the service request sent.
[0037] After sending the authorization token to the third-party application, the method of this embodiment may further include: receiving a service request from the third-party application, wherein the service request includes the authorization token and the timestamp when the service request is generated; parsing the service request The authorization token in the request obtains the time stamp of the preset authorization deadline and the encrypted first cha...
Embodiment 3
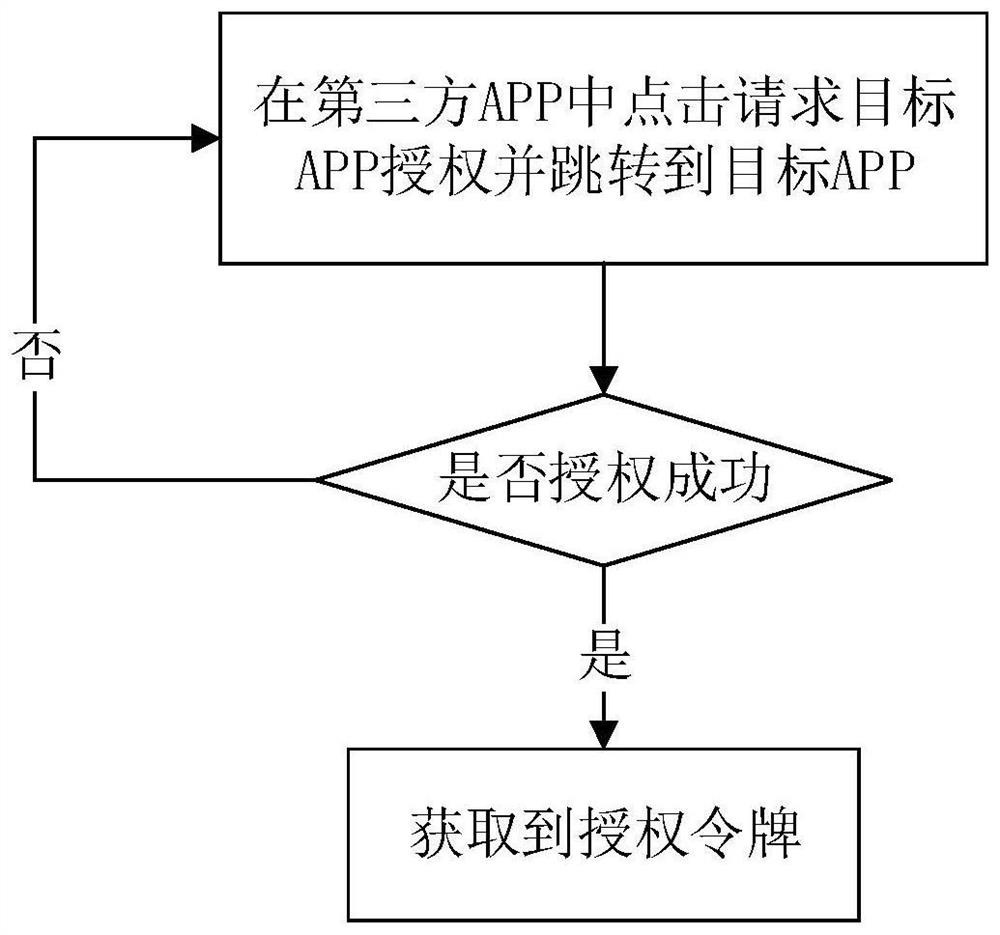
[0041] This embodiment provides a specific embodiment of a method for associating a third-party application. Such as figure 2 As shown, on the APP side, the user first registers and logs in to the account, and sets a fixed-length account name and a fixed-length custom key through this APP. When a third-party APP requires the authorization of this APP, the user can click on the third-party APP to request the authorization of the target APP, and then jump to the target APP. If the authorization is successful, the third-party APP obtains an authorization token.
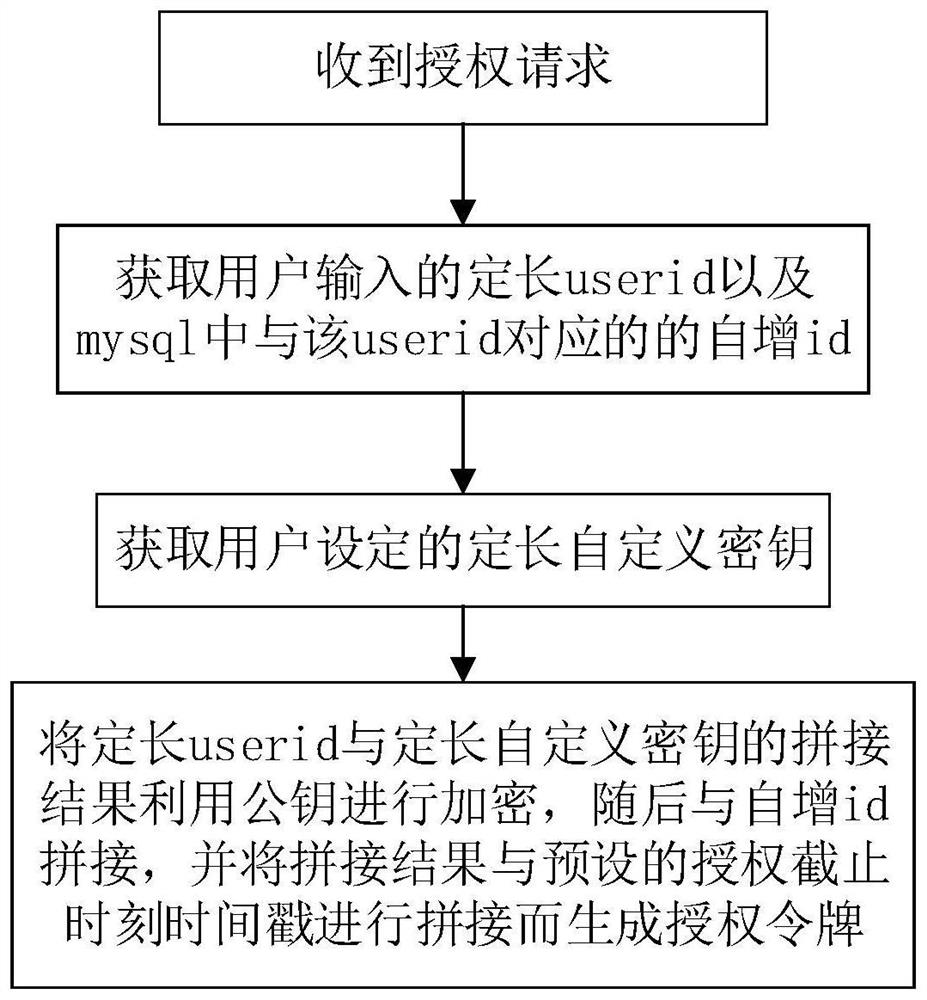
[0042] Such as image 3As shown, when this APP receives an authorization request from a third-party APP, it obtains the fixed-length userid entered by the user when registering and the corresponding self-incrementing id of the userid in mysql from the database, and at the same time obtains the fixed-length self-incrementing id entered by the user. Define the key. Splice the fixed-length userid with the fixed-length ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com