Encryption and decryption method and device for numerical value and storage medium
An encryption method and numerical technology, applied in the field of computing applications, can solve the problems of inability to accurately restore data tables, undetectable values, leakage of sensitive data, etc., and achieve the effect of avoiding random modification of data, occupying less memory, and wide applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0090] According to this embodiment, an embodiment of an encryption and decryption method for numerical values is provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
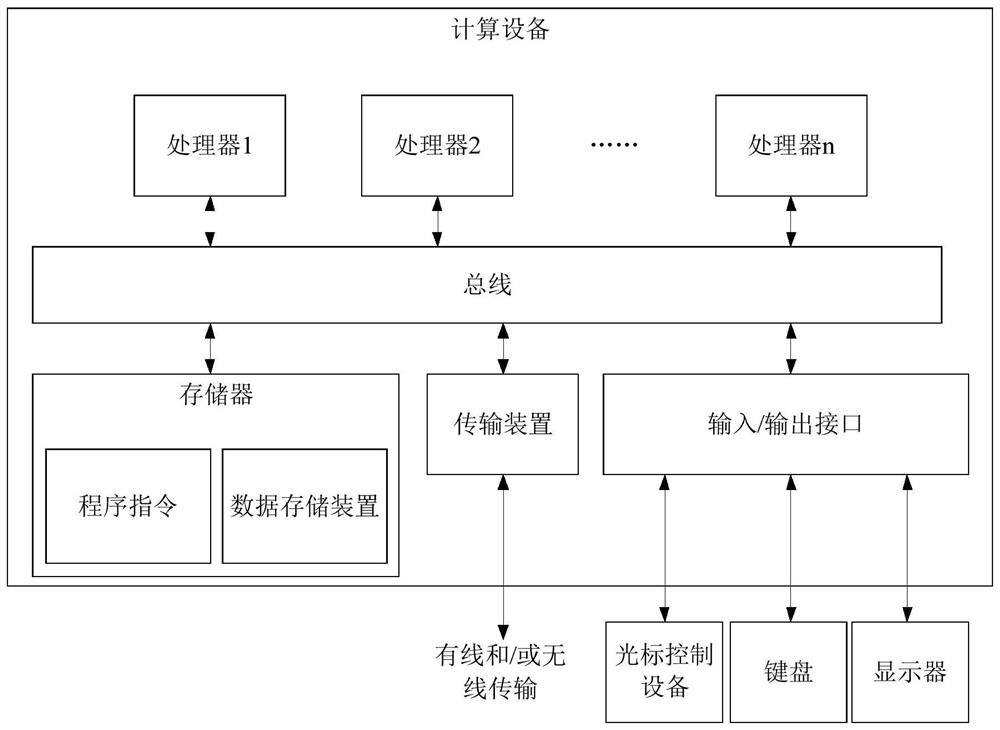
[0091] The method embodiments provided in this embodiment can be executed in mobile terminals, computer terminals, servers or similar computing devices. figure 1 A block diagram of a hardware structure of a computing device for an encryption and decryption method for numerical values is shown. like figure 1 As shown, the computing device may include one or more processors (processors may include but not limited to processing devices such as microprocessors MCUs or programmable logic devices FPGAs), memo...
Embodiment 2
[0134] Figure 15 Shown is the encryption device 500 for numerical values according to the first aspect of this embodiment, which corresponds to the method according to the first aspect of Embodiment 1. refer to Figure 15 As shown, the device 500 includes:
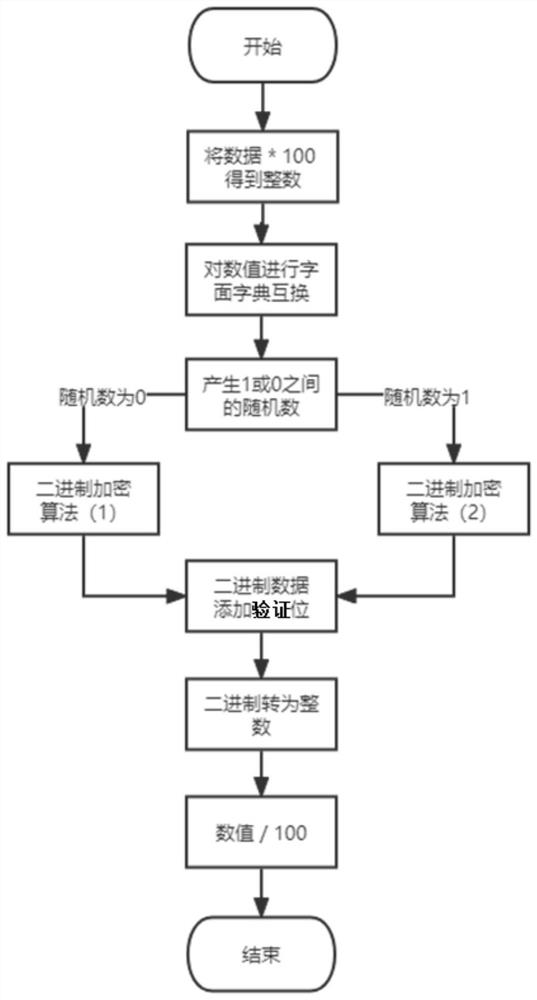
[0135] A binary conversion module 510, configured to multiply the data to be encrypted by 10 to the M power to obtain a first integer value, perform literal dictionary exchange on the first integer value, and convert the first integer value after the literal dictionary exchange is the first binary data, M is 0 or a natural number;
[0136] An encryption processing module 520, configured to generate a random number 0 or 1, and perform binary encryption processing on the first binary data according to the random number to obtain second binary data;
[0137] A verification bit and algorithm bit adding module 530, configured to add a verification bit and an algorithm bit to the right side of the second binary data;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com