A scheduling method and system for website security protection capabilities based on workflow
A technology of security protection capability and scheduling method, applied in transmission systems, digital transmission systems, security communication devices, etc., can solve problems such as low matching efficiency, disordered scheduling, website security monitoring hanging horses, etc., and achieve high-speed security. The effect of attacking, improving query efficiency, and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In the following description, numerous specific details are given in order to provide a more thorough understanding of the present invention. It will be apparent, however, to one skilled in the art that the present invention may be practiced without one or more of these details. In other examples, some technical features known in the art are not described in order to avoid confusion with the present invention.
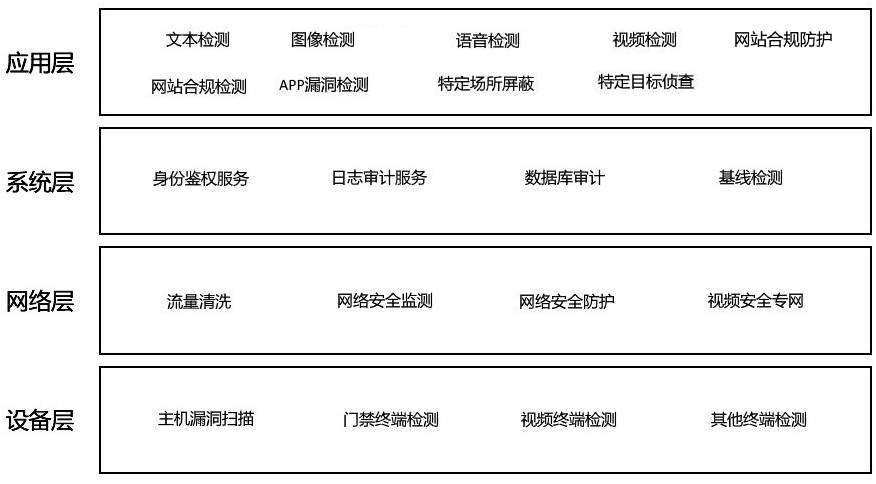
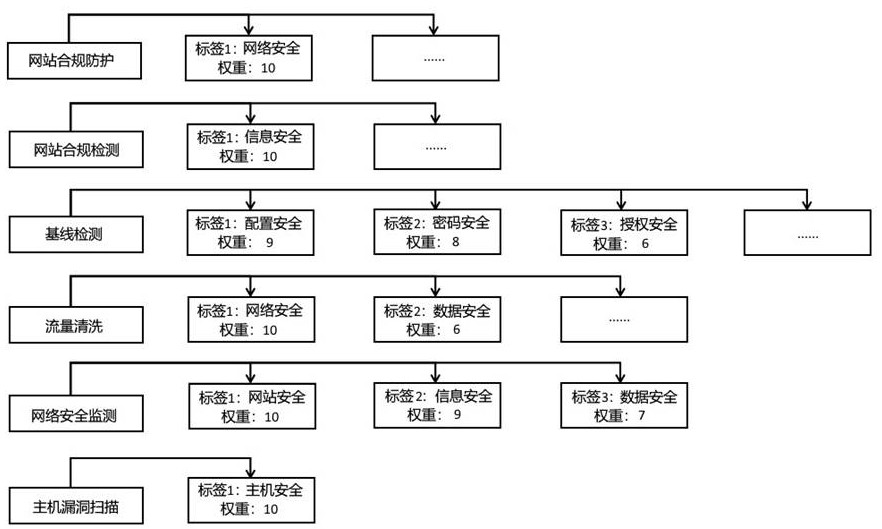
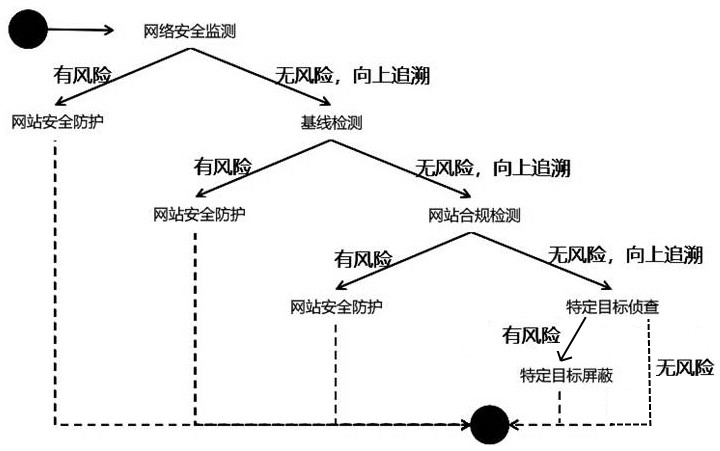
[0033] The present application discloses a website security protection capability scheduling method that automatically schedules security resource capabilities, can quickly and efficiently retrieve threats, effectively schedules security resource capabilities by classification and hierarchy, shares data, and can estimate potential risks.
[0034] The scheduling method includes: S1. The access registration module collects security resource pool capabilities.
[0035] S2. The hierarchical management module reads the security resource pool capability information o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com