Intranet equipment connection method and system based on SSH reverse tunnel
A device connection and tunnel connection technology, applied in the computer field, can solve the problems of limiting the maximum number of connections and occupying multiple ports of the bastion machine, so as to prevent scanning and attacks and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
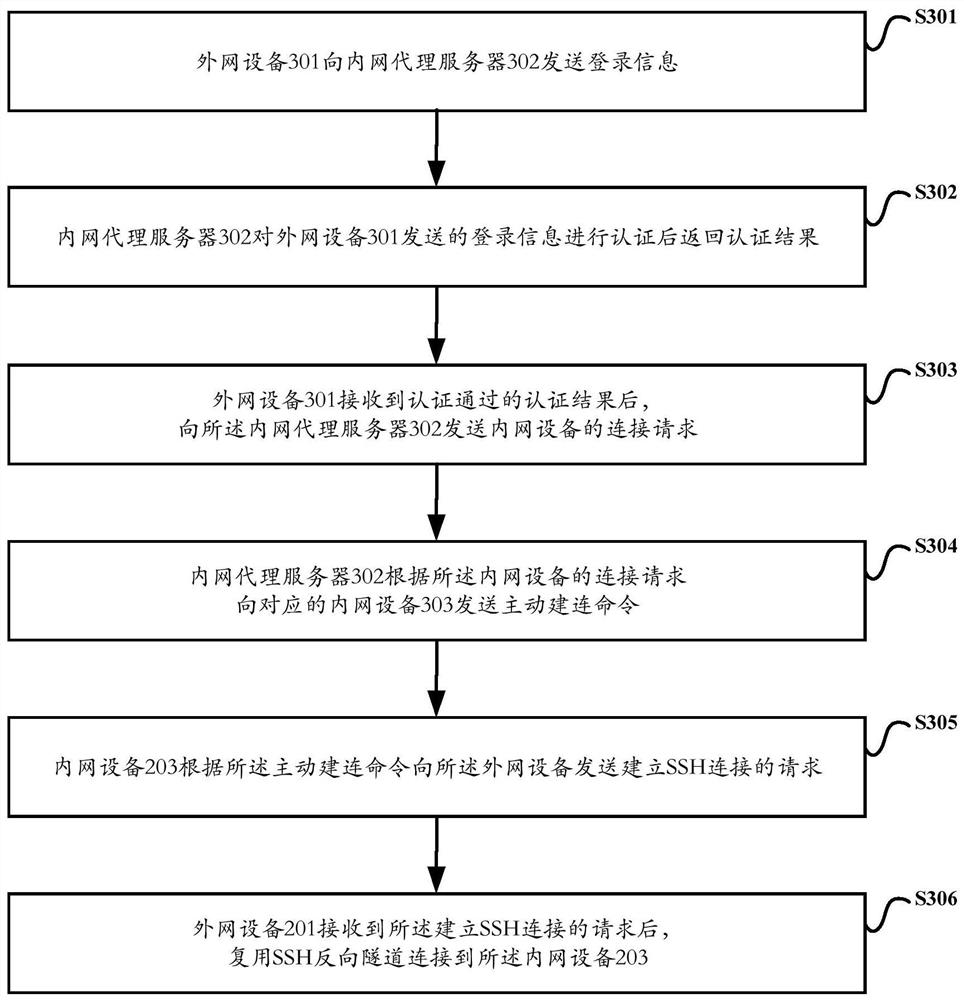
[0073] image 3 A specific flow chart of a method for connecting an intranet device based on an SSH reverse tunnel according to Embodiment 1 of the present application is schematically shown.
[0074] like image 3 As shown, the SSH reverse tunnel-based intranet device connection method may include the following steps S301-S306, wherein:
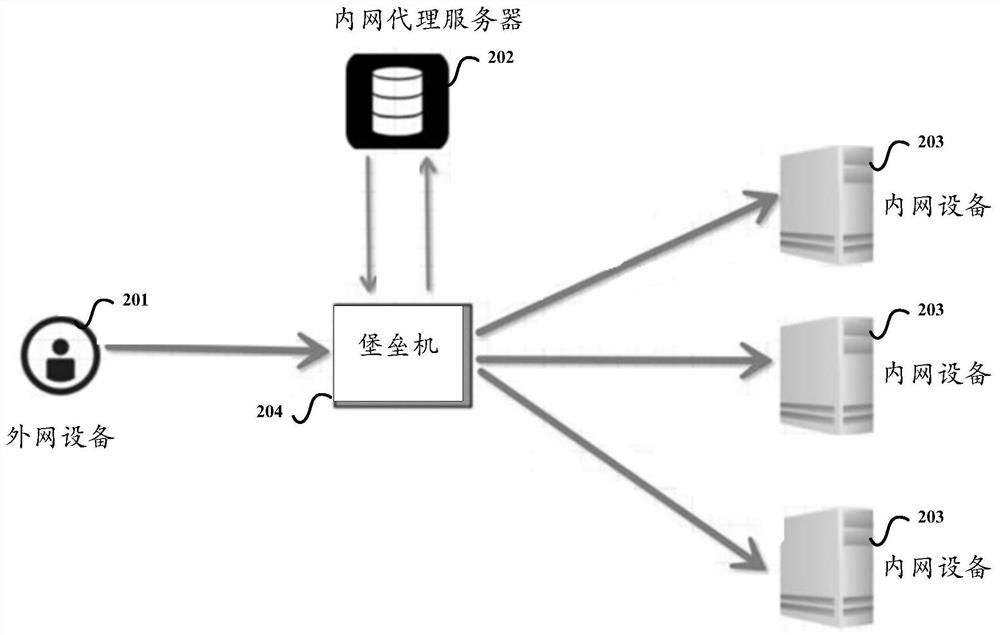
[0075] Step S301: the external network device 201 sends login information to the internal network proxy server 202.
[0076] Specifically, a proprietary client is installed in the external network device 201; the main functions of the proprietary client include: installing the SSH client and authentication part logic locally on the machine to ensure the normal implementation of the functions; in addition, the proprietary client uses the client-specific There is an agreement to use two-factor authentication when logging in to the intranet proxy server 202, that is, the authentication method of account password + dynamic password. Among the...
Embodiment 2
[0120] Figure 4 Schematically shows a block diagram of an external network device according to Embodiment 2 of the present application. The external network device can be divided into one or more program modules, and one or more program modules are stored in a storage medium and controlled by one or more Executed by multiple processors to complete the embodiment of the present application. The program modules referred to in the embodiments of the present application refer to a series of computer program instruction segments capable of accomplishing specific functions. The following description will specifically introduce the functions of the program modules in the embodiments of the present application.
[0121] like Figure 4 As shown, an internal structure of the above-mentioned external network device 201 may include the following modules: an internal network device connection request sending module 401, an SSH tunnel module 402;
[0122] Wherein, the intranet device con...
Embodiment 3
[0128] Figure 5 Schematically shows a block diagram of an intranet proxy server according to Embodiment 3 of the present application, the intranet proxy server can be divided into one or more program modules, one or more program modules are stored in a storage medium, and Executed by one or more processors to complete the embodiments of the present application. The program modules referred to in the embodiments of the present application refer to a series of computer program instruction segments capable of accomplishing specific functions. The following description will specifically introduce the functions of the program modules in the embodiments of the present application.
[0129] like Figure 5 As shown, an internal structure of the aforementioned intranet proxy server 202 may include: an intranet device connection request receiving module 501 , and an active connection establishment command sending module 502 .
[0130] The internal network device connection request re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com