Vulnerability detection method and system based on self-supervised learning and multi-channel hypergraph neural network
A neural network and vulnerability detection technology, applied in the direction of neural learning methods, biological neural network models, neural architectures, etc., can solve the problems of poor detection of loopholes and insufficient use of high-order relationships in codes, so as to achieve clean data stream information, The effect of low false alarm rate and reduced time overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
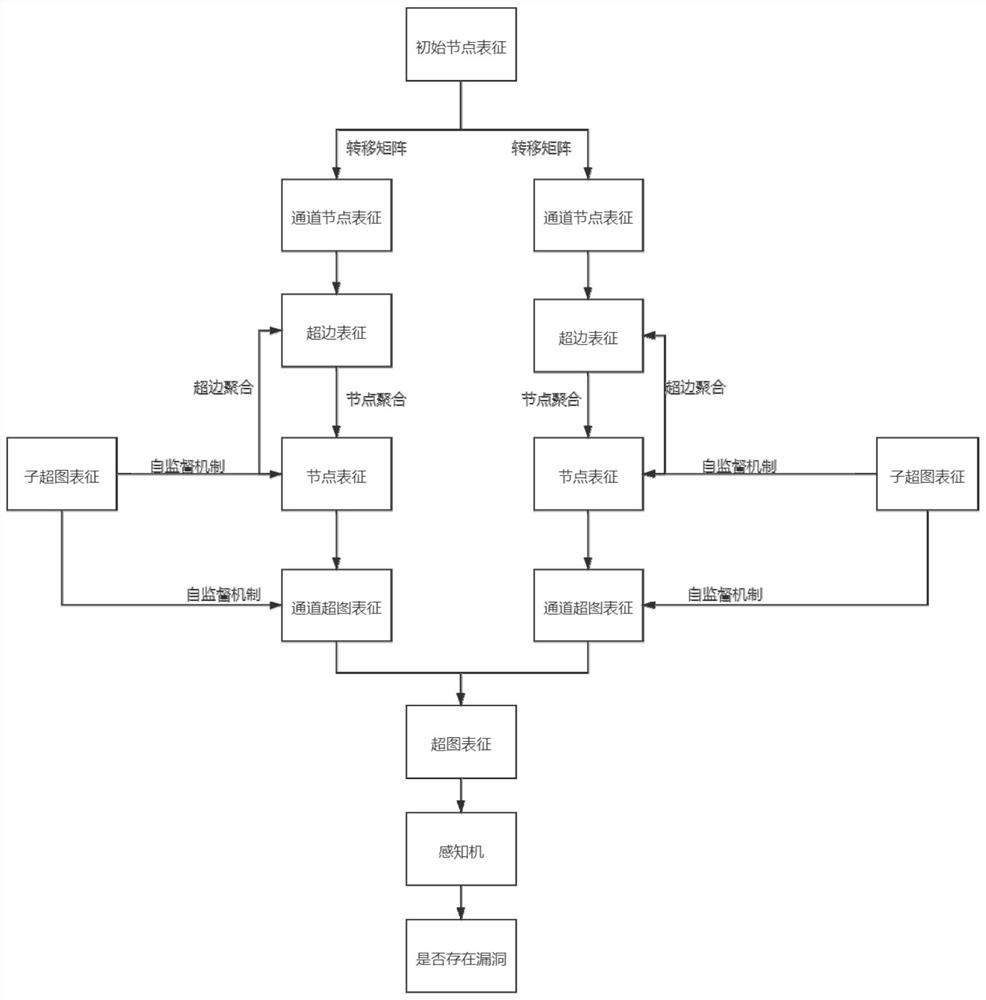
[0103] The specific process of this embodiment is as follows:
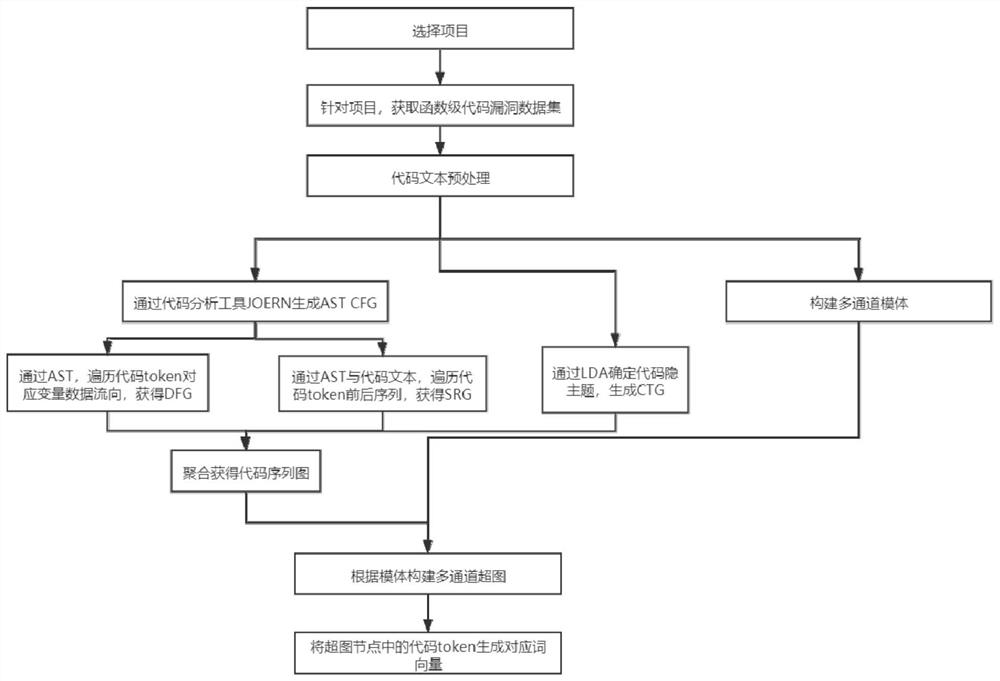
[0104] First, select the code dataset QEMU and FFmpeg:
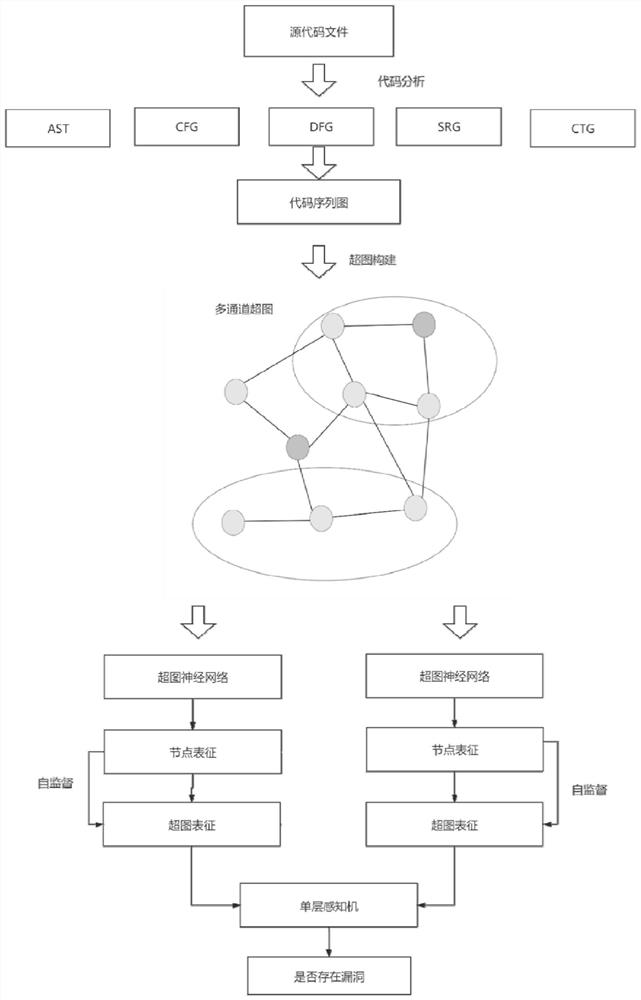
[0105] For the selected code data, the following describes how to convert the code text, such as figure 2 shown:
[0106] (1) Preprocess the code to remove links, special characters, etc. in the code.
[0107] (2) Standardize the code variable names.
[0108] (3) Using the compiler tool Joern to generate abstract syntax tree (AST graph) and control flow graph (CFG graph) of function code.
[0109] (4) Then traverse the token sequence of the leaf nodes in the AST, obtain the data transfer relationship between the code tokens, and generate a data flow graph (DFG graph).
[0110] (5) Then traverse the token sequences in the leaf nodes in the AST, match with the code text, and generate a sequence relationship diagram (SRG diagram) representing the sequence relationship between the code tokens before and after.
[0111] (6) Then, according to the Linear Di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com