Hybrid resource configuration method for fog computing Internet-of-Things physical layer security
A technology for physical layer security and resource allocation, applied in the field of mixed resource allocation, which can solve problems such as discussion, less failure to allocate mixed security resources, and complex implementation of high-level fog computing security policies.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
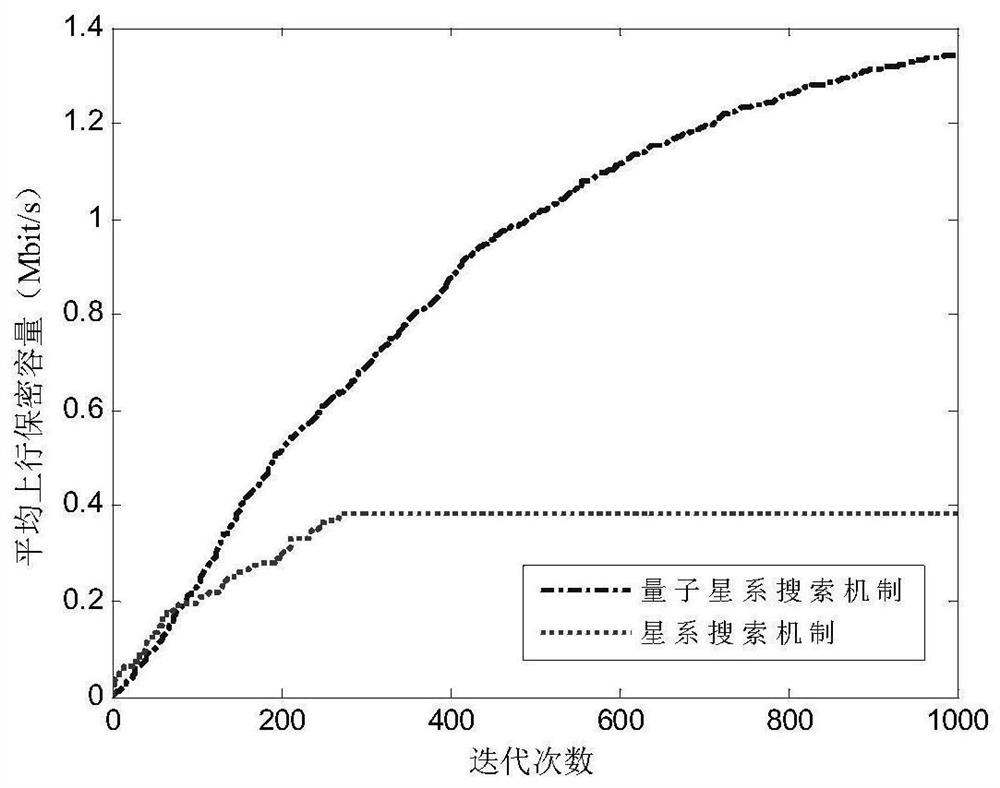
[0042] The present invention will be further described below in conjunction with accompanying drawing, as figure 1 As shown, the hybrid resource configuration method designed by the present invention for the security of the fog computing Internet of Things physical layer includes the following steps:
[0043] Step 1: Establish a secure fog computing IoT system model
[0044] Consider a fog computing IoT system with K fog nodes, D IoT users, and L passive bugs. use Represents the data task of each IoT user with time-delay requirements, where S d Indicates the size of the data task, C d Indicates the CPU cycles required to process data tasks, is the maximum allowable delay threshold. There are W spectrum resource blocks orthogonal to each other in the network, each IoT user occupies a spectrum resource block and transmits the data task to the corresponding fog node allocated by the cloud service provider, using χ d,k ∈{0,1} indicates whether the data task of the dth IoT ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com