Combined fingerprint password system and operation method
A fingerprint password and system operation technology, which is applied in the field of fingerprint password, can solve problems such as low security performance, loss of property of the lock owner, singleness, etc., and achieve the effect of improving security performance, improving security and diversity, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
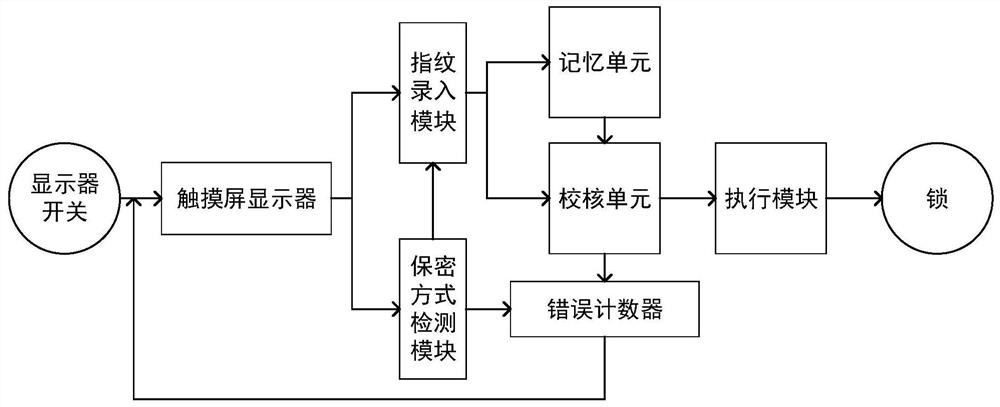
[0040] Such as figure 1 As shown, a combined fingerprint encryption system in this embodiment includes: a touch screen display, a fingerprint input module, an encryption method detection module, a memory module, a verification module, an execution module and a lock;
[0041] The touch screen display is used for touch recognition to feed back the operation instructions issued by the user to the fingerprint entry module and the encryption method detection module, and at the same time display the system status and guide the user to perform various operations; it is used to identify the number of fingerprints and the sequence of fingerprints, and send the data Feedback to the encryption mode detection module. The user can choose whether to unlock, enter fingerprints, enter fingerprints, return to the main interface and select encryption methods on the touch screen display.
[0042] The fingerprint entry module, when the user enters the fingerprint, recognizes the entered fingerpr...
Embodiment 2
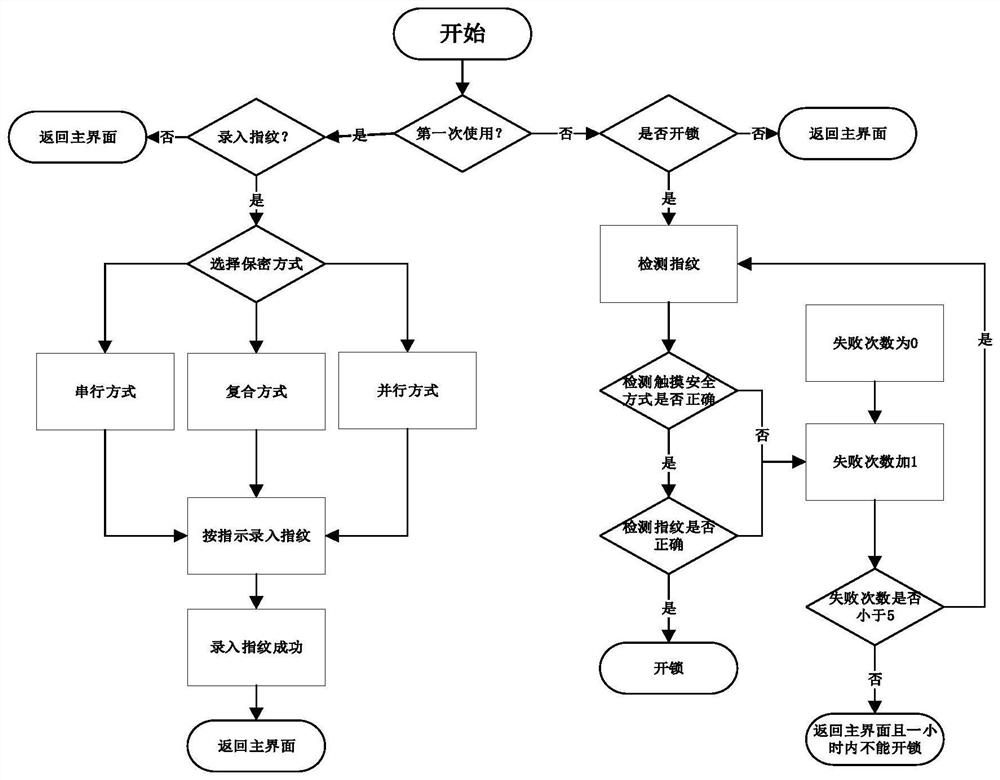
[0050] Such as figure 2 As shown, a method of operating a combined fingerprint cryptosystem in this embodiment includes the following steps:
[0051] Step 1. Turn on the display switch to enter the main interface, judge whether it is the first use, if it is the first use, enter step 2, if it is not the first use, skip to step 6;
[0052] Step 2. Determine whether fingerprints need to be registered. If fingerprints need to be registered, enter step 3. If fingerprints do not need to be registered, return to the main interface;
[0053] Step 3. Select the encryption method on the touch screen display;
[0054] In the embodiment of the present invention, the encryption method in step 3 is a serial method, a parallel method or a composite method.
[0055] According to the prompts in the system prompts, the user can independently select the required encryption method from the three encryption methods on the touch screen.
[0056] In the embodiment of the present invention, the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com