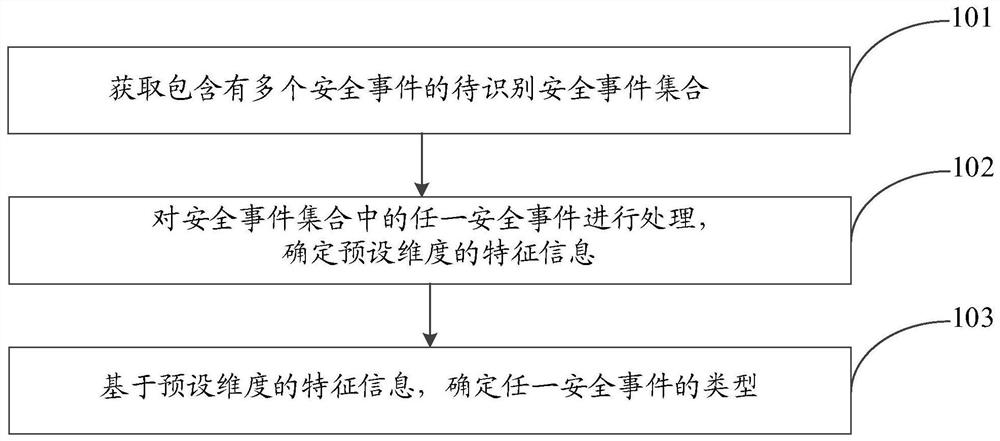
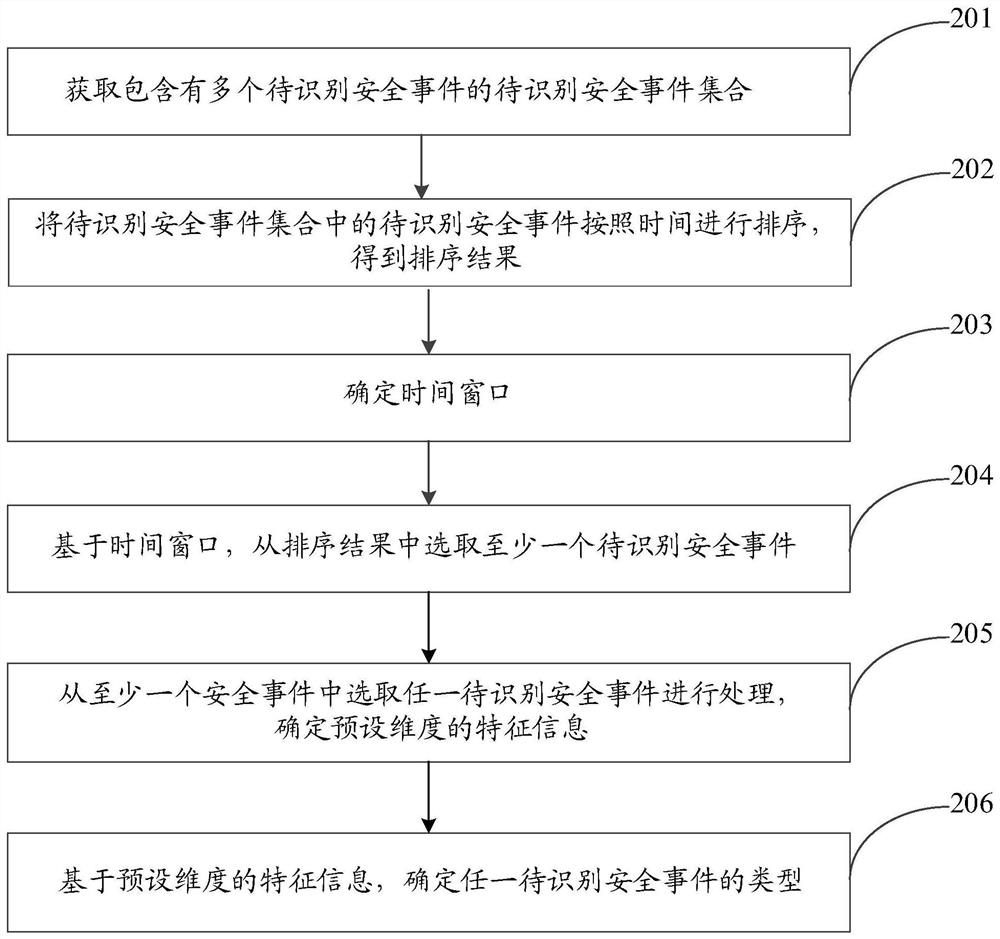
Security event type determination method, device and system and storage medium
A security event and determination method technology, applied in the information field, can solve problems such as security threats of network equipment terminal equipment, missed detection and reporting of security events, etc., to reduce the probability of missed detection and reporting of security events, improve accuracy, and determine the method flexible effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
[0065] It should be understood that the specific embodiments described here are only used to explain the embodiments of the present invention, and are not intended to limit the embodiments of the present invention.
[0066] The embodiments of the present invention relate to the field of information technology, and in particular, to a method, device, system, and computer-readable storage medium for determining a security event type.
[0067] Among related technologies, the mainstream threat intelligence technology mainly identifies security events by identifying IOCs including files, Uniform Resource Locators (Uniform Resource Locators, URLs), Internet Protocol (Internet Protocol, IP) addresses, and md5. Traces of the activity of the attacking organization are included in the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com