A Method for Discovering Vulnerabilities of Operating System Access Control Based on Model Checking
A technology of access control and operating system, applied in platform integrity maintenance, instrumentation, computing, etc., can solve problems such as lack of applications, difficulty in ensuring security policy determinism, and high level of abstraction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
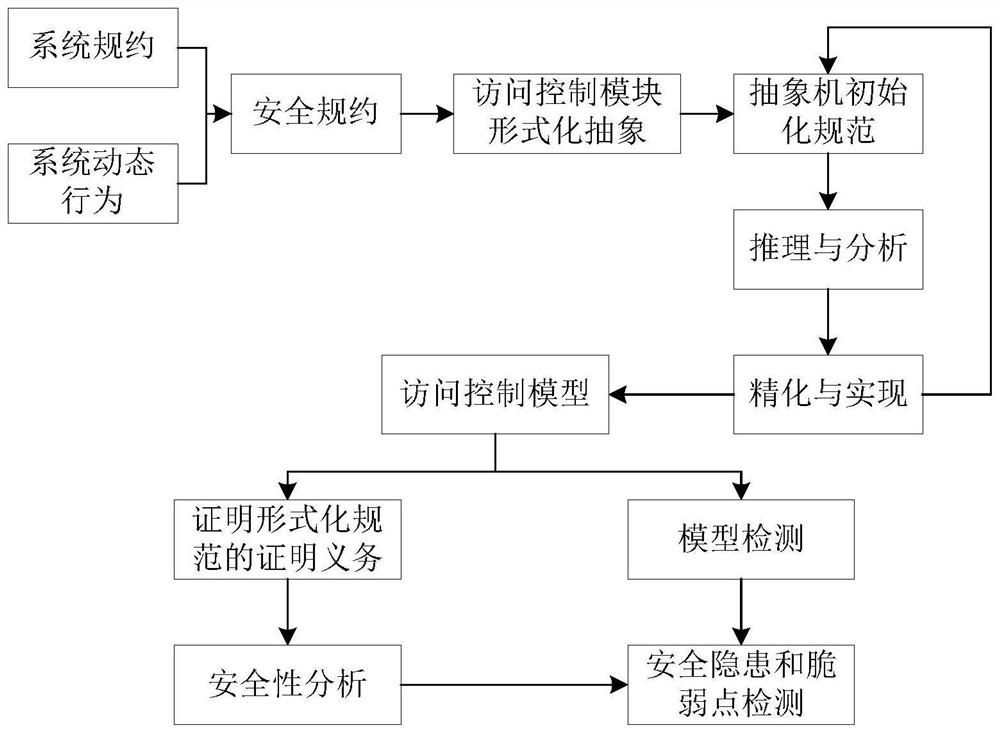
[0022] Step 1: Analyze the operating system access control security requirements, define access control rules and security attributes, and describe the security attribute specification conditions by analyzing the system specification and system dynamic behavior, and give a strictly defined security specification including form and semantics to achieve Describe the specification of the operating system access control mechanism at a higher level; security attributes are used to formally describe security rules, as one of the implementation methods, it includes atomic security attributes and resource security attributes, atomic security attributes include permission definition, access Location, user type; resource security attributes include subject security attributes and object security attributes.
[0023] Step 2: Formally abstract the access control module of the operating system, define the basic abstract machine and its elements, analyze and reason the formal specification, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com