Safe and effective cloud data integrity verification scheme with privacy protection
An integrity verification and privacy protection technology, which is applied in the field of cloud data integrity verification solutions with privacy protection, can solve the problems of security, privacy and low efficiency, reduce communication complexity and calculation complexity, and ensure privacy performance, the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
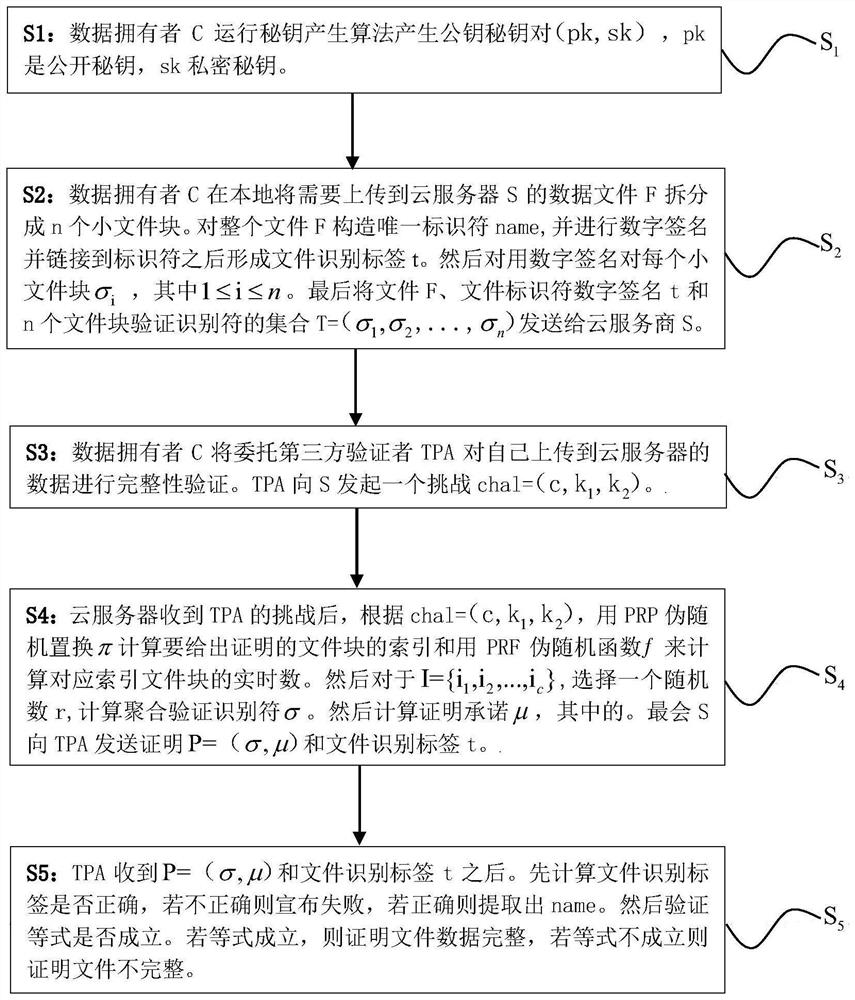
[0017] In order to make the purpose, solutions and effects of the embodiments of the present invention more clear and definite, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
[0018] The specific implementation steps of the present invention are as follows:
[0019] S1: The data owner C runs the secret key generation algorithm: selects the corresponding security parameter κ according to the needs of the data owner to reach the required security level. In this embodiment, the security parameter κ=80bits is taken, and then a large prime number p=2κ=160bits is taken to form a group Z p , select a group G with Weil pairing (bilinear mapping) of order p. Then we use the hash function SHA256 to construct the hash function H mapped to the group G: {0, 1} * →G. The pseudo-random permutation PRP adopts AES, and the pseudo-random function PRF also adopts AES construction. In group Z p A number x is randomly...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com