A High Security Transmission Method Based on Double Encryption of Three-Dimensional Constellation
A double encryption, secure transmission technology, applied in the field of communication, can solve the problems of rarely considering three-dimensional or even higher dimensions, and the encryption method is not flexible enough, and achieve the effect of improving transmission capacity, high gain index, and improving security performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
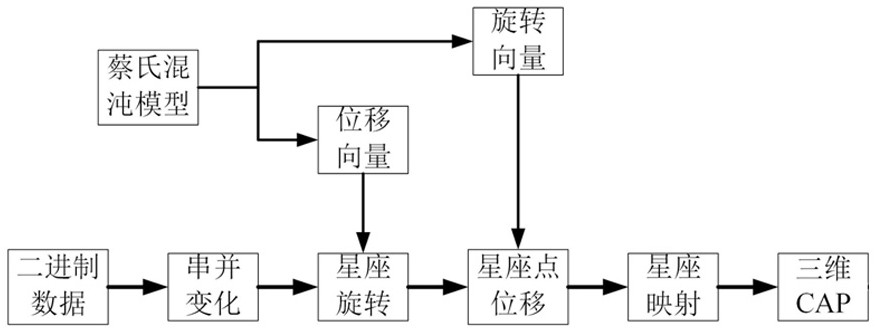
[0026] A high-security transmission method based on three-dimensional constellation double encryption described in this embodiment, the flow chart is as follows figure 1 shown, including the following steps:
[0027] (1) Serial-to-parallel conversion is performed on the binary data at the transmitter, and the one-dimensional data stream is converted into three-dimensional data for transmission.
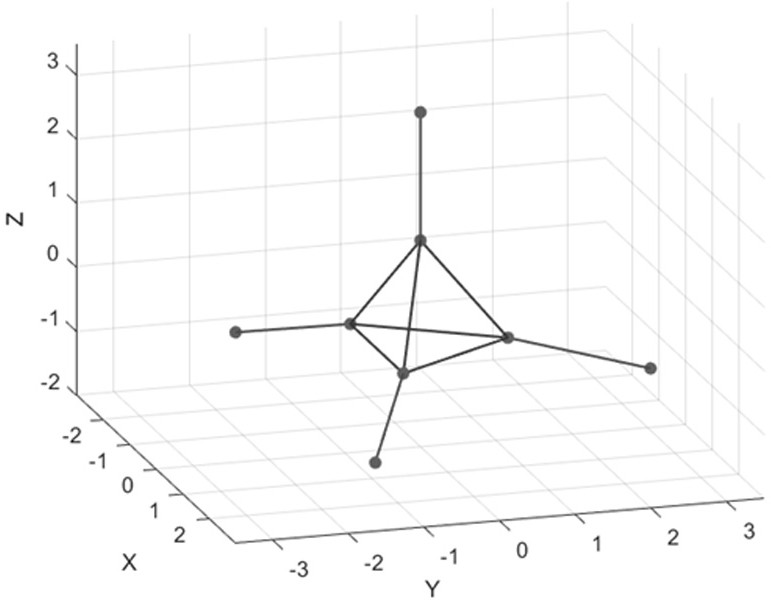
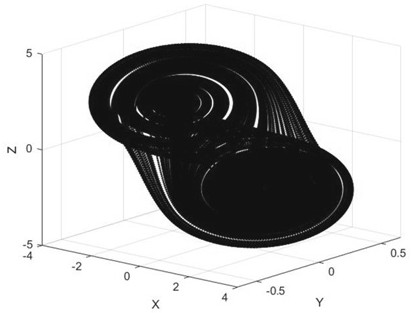
[0028] (2) Constellation mapping is performed on the 3D data, and the original data flow is mapped to the 3D constellation diagram to form constellation points. The model of the 3D constellation diagram is as follows: figure 2 As shown, the number of constellation points in the figure is 8, and one constellation point in the bit stream corresponds to three bits. The constellation gain index of the three-dimensional constellation diagram is:
[0029]
[0030] Among them, d min (C) represents the minimum Euclidean distance in the constellation diagram, and P(C) represents the ave...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com