Double-link wireless ad hoc network and security defense method in emergency scene
A wireless ad hoc network and security defense technology, applied in the field of network security, can solve problems affecting normal communication, nodes being invaded, and alarm response information not arriving in time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
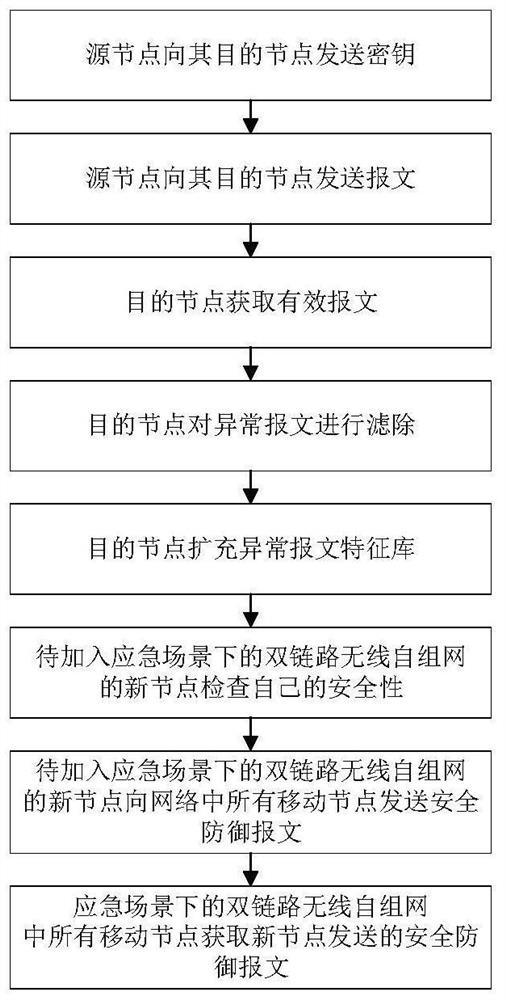
[0057] Below in conjunction with accompanying drawing and specific embodiment, the present invention is described in further detail:
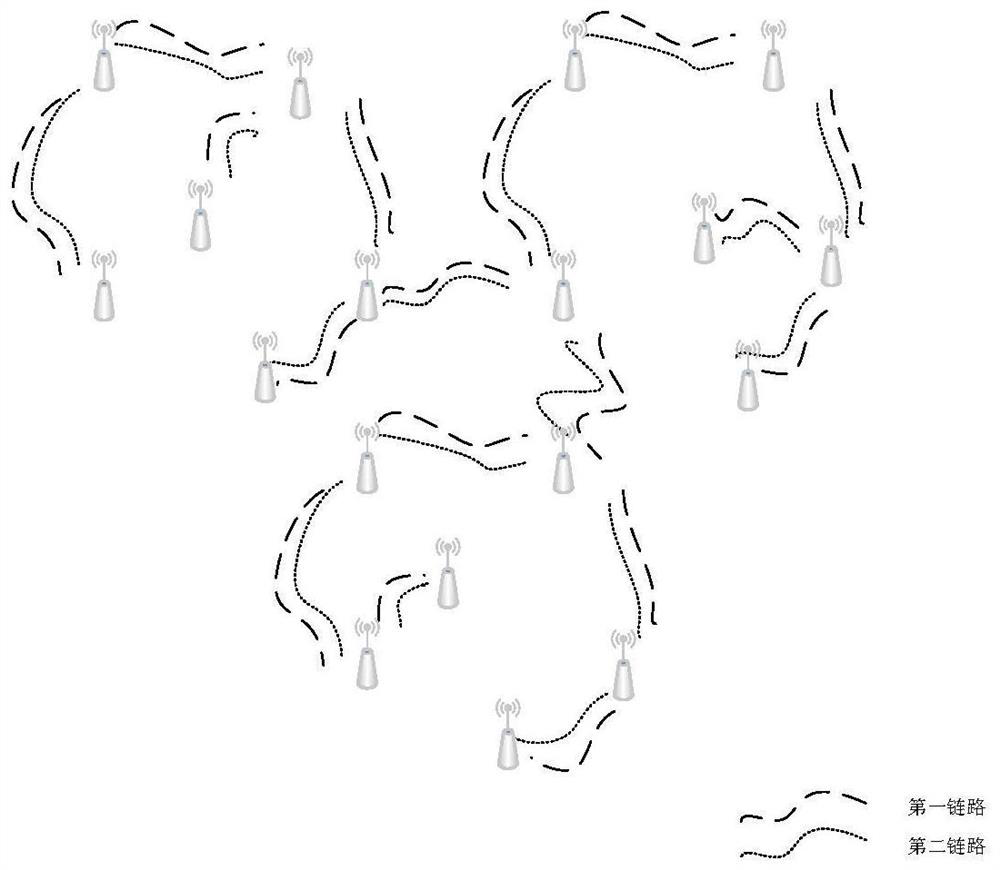
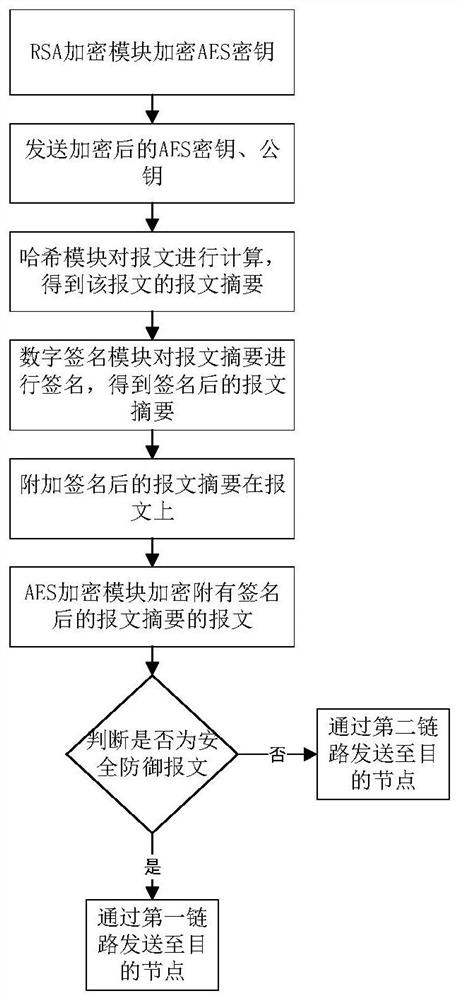
[0058] refer to figure 1 , the dual-link wireless ad hoc network in the emergency scenario includes: including M mobile nodes N={n 1 ,n 2 ,...,n i ,...,n M}, M≥3, where n i Indicates the i-th mobile node, 1≤i≤M, in this embodiment, M=18, each mobile node serves as both a source node and a destination node of other mobile nodes, and an intermediate node between two mobile nodes , a first link for transmitting security defense messages and a second link for transmitting other messages, public keys and encrypted AES keys not belonging to security defense messages are set between any two mobile nodes;
[0059] The first link is set to be independent of the second link, and the two parties do not affect each other, and transmit their respective information independently. At the same time, because only security defense messages are transmitted o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com