Authentication method and device and storage medium
An authentication method and authentication request technology, applied in the field of security, can solve problems such as reducing the overhead of synchronization requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
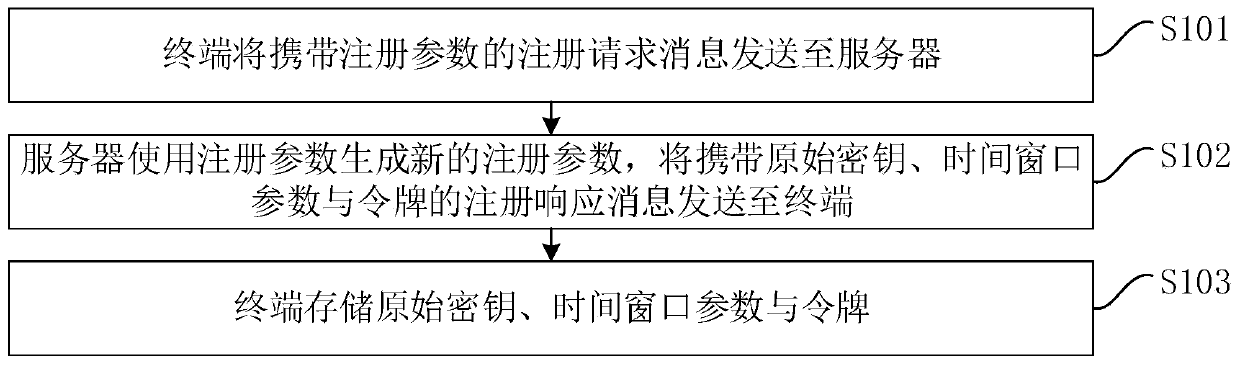
[0074] figure 1 It is a flowchart of an authentication method provided by Embodiment 1 of the present invention. This embodiment is applicable to the case where the server registers the terminal based on the time window (TimeWindow) in the stateless mode. The so-called stateless mode may refer to the server The relevant data of user authentication is not persistently stored, and the method can be performed by a computer device, and the computer device (terminal and server) can be implemented by software and / or hardware, wherein the terminal can include a mobile terminal (such as a mobile phone, a tablet computer) etc.), wearable devices (such as smart watches, etc.), etc., the method specifically includes the following steps:
[0075] S101. The terminal sends a registration request message carrying registration parameters to the server.
[0076] In this embodiment, when the user registers, the terminal assembles the registration parameters into a registration request message ...
Embodiment 2
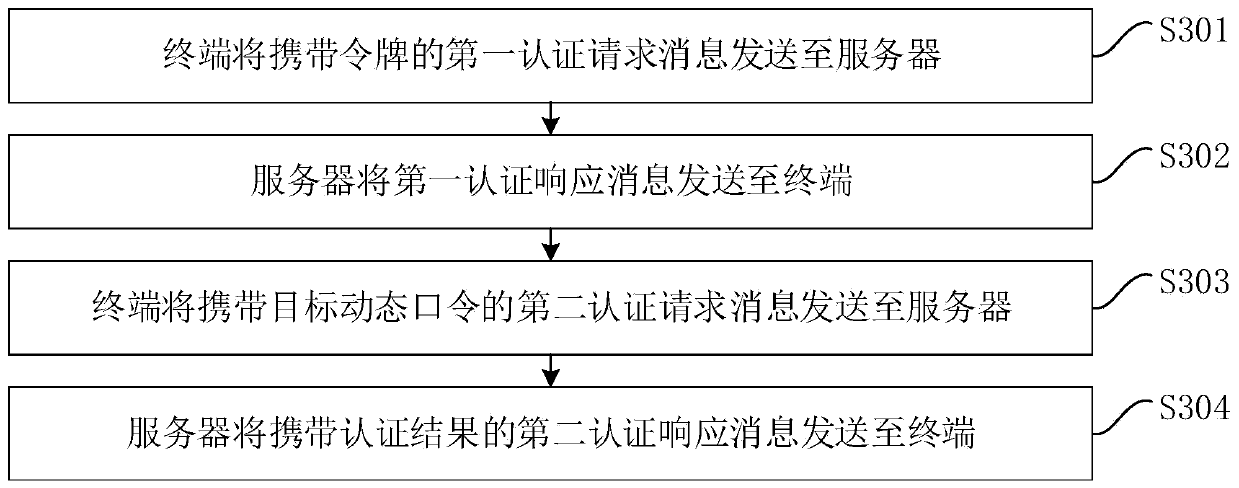
[0103] image 3 It is a flowchart of an authentication method provided by Embodiment 2 of the present invention. This embodiment is based on the foregoing embodiments, and further adds processing operations for the server to authenticate the terminal based on the time window in the stateless mode. The method specifically includes Follow the steps below:
[0104] S301. The terminal sends a first authentication request message carrying a token to a server.
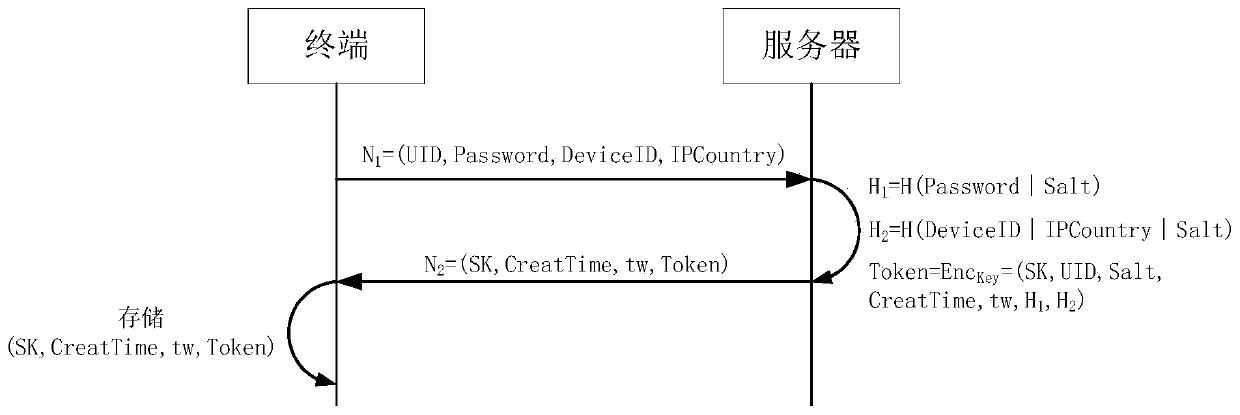
[0105] In this example, if Figure 4 As shown, when the terminal registers with the server, it stores the original key SK, time window parameters, and token Token, and the server does not persist the original key SK, time window parameters, and token Token. , the terminal extracts the Token stored locally, and sends it to the server through the first authentication request message.
[0106] In one embodiment, as Figure 4 As shown, the terminal extracts the local token Token and the user identification UID of the termina...
Embodiment 3
[0171] Figure 5 It is a flowchart of an authentication method provided by Embodiment 3 of the present invention. This embodiment is applicable to the situation where the server registers and authenticates the terminal based on the time window in the stateless mode. This method can be executed by a computer device. The computer device can be implemented as a terminal, and the terminal stores the original key, time window parameters and tokens when registering with the server, and the terminal can be implemented by software and / or hardware, wherein the terminal can include a mobile terminal (such as a mobile phone, a tablet computer) etc.), wearable devices (such as smart watches, etc.), etc., the method specifically includes the following steps:
[0172] S501. Send the first authentication request message carrying the token to the server.
[0173] In a specific implementation, the server is used to decrypt the token into the original key, time window parameters and registrati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com