Hex file processing method and application
A file processing and file technology, applied in the field of Hex file processing, can solve problems such as program cracking or rewriting, and achieve the effect of consistent format and length, low memory requirements, and accurate control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
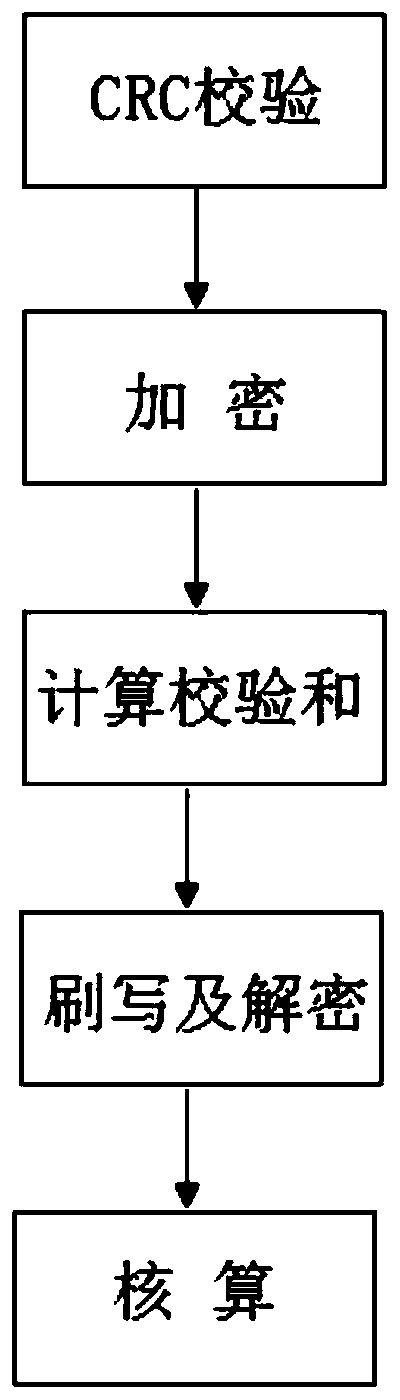
[0037] Process the Hex file that needs to be flashed in the car TCU, specifically:
[0038] Step 1, perform CRC32 check on every 4 Blocks of the Hex file, get the corresponding CRC32 check code, put it into the specified address position according to the Intel format, that is, the reverse order of placing the most significant bit on the high address;
[0039] Step 2, perform AES128 encryption on the data field in each Record, keep the data length field, load address field, data type field, checksum field, etc., and set the corresponding decryption program in the TCU internal startup program;
[0040] Step 3, recalculate the checksum of each encrypted Record;
[0041] Step 4, write the Hex file processed in steps 1 to 3 to the TCU, and start the program inside the TCU to decrypt it;
[0042] Step 5: The TCU calculates the CRC32 check code. If they are consistent, the data in the Hex file is correct and stored in the TCU memory; otherwise, the data in the Hex file is incorrect ...
Embodiment 2
[0044] Process the Hex file that needs to be flashed in the car TCU, specifically:
[0045] Step 1, perform byte padding on each Record in the Hex file, so that the format and length of each Record are consistent, which is convenient for subsequent data processing;
[0046] Step 2, perform CRC32 check on each Block of the Hex file to obtain the corresponding CRC32 check code, and put it into the specified address position according to the Intel format, that is, the reverse order in which the most significant bit is placed on the high address;
[0047] Step 3, perform AES128 encryption on the data field in each Record, keep the data length field, address field, data type field and checksum field unchanged, and set the corresponding decryption program in the TCU internal startup program;
[0048] Step 4, recalculate the checksum of each encrypted Record;
[0049] Step 5, write the Hex file processed in steps 1 to 4 to the TCU, and start the program inside the TCU to decrypt it;...
Embodiment 3
[0052] Process the Hex file that needs to be flashed in the car ESC, specifically:
[0053] Step 1. Group the Blocks of the Hex file. The number of blocks in each group varies according to the needs. Perform CRC16 check on the specified address segment of each group of Blocks to obtain the corresponding CRC16 check code, and put it into the specified address location according to the Intel format. , that is, the reverse order in which the most significant bit is placed on the high address;
[0054]Step 2, perform AES192 encryption on the data field in each Record, keep the data length field, address field, data type field and checksum field unchanged, and set the corresponding decryption program in the ESC internal startup program;
[0055] Step 3, recalculate the checksum of each encrypted Record;
[0056] Step 4, write the Hex file processed in steps 1 to 3 to the ESC, and start the program inside the ESC to decrypt it;
[0057] Step 5: The ESC calculates the CRC16 check c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com