Intelligent safety management system and method based on biometric identification technology
A technology of biometric identification and security management, applied in the field of intelligent security management system based on biometric identification technology, can solve problems such as inability to perform security management, unable to verify the identity and authority of key holders, and key loss, so as to eliminate Possibility of human error operation, improvement of maintenance work efficiency, and effect of improving maintenance work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
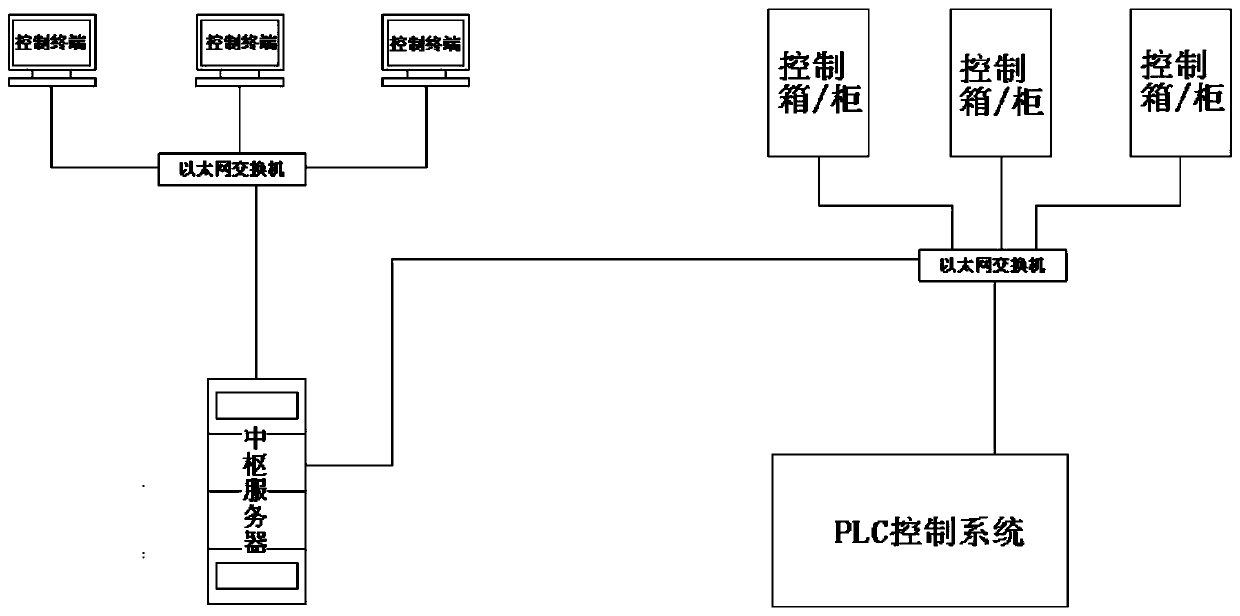
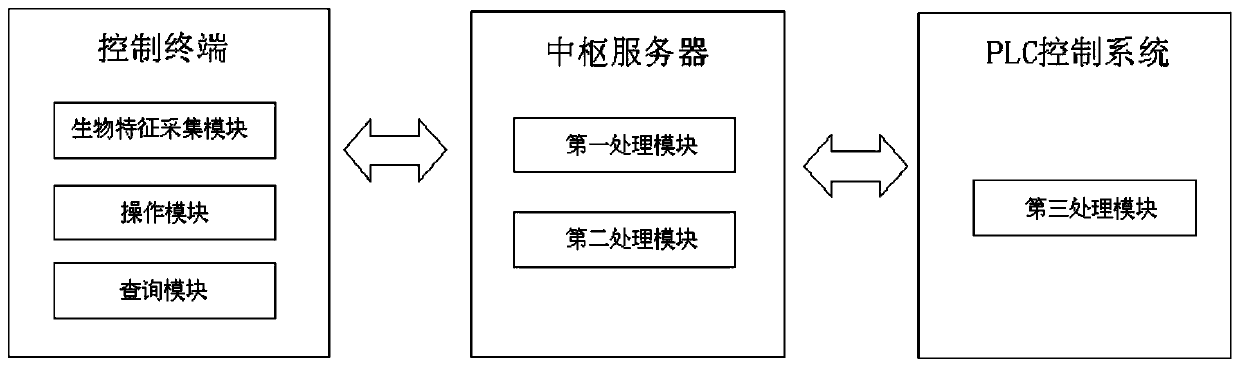
[0031] Embodiment 1: see figure 1 and figure 2 , the present embodiment relates to an intelligent security management system based on biometric feature recognition technology, including a control terminal, which has a biometric feature collection module and an operation module.
[0032] The biometrics collection module is used to collect the biometrics of the operator and send them to the central server. Wherein, the biometric feature is fingerprint, human face, iris or voice, preferably fingerprint.
[0033] The operation module is used to receive the judgment result fed back from the central server. If it has the authority, it will send a lock or unlock command to the central server. If it has no authority, it will prompt that there is no operation authority.
[0034] The hub server has a first processing module and a second processing module.
[0035] The first processing module is used to receive the operator's biometrics sent by the acquisition module, query the maint...
Embodiment 2
[0042] Embodiment 2: This embodiment relates to an intelligent security management method based on biometric identification technology, including the following steps: S101, the control terminal collects the operator's biological characteristics and sends it to the central server; S102, the control terminal receives the judgment of the central server's feedback As a result, if there is permission, a lock or unlock command is sent to the central server, and if there is no permission, it prompts that there is no operation permission.
[0043] In step S102, the central server includes the following steps: K101. The central server receives the operator's biological characteristics sent by the control terminal, and queries the maintenance item knowledge base of the central server according to the operator's biological characteristics to determine whether it has the maintenance operation authority, and reports the judgment result Feedback to the operation module; K102, the central ser...
Embodiment 3
[0047] Embodiment 3: An intelligent safety management system based on biometric identification technology can further improve its functions on the basis of Embodiment 1, such as the function of shift change, the precondition function of maintenance operations, and so on.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com