A security control method
A security control and active security technology, applied in computer security devices, instruments, computing, etc., can solve problems such as inability to provide trust in system device controller chips, failure to provide trust transfer implementation methods, motherboard peripherals, and BOOTROM protection. , to achieve the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
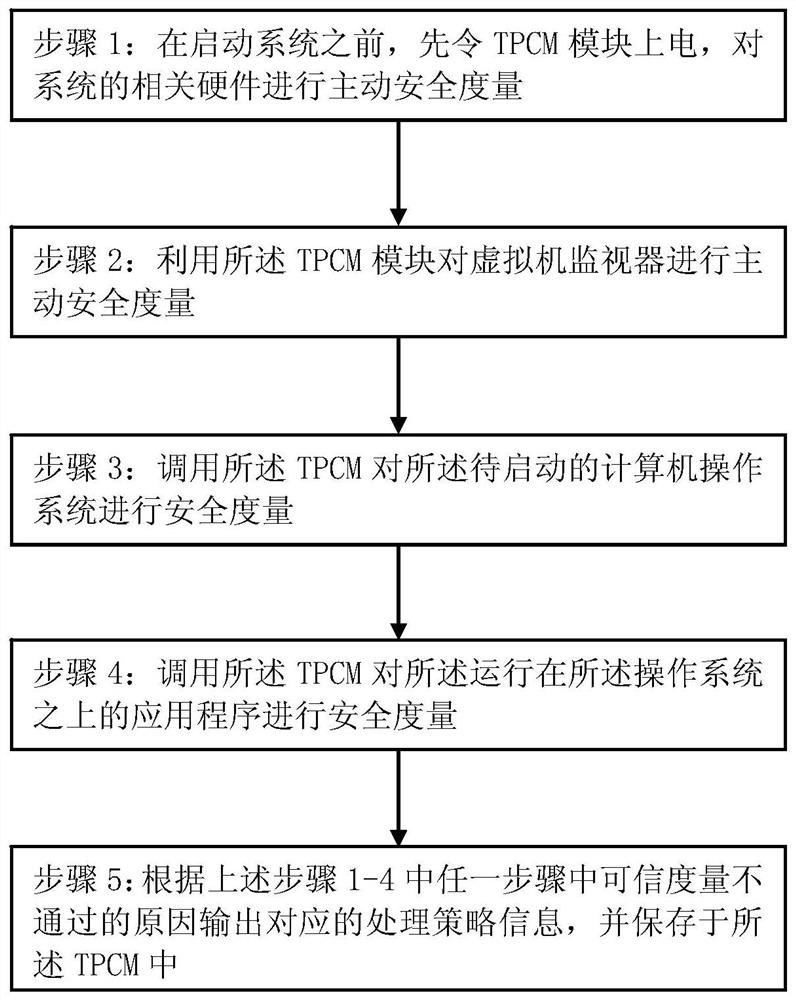
[0039] This embodiment proposes a security control method, the flow chart of which is as follows figure 1 As shown, before the system is started, the TPCM is first ordered to be powered on, and the TPCM performs active security measurement on the hardware integrity of the system. After the measurement is passed, the active security measurement is performed on the operating system and related application software, and the computer system trust chain is completed. established, the method includes:
[0040] Step 1: Before starting the system, shill the TPCM module to be powered on, and carry out active safety measurement on the relevant hardware of the system.
[0041] Specifically, the TPCM module is set independently of the computer operating system to be started, so as to ensure that the active security measurement process will not be affected when the computer operating system to be started is abnormal, and the TPCM is the The only trusted root of the computer operating syst...
Embodiment 2
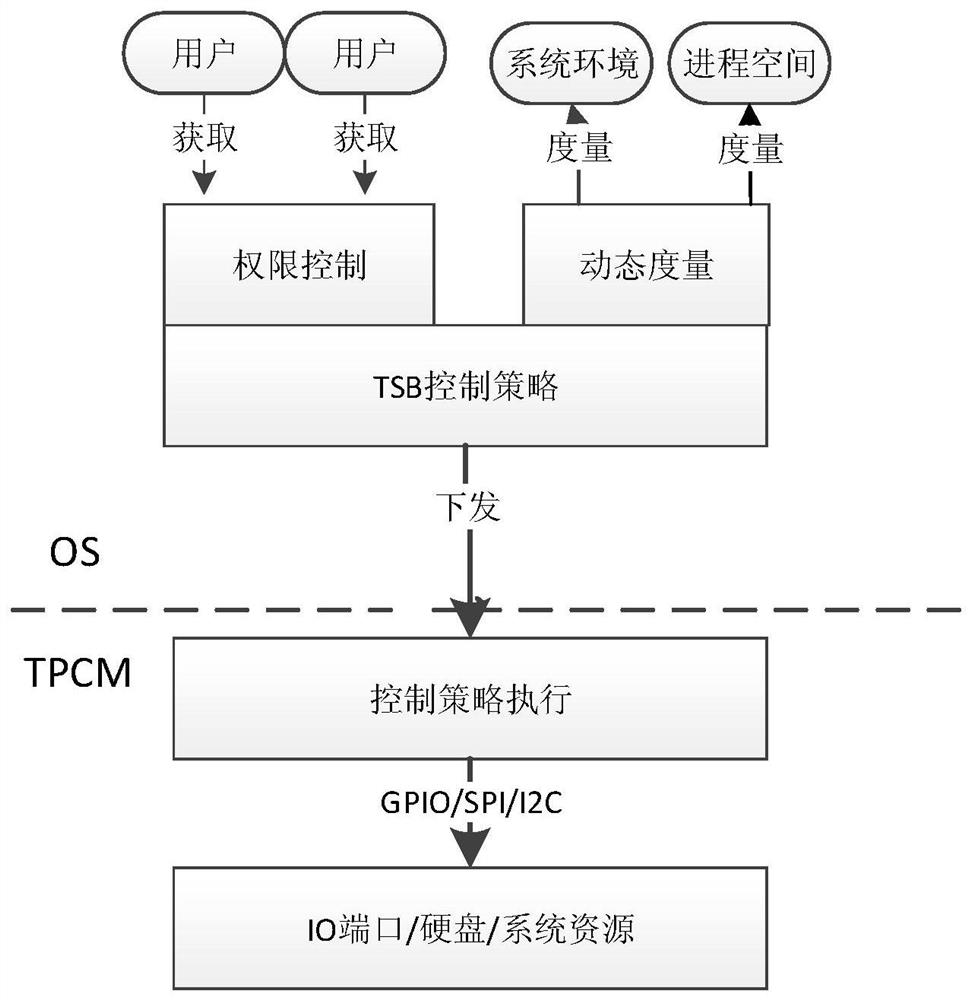
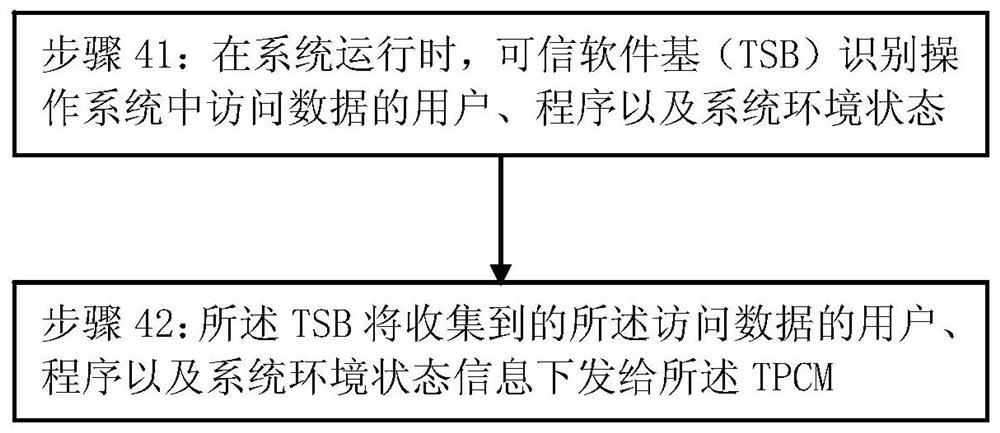
[0062] Based on the method in Embodiment 1, this embodiment proposes a method to ensure the safe operation of the operating system, and its functional structure diagram is as follows figure 2 As shown, the flow chart is as image 3 As shown, the following steps are located between step 4 and step 5 in Embodiment 1, including:
[0063] Step 41: When the system is running, the Trusted Software Base (TSB) identifies users, programs, and system environment status that access data in the operating system.
[0064] Specifically, the identifying the user who accesses the data in the operating system includes calling the authority control module through the TSB, so as to obtain the identity information of the user, and the identity information includes a user ID.
[0065] Specifically, the identifying the program and system environment state in the operating system includes calling a dynamic measurement module through the TSB, and the dynamic measurement module performs active secur...
Embodiment 3
[0071] The present invention also proposes a trusted control method based on a trusted hard disk, characterized in that the method includes:
[0072] Step 1. Power on the trusted hard disk, use the TPCM module embedded in the hard disk chip in the trusted hard disk to measure other hardware in its system, if the measurement result of the other hardware is normal, then enter step 2, if If the measurement result of the other hardware is abnormal, then alarm;
[0073] Step 2. Power on the other hardware, start the system where the trusted hard disk is located, measure the software in the system where the trusted hard disk is located, if the measurement result of the software is normal, then enter step 3, if If the measurement result of the software is abnormal, then report to the police;
[0074] Step 3. The system where the trusted hard disk is located runs normally. When the system where the trusted hard disk is located performs read / write operations on the trusted hard disk, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com