Privacy budget allocating and data publishing method and privacy budget allocating and data publishing system for protecting data query privacy
A privacy protection and budget allocation technology, applied in the field of information security, can solve the problems of limiting the number of user queries, the inability to realize infinite queries of data sets, and the reduction of data availability, so as to achieve the effects of improving availability, resisting collusion attacks, and ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
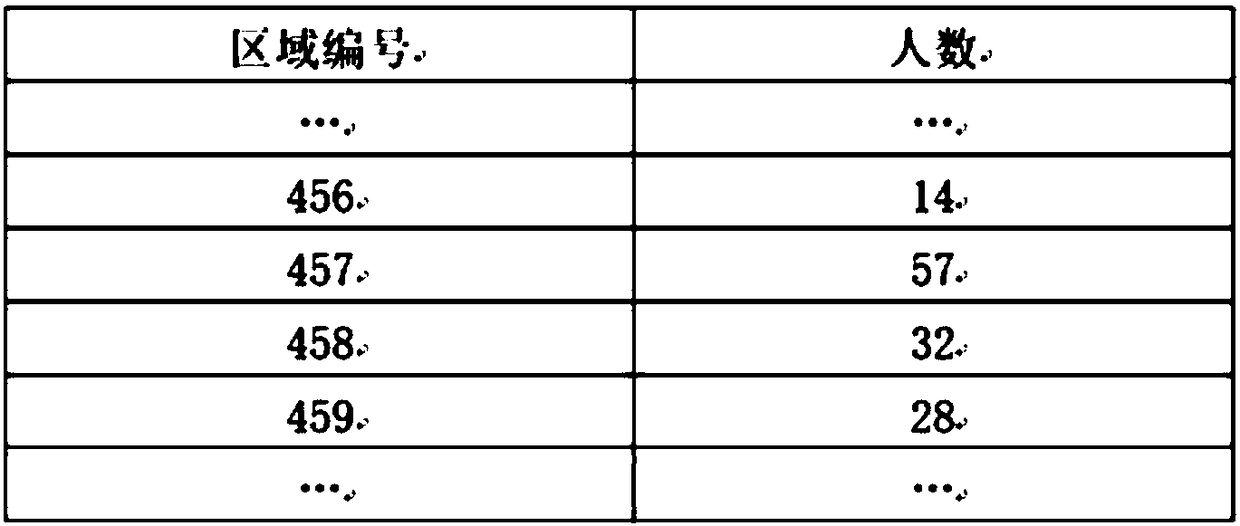
[0058] Waitakere is a semi-synthetic dataset generated from the New Zealand 2006 census grid dataset, with a total population of 186,471 distributed across 1,340 grid areas. We randomly placed residents into each grid block, and then the entire area Divide it into 7,725 non-overlapping rectangles (154×113m2 in size), and count the population in each rectangle.
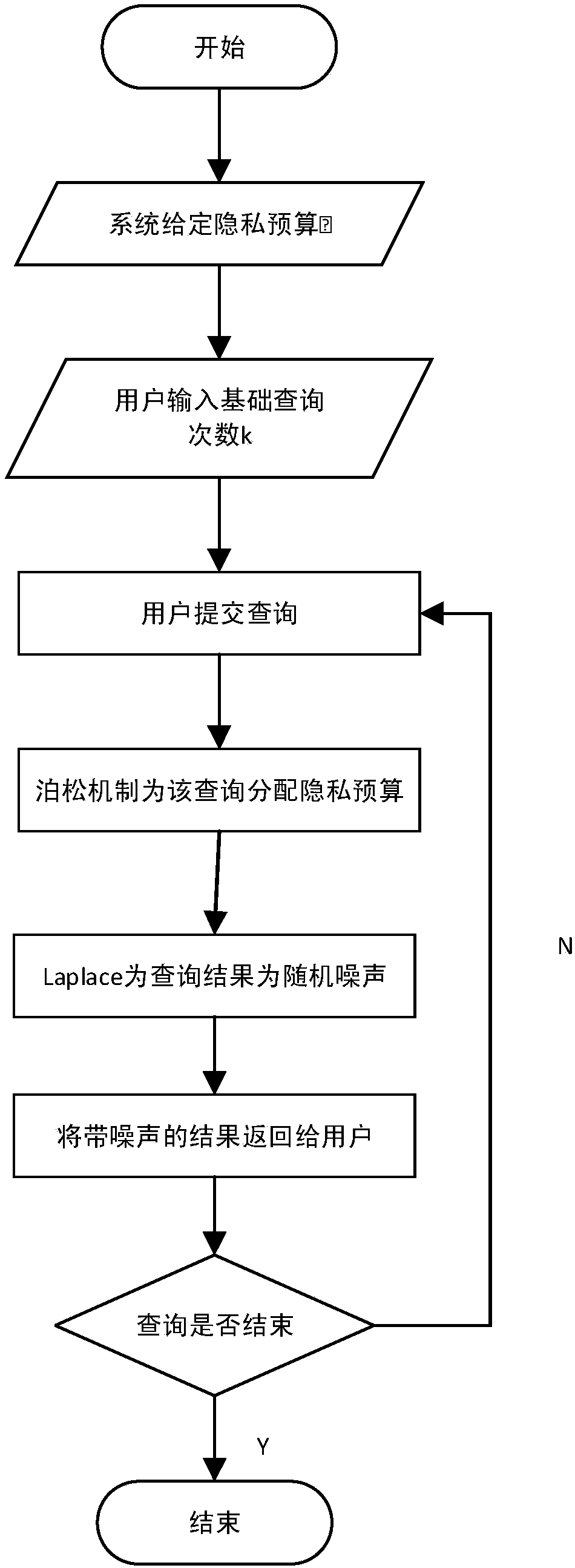
[0059] Step 1. Take the privacy budget ε=1, and take the number of basic queries k=10;
[0060] Step 2. Calculate the privacy budget based on the Poisson mechanism:
[0061]
[0062] Step 3. According to the query submitted by the user, Laplace adds random noise to the query results. In order to simplify the operation, we set the query set F={f|f to find the total number of people in the interval [456,459]}, that is, f 1 =f 2 =…=f n =...=f, Δf 1 =Δf 2 =...=Δf n =...=Δf=1,f 1 (D) = f 2 (D)=...=f n (D)=...=f(D)=131.
[0063] When the user submits the first query f 1 When the query result f 1 Add a random n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com