Method, system and related device for acquiring Android application primary layer code
A code and target application technology, applied in computer security devices, program code conversion, decompilation/disassembly, etc., can solve problems such as low survival rate, insufficient time to obtain decrypted code, and difficulty in escaping antivirus software interception, etc. , to achieve high accuracy and improve acquisition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
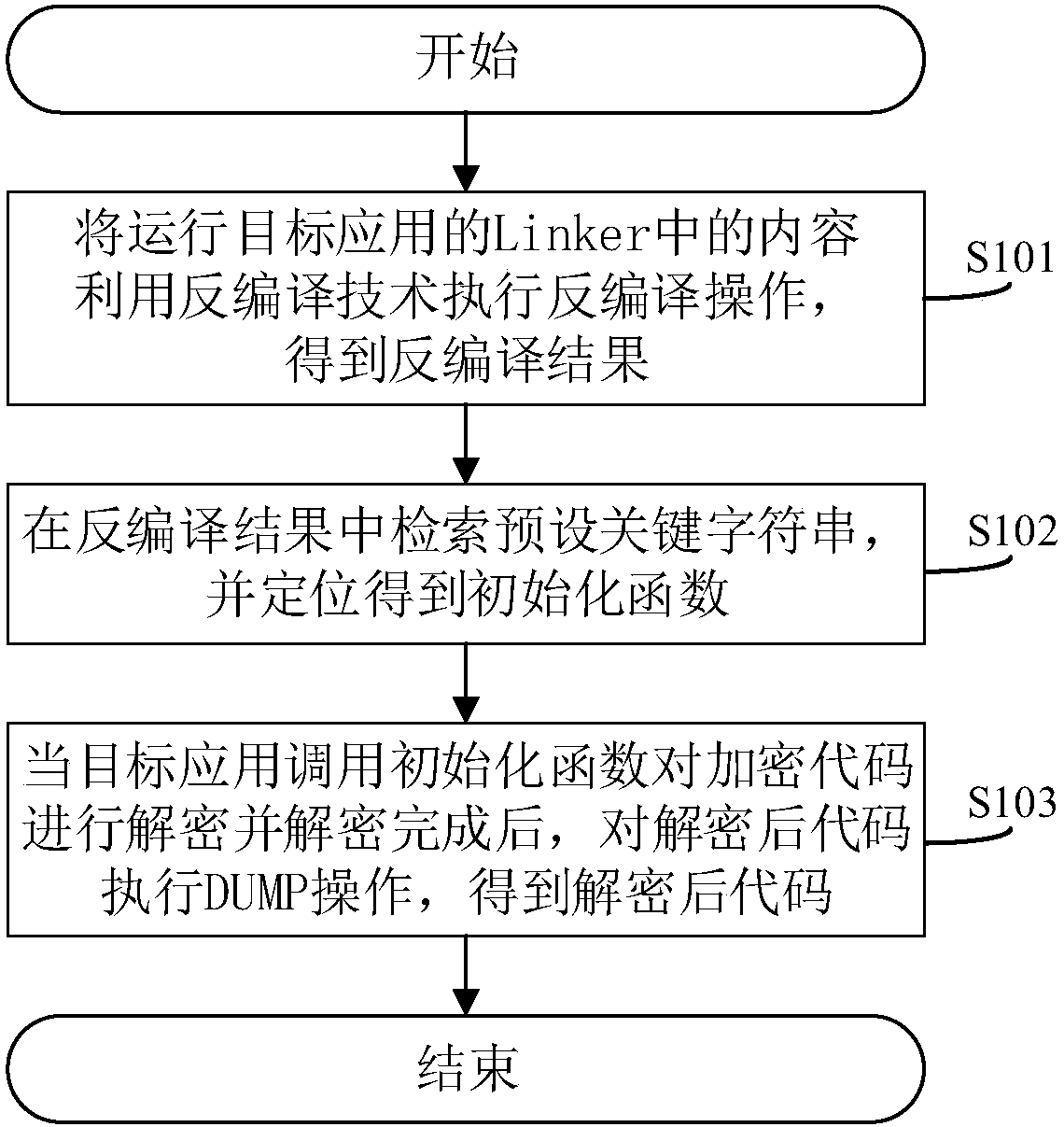
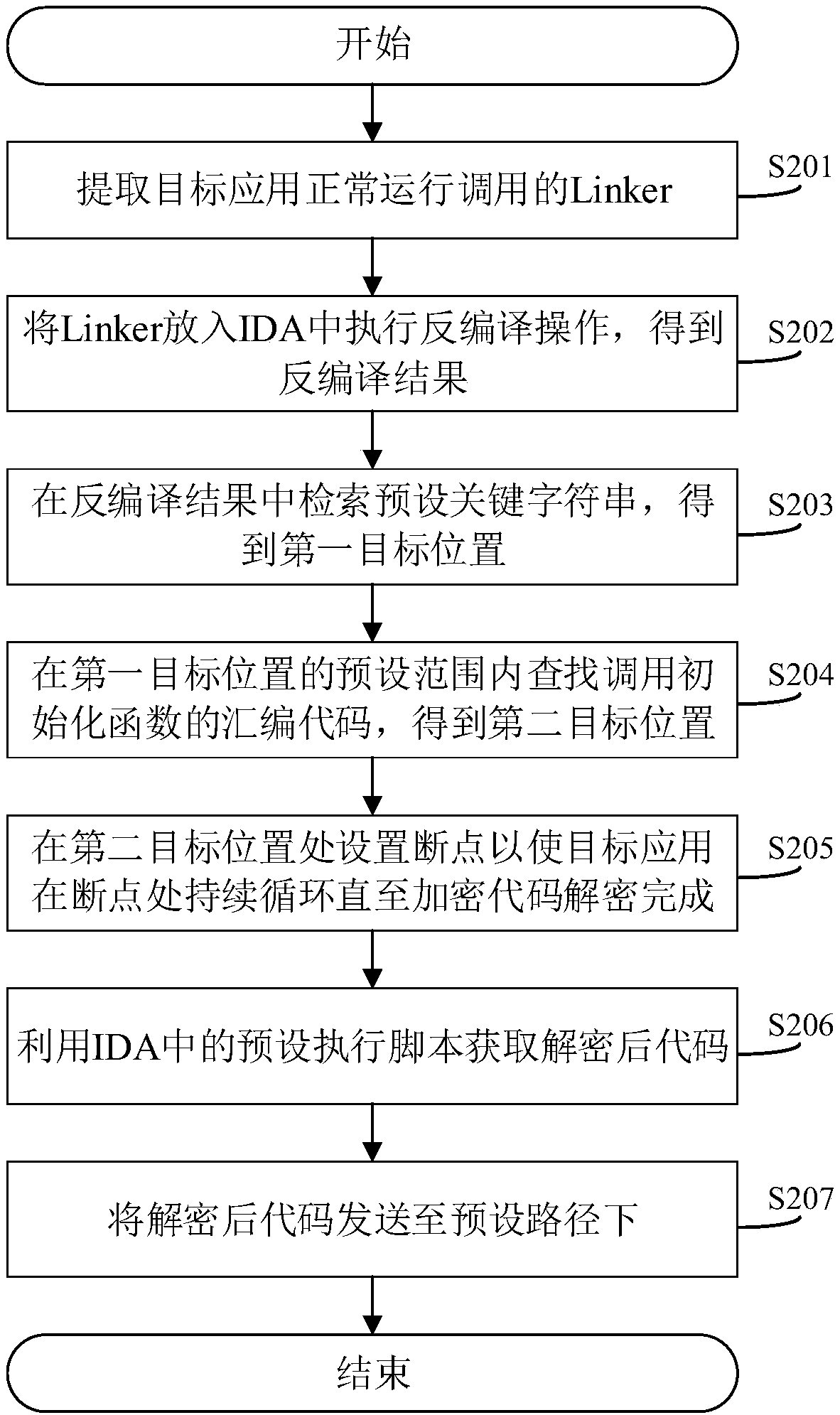
[0043] In view of the fact that the existing decrypted code acquisition method cannot achieve the purpose of accurately obtaining the decrypted code, it will waste the time of analysts and even lead to erroneous analysis results. Therefore, this application re-examines the running process of the Android application, and aims to provide a method that can overcome various technical defects existing in the prior art starting from the bottom layer of the running of the Android system. Here is a brief background description of the running process of the Android application on the Android system:
[0044] Linker is the loading / linker of the Android system, mainly used to realize the loading and linking of the shared library. The shared library is a collection of functions that may be called and used by various applications running on the Android system. Common components are convenient for the calling of various applications, just like the environment components we need to install a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com