Safe Android APP function pluggable method
A functional and safe technology, applied in the field of Android applications, can solve problems such as security risks and repeated update troubles, and achieve the effect of ensuring application security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
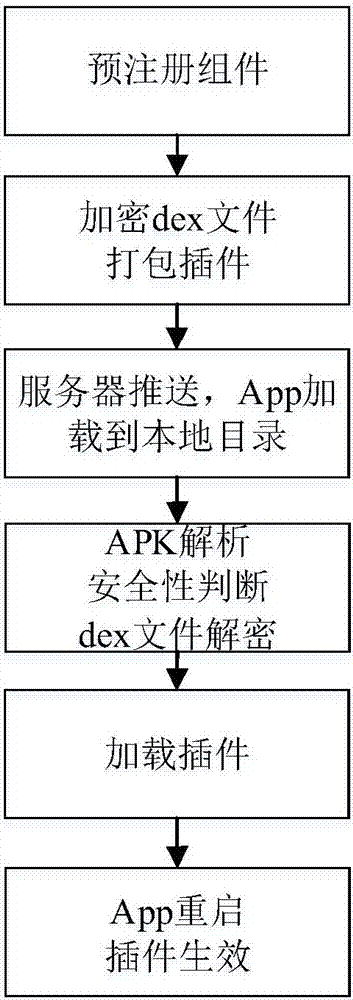
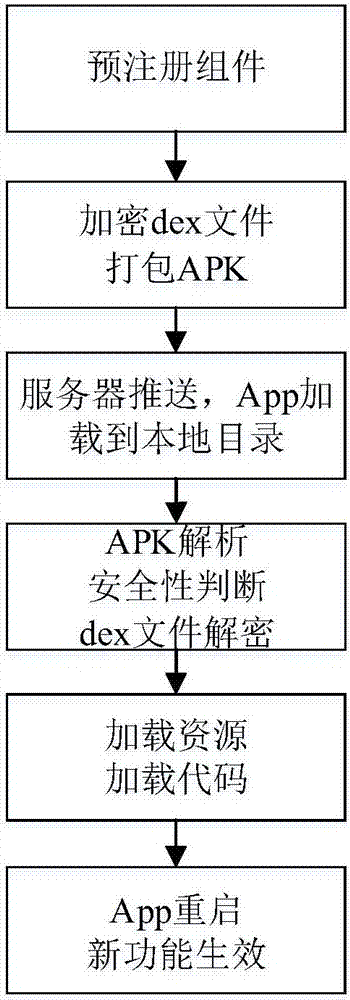
[0050] Embodiment 1, modular update, refer to figure 2 ,
[0051] Step 1. Carry out large-grained plug-in, and choose modular update
[0052] Step 2. Pre-register 6 processes in the AndroidManifest.xml file of the host application.
[0053] Each process contains 1 Service proxy component, 1 ContentProvider component, 1 Activity started in standard mode, and 5 Activities started in singleTop, singleTask, and singleInstance modes.
[0054] Step 3. Update the module to compile and generate a dex file, randomly generate a DES key, encrypt the file with the key, and pack the APK;
[0055] 3.1) Compile resource and java code, generate dex file and resource id;
[0056] 3.2) Encrypt the dex file with a randomly generated key, and append the key to the end of the dex file;
[0057] 3.3) Package the compiled resource files and encrypted dex files into an APK package and sign the APK. The signature file must be consistent with the application release, and deploy the signed APK on t...
Embodiment 2
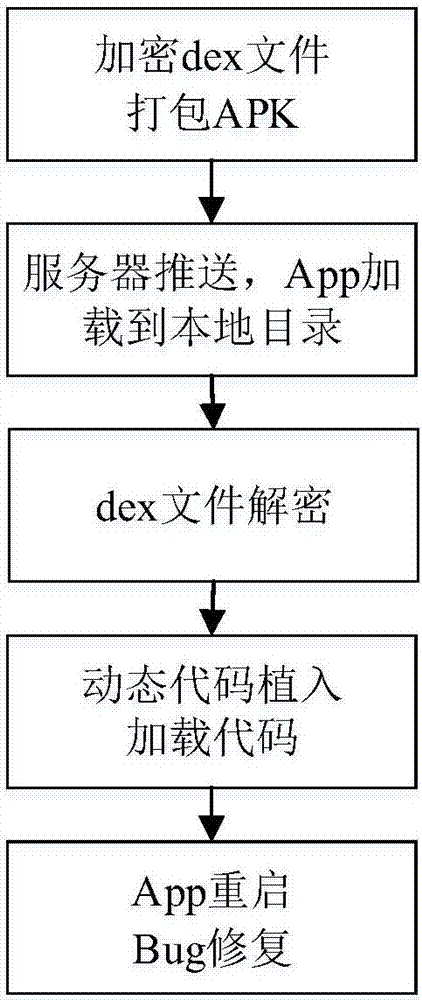
[0068] Embodiment 2, thermal repair, refer to image 3 ,
[0069] Step 1. Carry out small-grained plug-in, and select hot repair;
[0070] Step 2, dynamic code injection, providing a dex jar package and packaging it into the host application;
[0071] 2.1) Write a switch in the Application class in the host program to control whether to perform code injection;
[0072] 2.2) Write a class file containing at least one class and generate a jar package of a dex file, named hotPatch.jar, and package it into the host application when the host application is packaged;
[0073] Step 3. Compile the java code to generate a dex file, generate a random DES key to encrypt the dex file, and deploy the file on the server;
[0074] 3.1) Compile the repaired class to generate a dex file;
[0075] 3.2) Randomly generate a DES key, use the key to encrypt the dex file, and append the key to the end of the dex file;
[0076] 3.3) Deploy the dex file on the server;
[0077] Step 4, load the u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com