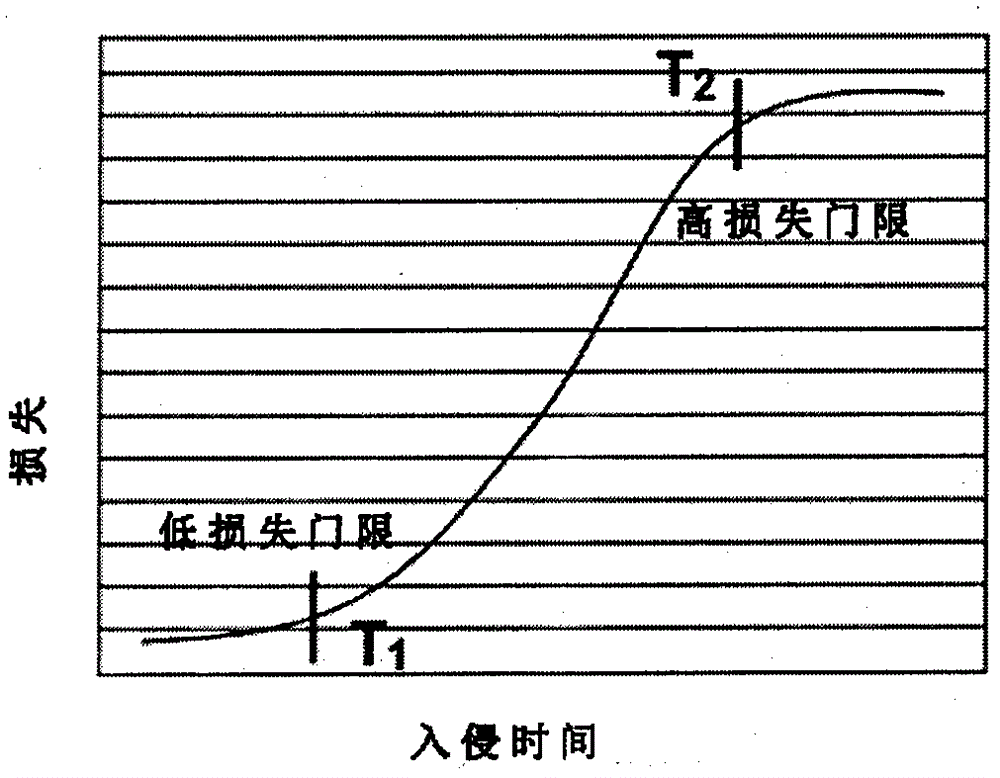
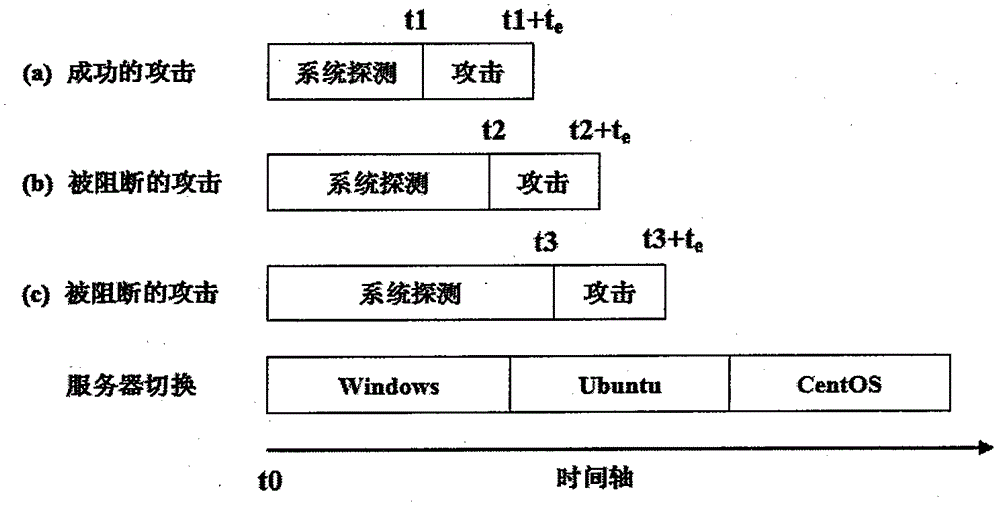
SCIT-based mobile target defensive system
A moving target defense and defense system technology, applied in the field of moving target defense systems, can solve the problems of lack of in-depth understanding and research on the impact of system security, and effective attack types.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In the content of the invention, the overall technical idea of the technical solution of the present invention is proposed. In order for those skilled in the art to further understand the content of the present invention, the technical solution of the application of the present invention will be further described below in conjunction with specific embodiments.
[0027] First, three ThinkPad X240 (CPU i7-2640M@2.8GHz, memory 12GB) are selected as the hosts of the back-end server group; one DELL Ins15RR (CPU i5-3210M@2.5GHz, memory 4GB) is used as the central controller; One NSFOCUS remote vulnerability scanner is used for vulnerability scanning, and the software stack composition of three ThinkPad X240s is shown in Table 2:
[0028]
[0029] Table 2 The specific composition of the software stack
[0030] The scanning results of the NSFOCUS remote vulnerability scanner show that the RPC vulnerability numbered MS08-067 exists only in the ThinkPad X240 of Windows 2007....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com