Electric power communication method and device
A power communication and server technology, applied in electrical components, transmission systems, etc., can solve problems such as shutdown, attack, and unprotected computers, saving time and cost and ensuring information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
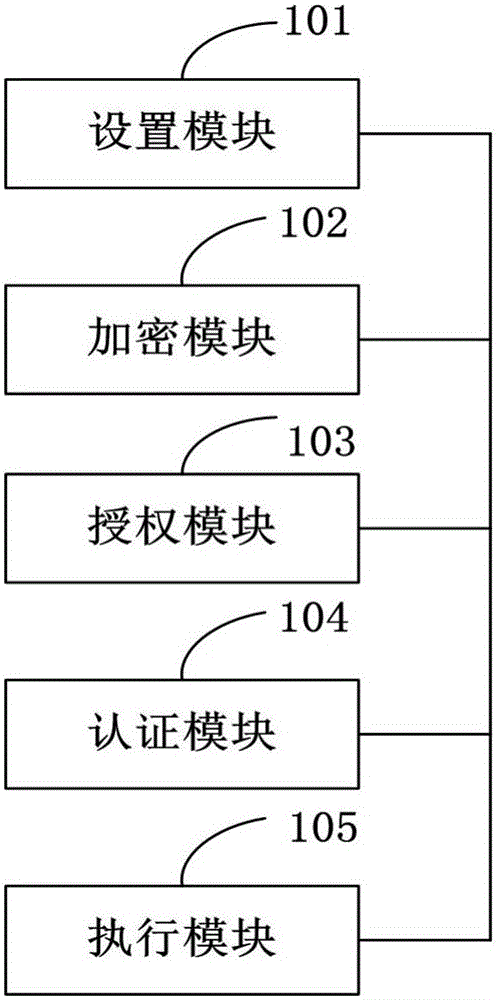
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
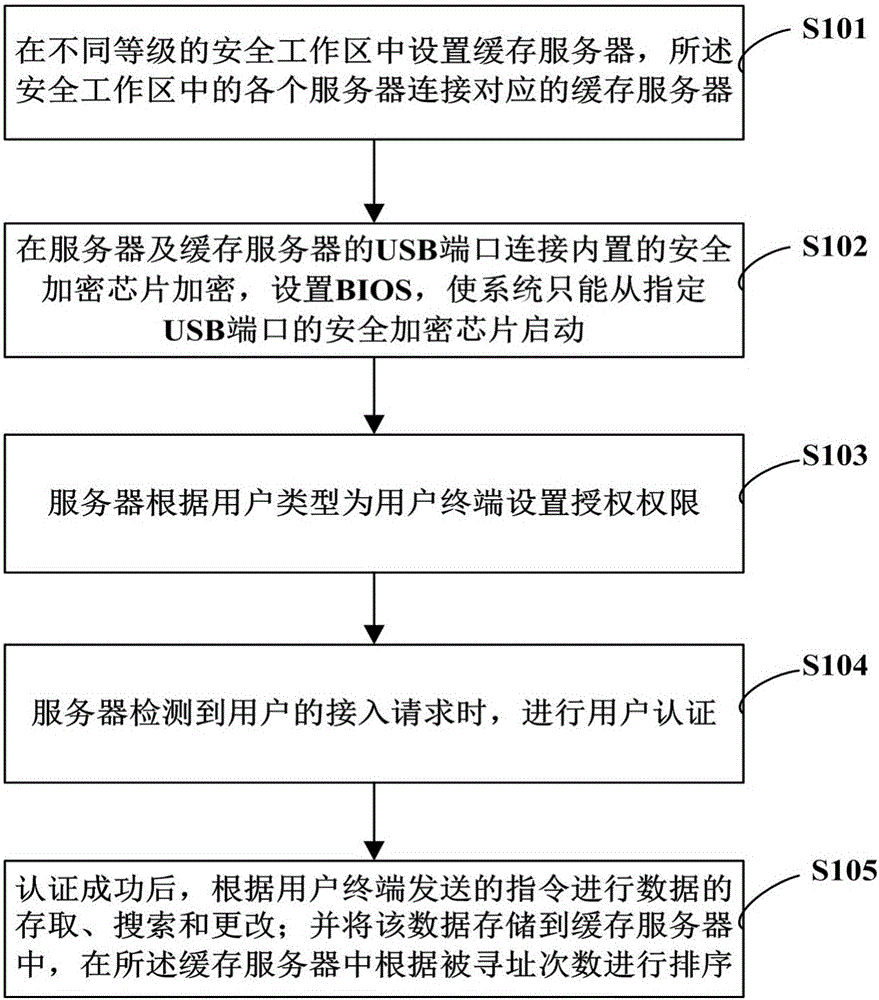
[0046] Such as figure 1 As shown, a power communication method includes the following steps:
[0047] Step S101, setting cache servers in different levels of security work areas, each server in the security work area is connected to a corresponding cache server, and the server and cache servers are connected via a virtual private network (VPN);
[0048] Step S102, connect the built-in security encryption chip to the USB port of the server and the cache server for encryption, set the BIOS so that the system can only start from the security encryption chip of the designated USB port; start the system, and judge whether the security encryption chip is working normally, if not work, the system will automatically shut down;
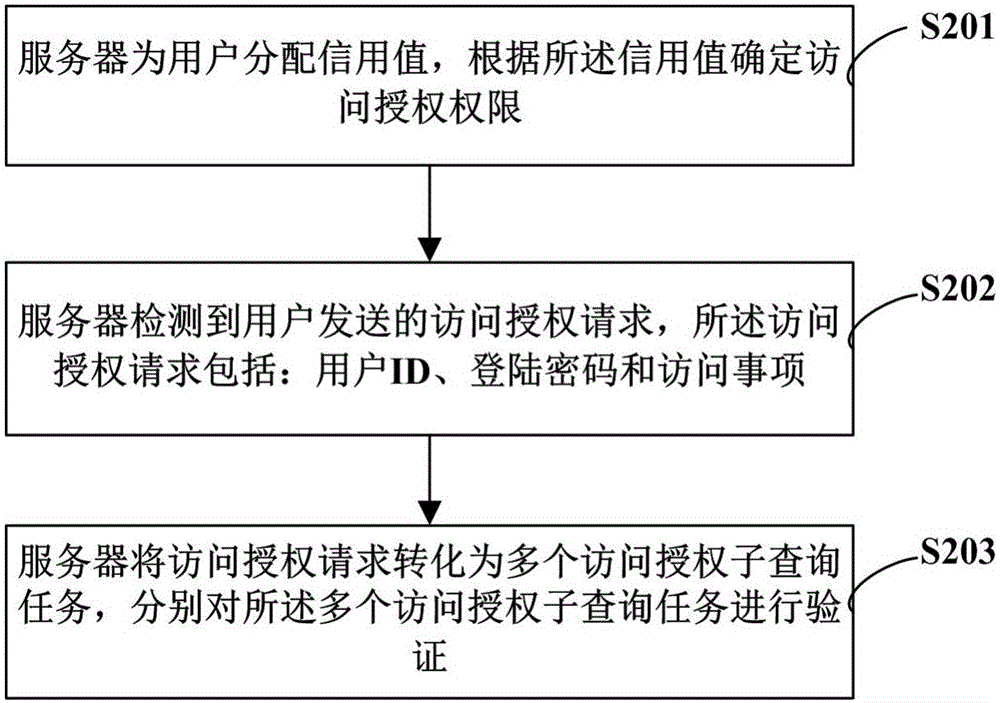
[0049] Step S103, the server sets the authorization authority for the user terminal according to the user type; the USB port of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com