Anomaly detection in industrial communications networks
A communication network and anomaly detection technology, applied in the direction of error detection/correction, general control system, electrical test/monitoring, etc., can solve problems such as interruption of factory operations, difficulty in detection, generation of errors or alarms, etc., to reduce workload, reduce The effect of the false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
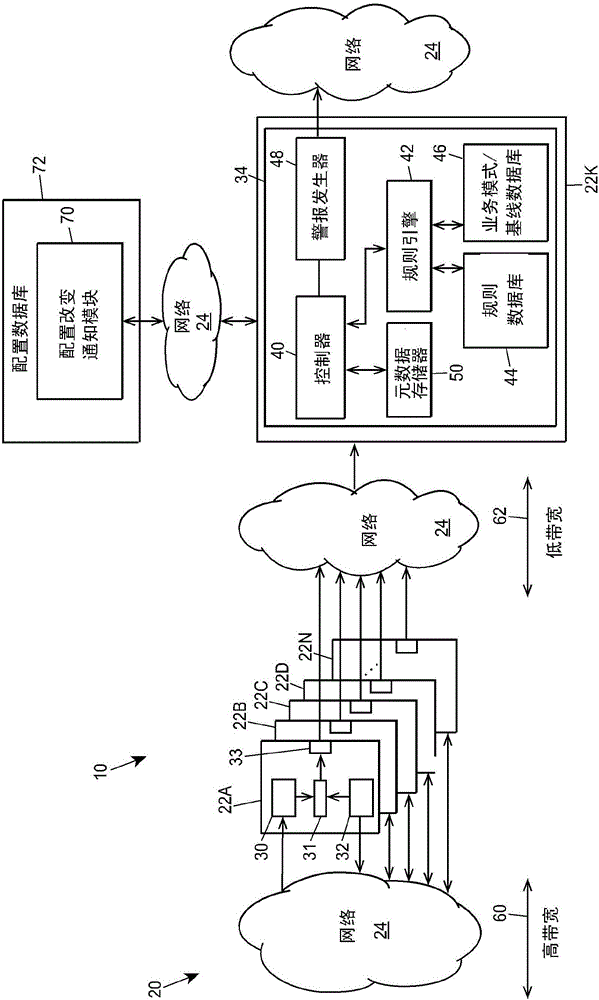
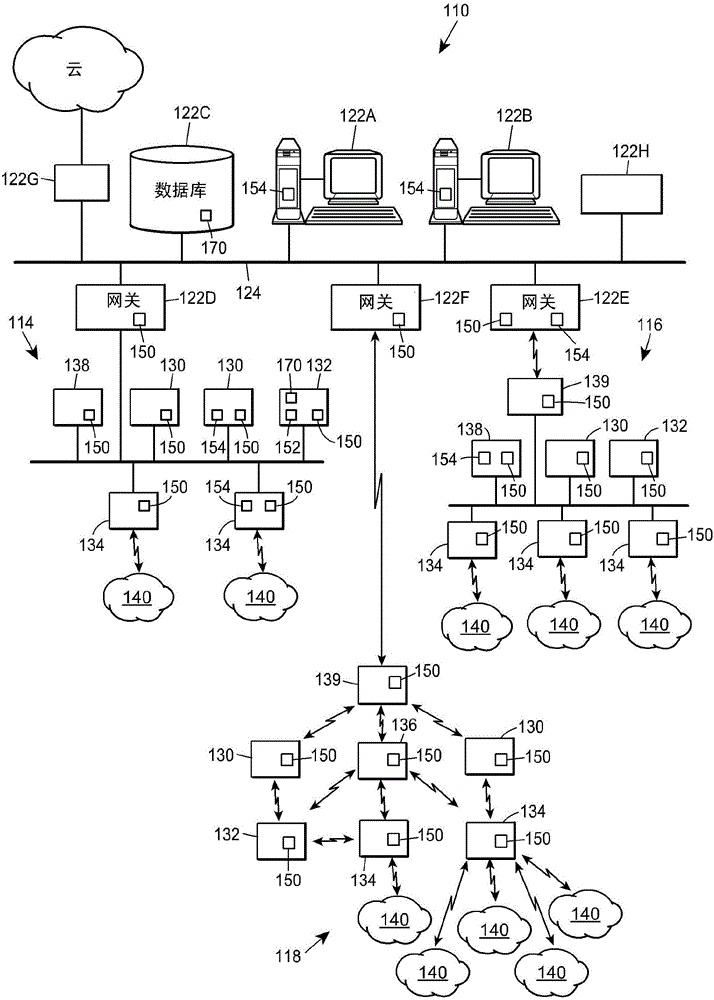
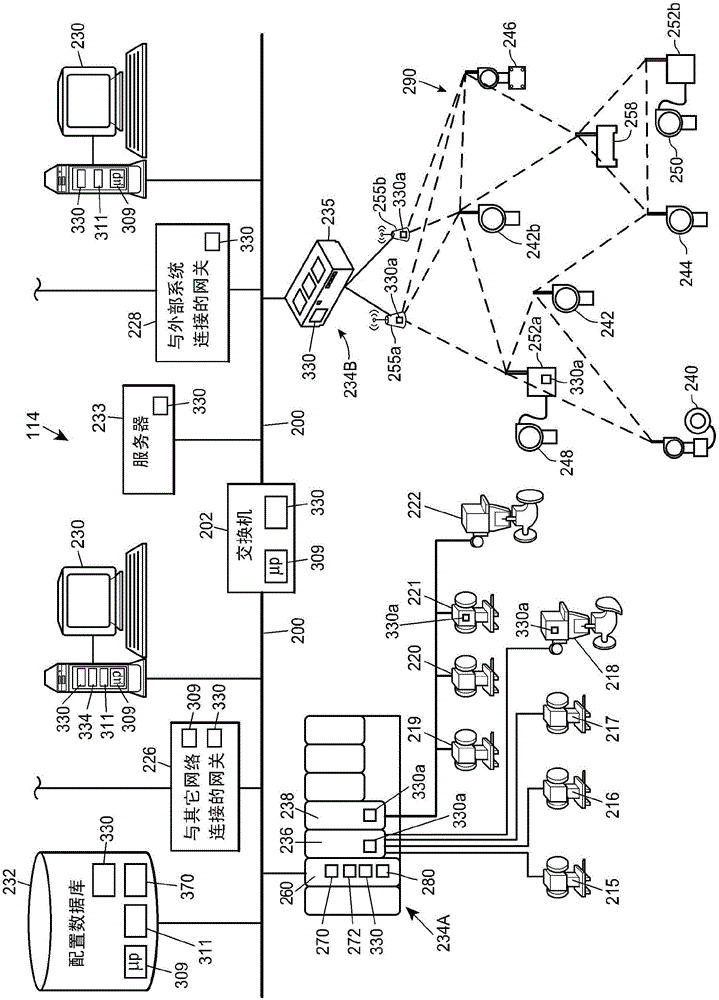
[0016]In general, the network security systems described herein work by detecting anomalies in network traffic patterns (e.g., traffic or message content, frequency, timing, length, etc.) at or across nodes in an industrial system or process control network To perform threat detection, it can be performed efficiently due to the a priori performance of industrial system or process control network configurations to compare measured traffic patterns with expected or known patterns. That is, the configuration of network communications in a process control, industrial system, or factory automation network is usually fairly well known prior to the implementation or operation of that communications network, so that network business patterns are not relevant during the use or operation of those networks. will not tend to change significantly. In contrast, network communication traffic patterns tend to be relatively static (in a statistical sense) during the operation of the communicat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com