Information security processing method and security processing apparatus
A security processing and security mechanism technology, applied in data processing applications, protocol authorization, instruments, etc., can solve problems such as reducing the efficiency of public transport systems, and achieve the effect of improving the convenience of use and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
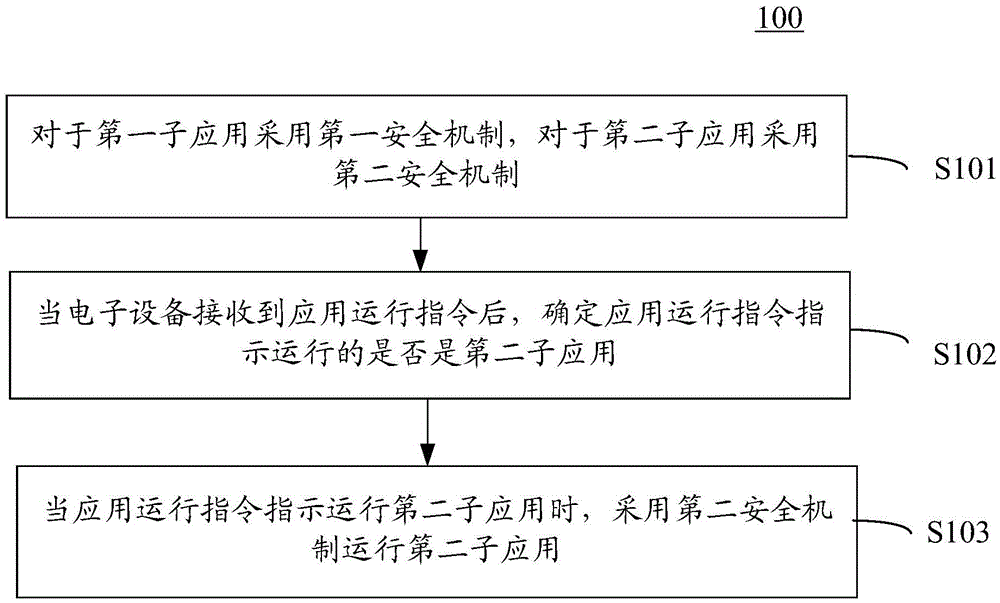
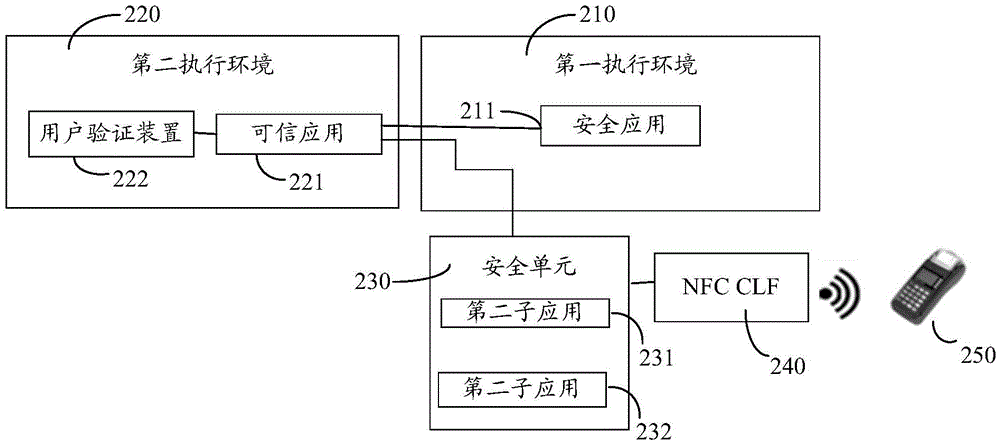
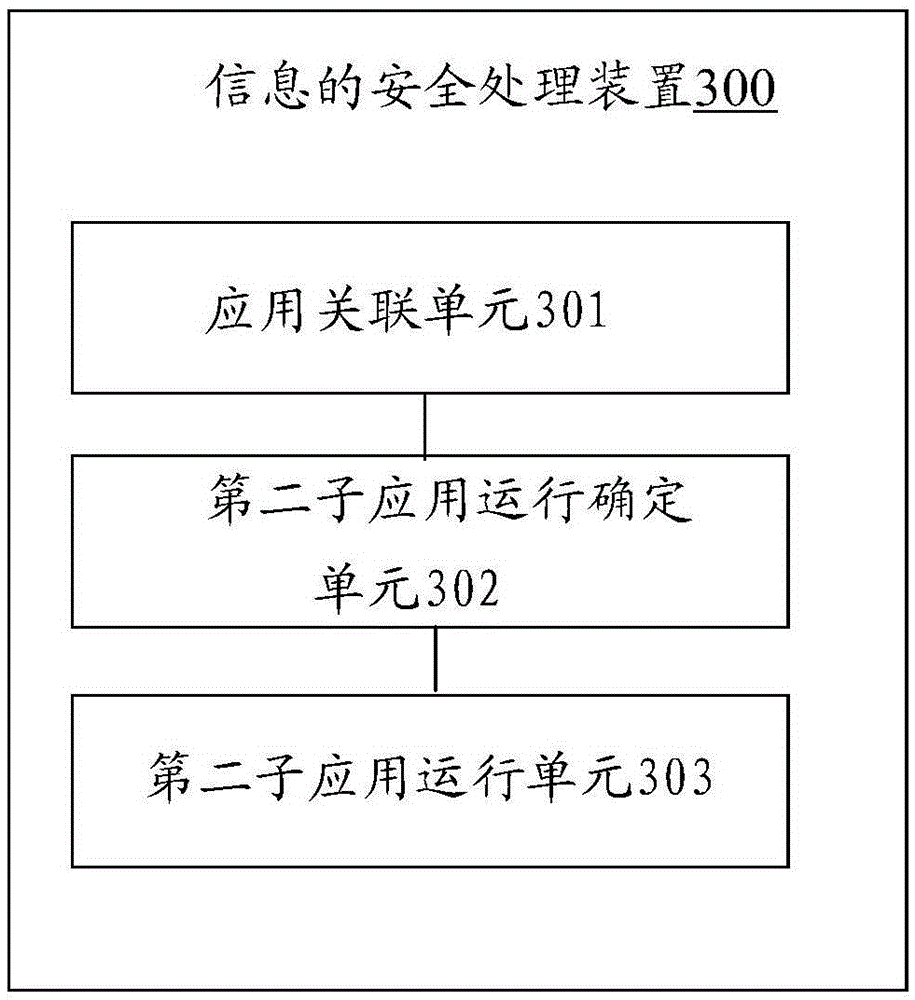
[0012] Hereinafter, preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings. Note that in this specification and the drawings, substantially the same steps and elements are denoted by the same reference numerals, and repeated explanation of these steps and elements will be omitted.
[0013] In the following embodiments of the present invention, an electronic device refers to a device capable of communicating with other devices. Particular forms of electronic equipment include, but are not limited to, mobile phones, personal computers, digital cameras, personal digital assistants, portable computers, game consoles, and the like. In the embodiment of the invention, the electronic device is capable of running a security application, and the security application is associated with a first sub-application and a second sub-application, and the first sub-application is different from the second sub-application. For examp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com