Asymmetric FHE (Fully Homomorphic Encryption) method and secret key substitution and cipher text delivery methods thereof
A homomorphic encryption, asymmetric technology, applied in the field of information security, to achieve the effect of improving computing speed, eliminating security risks, and wide application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
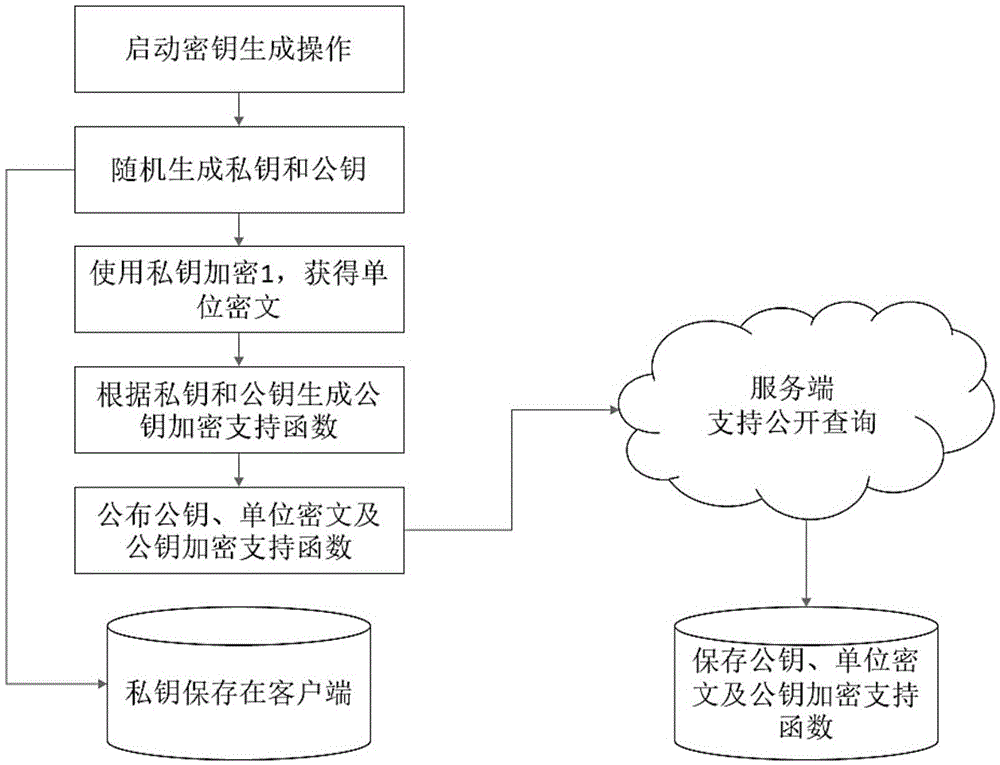
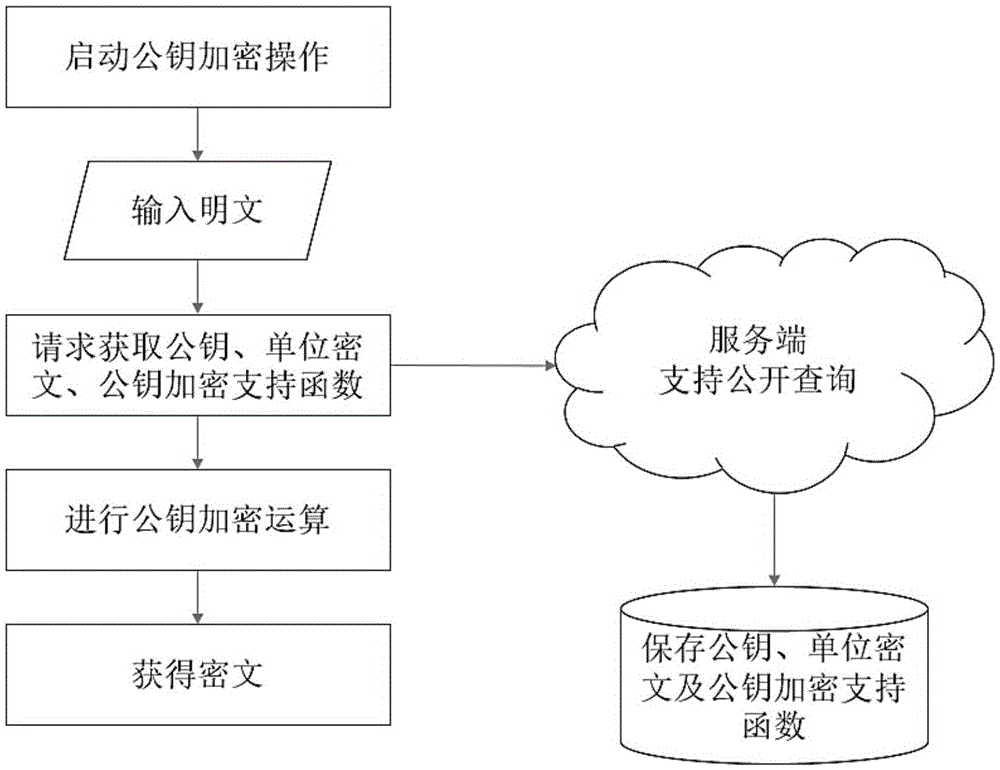
[0041] Because the ciphertext obtained by the fully homomorphic encryption method is operable, the ciphertext encrypted with the same key can be operated by relying on the operation support function, but the ciphertext encrypted with different keys cannot. Therefore, we call the space formed by all ciphertexts generated using the same key as the key space corresponding to this key. Only two ciphertexts in the same key space can be operated, while ciphertexts in different key spaces Ciphertext cannot be manipulated.
[0042] The asymmetric fully homomorphic encryption system involved in this embodiment is implemented in the following ways:
[0043] i) System initialization, setting with C K,1 ={A 1 ,X 1 ,B 1} as the unit ciphertext corresponding to the private key K, where: f(x i )>0 and f() is differentiable, K={f(),Y}, A 1 ={a 1i |i∈I} is a real vector, X 1 ={x 1i |i∈I} is a real vector, Y={y i |i∈I} is a real number vector; I is a polynomial key dimension subscri...
Embodiment 2
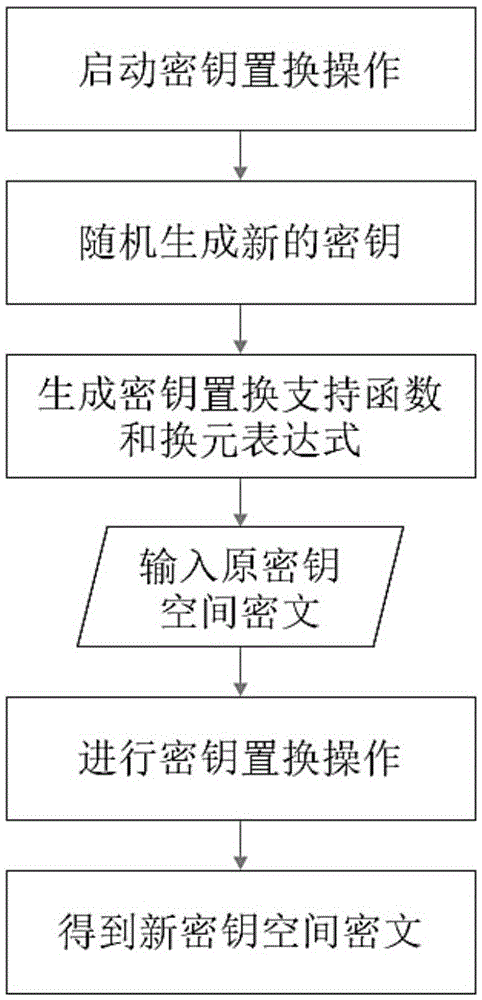
[0056] This embodiment is based on the asymmetric encryption system in Embodiment 1, and further realizes the ciphertext delivery in the following ways:
[0057] Step 1) System initialization, that is, the sender generates a private key K for sending A ={f A (), Y A}, the receiving end generates the receiving private key K B ={f B (), Y B}, the sender generates the ciphertext C to be sent A ={A A ,X A ,B A}, the server randomly generates a temporary key K 1 ={f 1 (), Y 1} and delivered to the sender and receiver respectively;
[0058] Step 2) The receiving end randomly generates a temporary receiving key K 2 ={f 2 (), Y 2} and key delivery function f T (), and generate delivery support functions at the receiving end and key receiving permutation function where: h temp1 (x,x')≠x≠x'; then the receiving end will deliver the key function f T () Delivery to the sender, delivery support function G to the receiver T and key receiving permutation function G 2→B ...
Embodiment 3
[0074] In some cases, the two parties to the ciphertext delivery can reach mutual trust. At this time, you can also choose a simplified ciphertext delivery operation. This operation does not require the participation of the server side, and can be completed only by the sending and receiving parties. The whole process is as follows:
[0075] Step 1) The receiving end randomly generates a temporary receiving private key K 1 ={f 1 (), Y 1}, key delivery function f T () and key receiving permutation function G 1→B , and will temporarily receive the private key K 1 and the key delivery function f T () delivered to the sender;
[0076] The receiving end preferably will temporarily receive the private key K after completing the transmission 1 destroy;
[0077] Step 2) The sender randomly generates a temporary private key K for sending 2 ={f 2 (), Y 2} and key sending permutation function G A→2 , and will send the ciphertext C A Convert to intermediate ciphertext C 2 ;Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com