Two-way link security authentication method for wireless relay network
A wireless relay network and two-way security authentication technology, which is applied in the field of network communication, can solve the problems of not being able to fully utilize the security of relay devices and consume a lot of time, and achieve the effect of solving asynchronization problems and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The concept, specific structure and technical effects of the present invention will be further described below in conjunction with the accompanying drawings, so as to fully understand the purpose, characteristics and effects of the present invention.
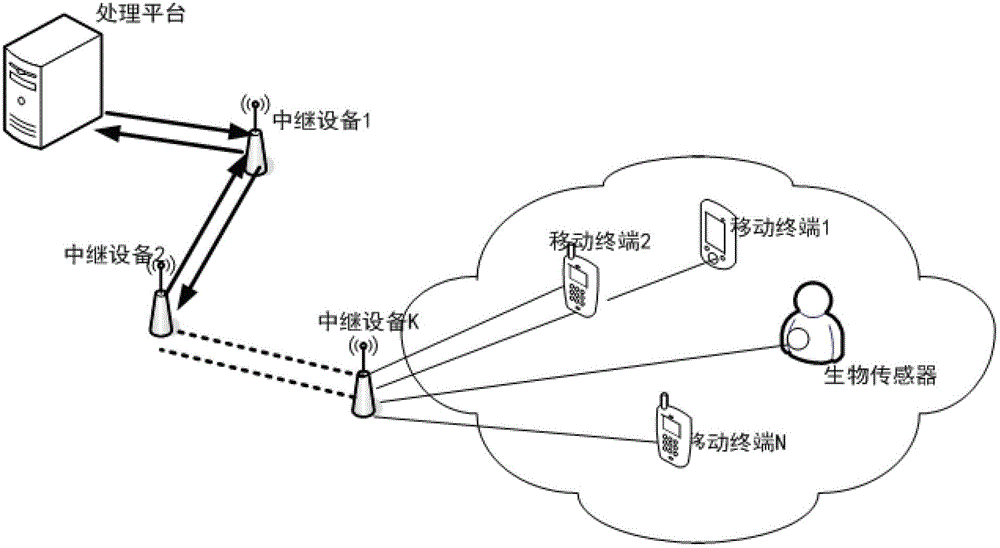
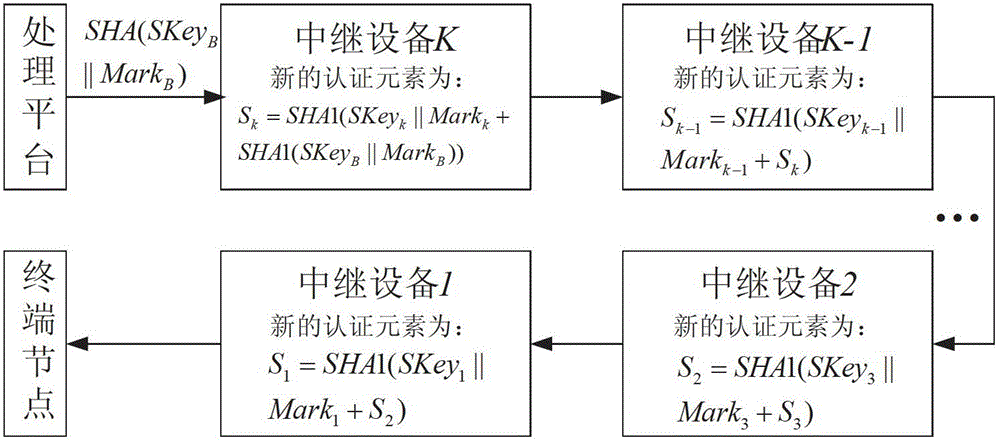
[0026] The bidirectional security authentication method of the link in the wireless relay network of the present invention adds the relay device to the security authentication process of the link, shares the computing burden of some terminal nodes, and at the same time only verifies the validity of the final information on the terminal nodes. Verification is performed to determine the legitimacy of the entire link.
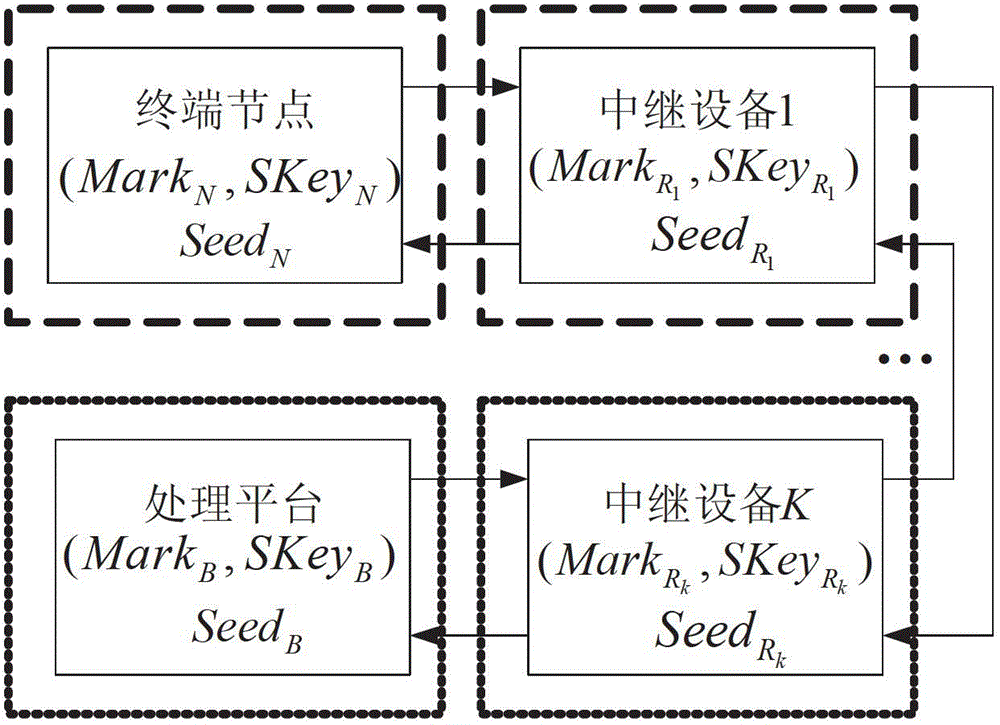
[0027] Each node on the entire link has its own private information SKey, Mark, Seed and (a n , a (n-1) ,...a 2 , a 1 ), where SKey is the key; Mark is reserved extended private information, which can be user authentication password, dynamic password, etc.; Seed is the seed; (a n , a (n-1) ,...a 2 , a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com