Deterministic finite-state machine construction method based on classification counter
A finite state machine and finite state technology, applied in computer security devices, instruments, computing, etc., can solve problems such as low matching efficiency and inability to repeat strings for many times, so as to improve the accuracy, reduce the number of transitions, and reduce errors. The effect of reporting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Below in conjunction with accompanying drawing, the present invention will be further described:
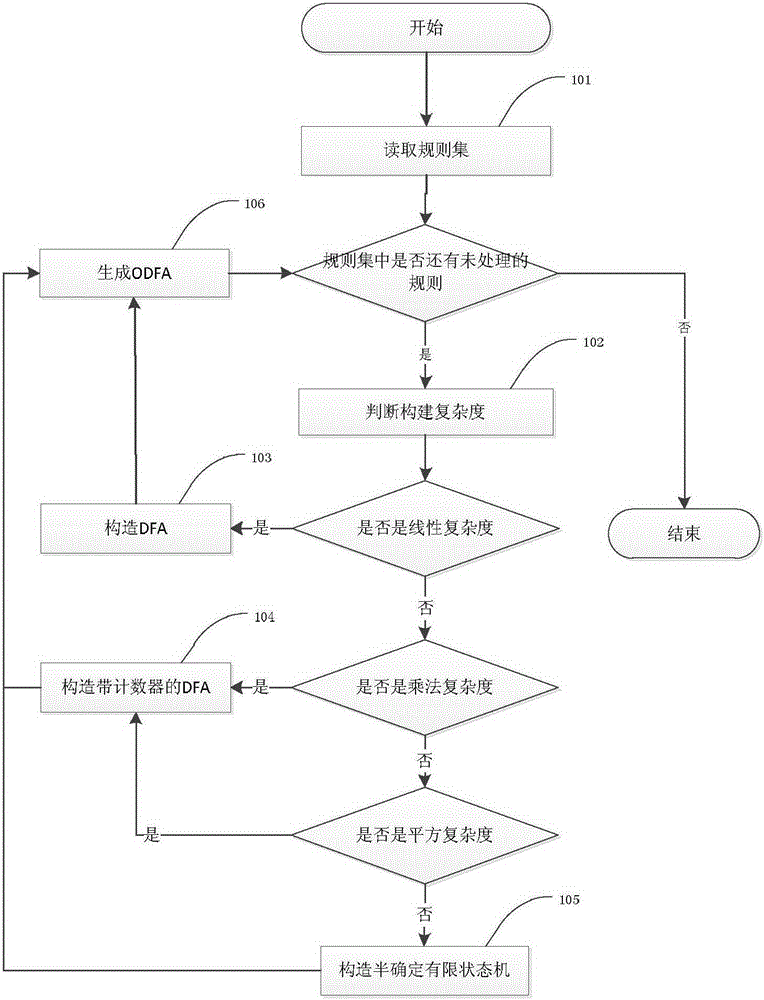
[0025] Such as figure 1 As shown, it is a method for determining the construction of a finite state machine according to an embodiment of the present invention, and the method includes:
[0026] 101. Read the rule set in the system, and check whether there are unconstructed rules in the rule set, and judge the construction complexity of the rule if there are unconstructed rules.
[0027] 102. Determine the construction complexity of the rules. The construction complexity refers to the complexity of the number of state points of the DFA generated by the rule formula. In the worst case, the construction complexity of a regular expression of length n is ο(2 n ). In practice, however, construction complexity is mostly linear, multiplicative, or quadratic. Regular expressions with certain characters or only wildcards have linear construction complexity, such as ^ABCD, ^AB.*...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com