Specific facial identity-based face identification access control system and implementation method
An access control system and face recognition technology, applied in character and pattern recognition, computer parts, instruments, etc., can solve the problems of inconvenience of the owner, low efficiency of the recognition system, long recognition calculation time, etc., to reduce security risks and system integration Installation cost, the effect of solving the inefficiency of real-name authentication, and reducing living and operation and maintenance costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
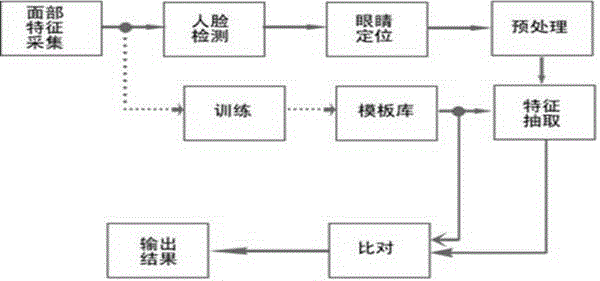
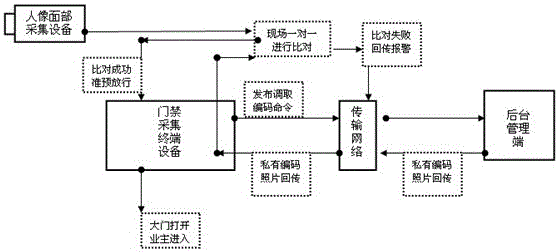
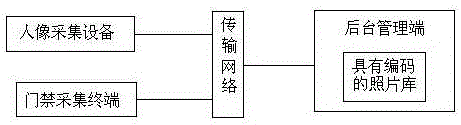
[0029] The present invention aims at the current situation of various and uneven access control system market products in the security technology link of the community, combined with the public security security portrait recognition and comparison business needs, relying on the industry-leading face recognition algorithm, adopting advanced dynamic local feature analysis technology, combined with network , database, distributed computing and other technologies, quickly realize the one-to-one comparison between the face collection information in the access control system and the system's preset facial feature codes, and help the security basic front-line units (residential communities, key units, companies, etc.) Perform access control management, and turn the unimaginable demand for comparison of tens of millions of massive photo libraries into the reality of calling feature marks (or codes) for on-site one-to-one comparison. This system not only solves the problem of low effici...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com