Business data processing method, account identification method, devices, and computer terminal
A technology of business data and processing methods, applied in data processing applications, computing, commerce, etc., can solve the problems of low accuracy, easy to be cracked, etc., to improve the recognition accuracy, improve the effect of marketing activities, and reduce marketing costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
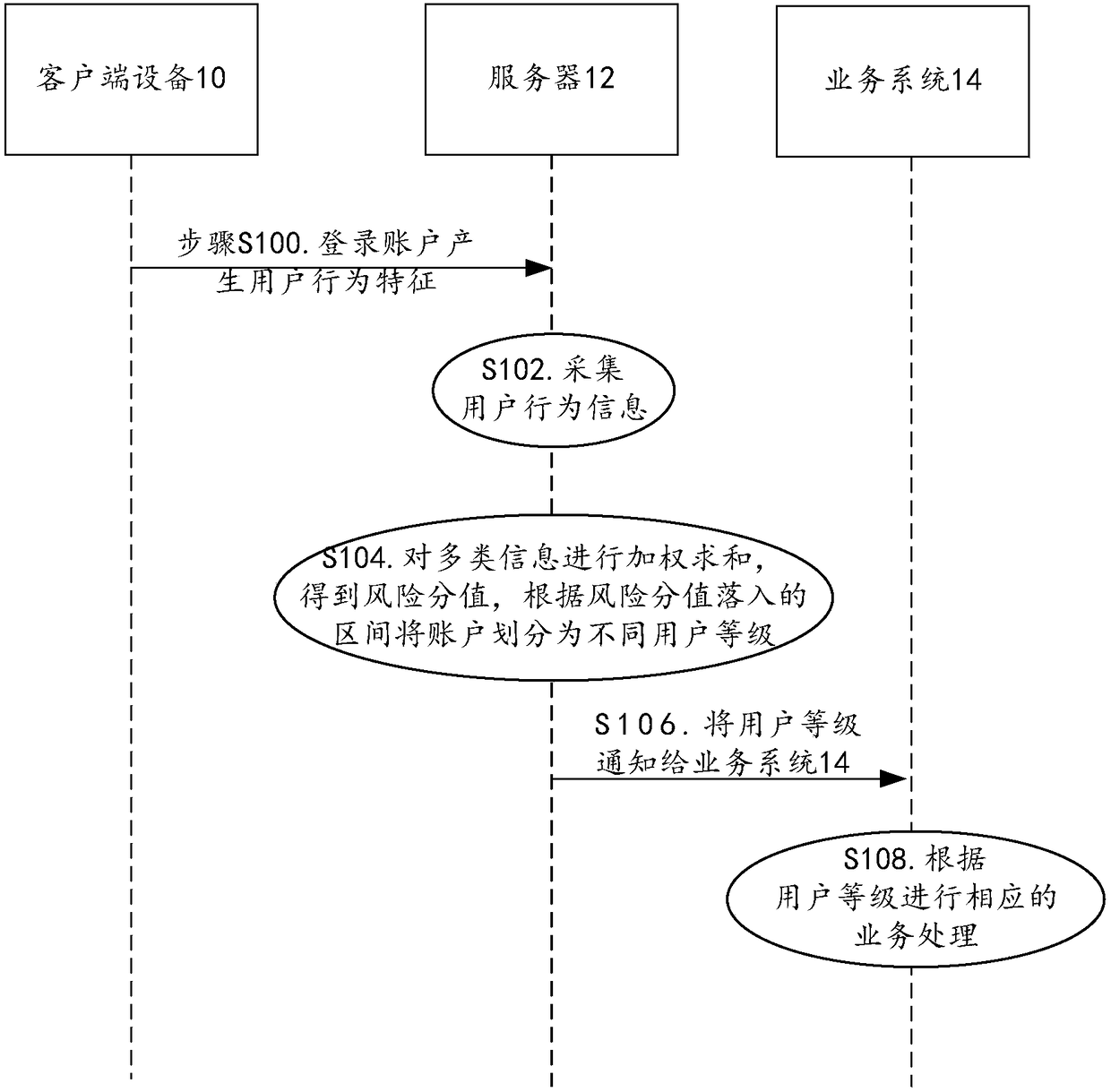
[0037] In related technologies, enterprise platforms, especially e-commerce platforms, often launch some preferential measures to stimulate users' desire to purchase, for example, attracting users by receiving red envelopes or coupons. With the increase of such preferential activities, some Cheating behaviors have also occurred one after another. For example, when an e-commerce platform launched a red envelope promotion, if the red envelope grabbing is based on SMS verification codes, illegal users can rent a SMS waiting platform to obtain a large number of red envelopes, and then promote them For customers who really need to consume, marketing resources are seized, and the marketing effect of the company is greatly reduced.
[0038] In order to solve the above problems, this embodiment can identify illegal accounts in combination with various information of the account to be identified, for example, identify the operation behavior of the account to be identified in combination...
Embodiment 2
[0081] According to the embodiment of the present application, a method for implementing image 3 The device of the processing method of the business data shown, such as Figure 4 As shown, the device includes:
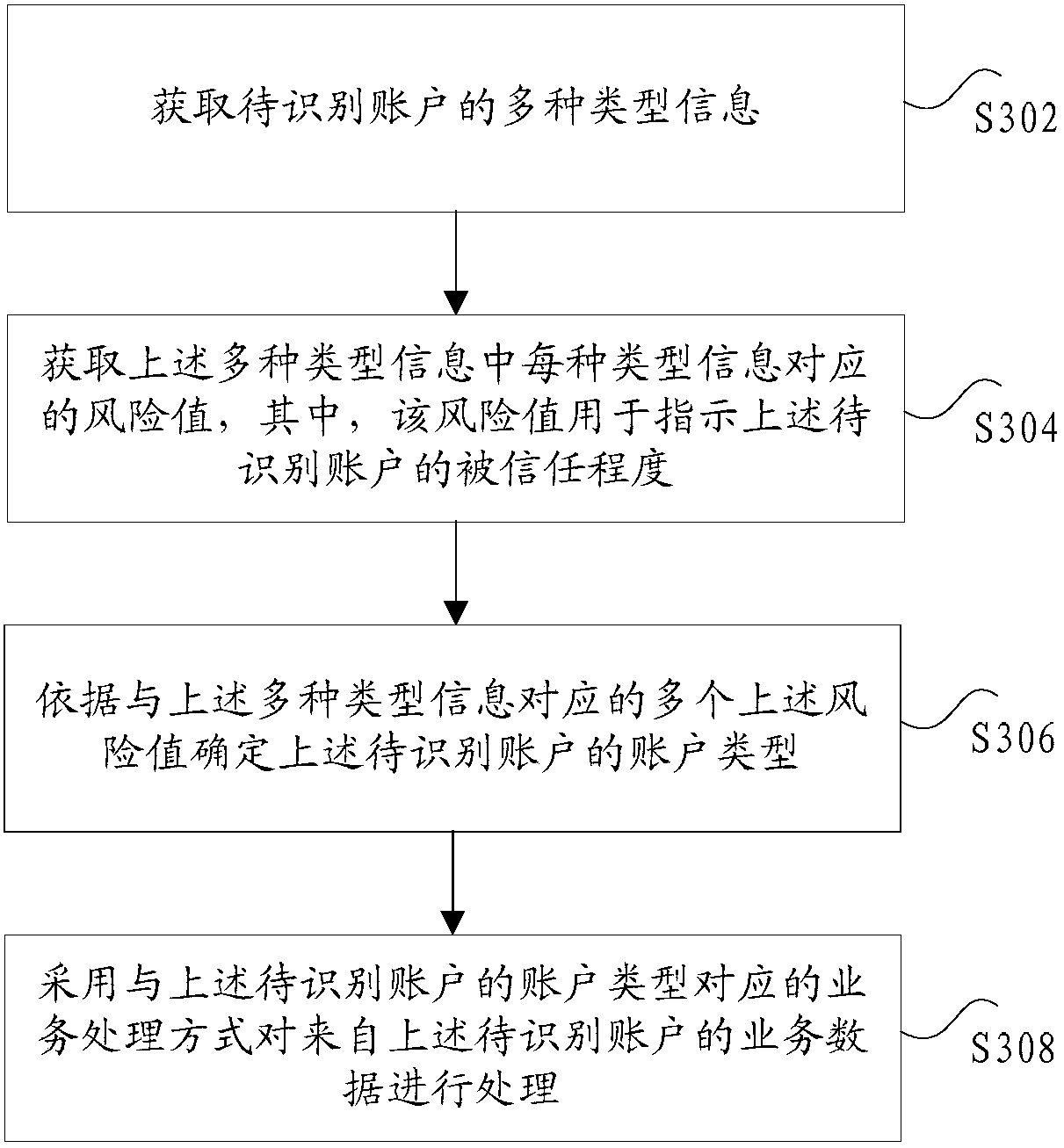
[0082] The obtaining module 40 is configured to obtain various information of the account to be identified; and obtain a risk value corresponding to each of the above various information, wherein the risk value is used to indicate the degree of trust of the above-mentioned account to be identified;
[0083] A determination module 42, connected to the acquisition module 40, configured to determine the account type of the above-mentioned account to be identified according to the multiple above-mentioned risk values corresponding to the above-mentioned various information;
[0084] The processing module 44 is connected to the determination module 42, and is configured to process the business data from the account to be identified by adopting a business processing meth...
Embodiment 3
[0088] This embodiment provides an account identification method, such as Figure 5 As shown, the method includes:
[0089] Step S502, acquiring various information of the account to be identified, wherein the various information includes at least one of the following: the current behavior characteristics of the account to be identified, the number of times the same device ID is used by the same account or multiple accounts, The number of accounts in the relationship network to which the account to be identified belongs, wherein the device ID is the ID of the device where the account to be identified accesses the website, and the relationship network is a network formed by connecting multiple accounts as vertices of a connected graph , the relationship scores between any two accounts in the above relationship network are greater than a preset threshold, , the above relationship scores are used to indicate the degree of association between the two accounts;
[0090] Step S504,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com