Method and system for realizing malicious code marking
A malicious code, the same technology, applied in the field of malicious code labeling based on texture clustering, can solve the problems of low accuracy of family labeling, inconsistent labeling methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
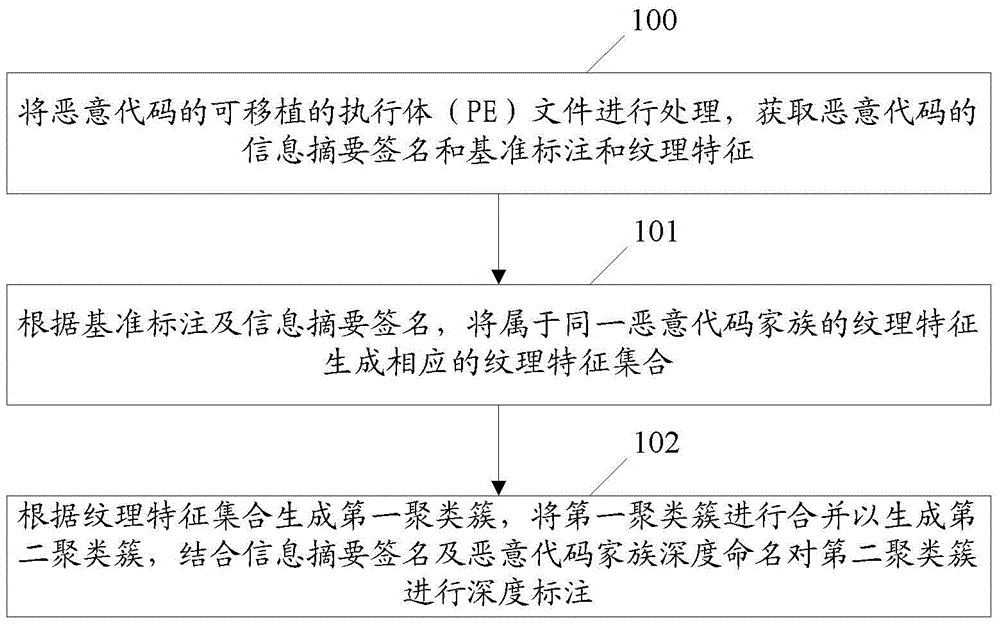
[0171] When the user's request to mark the malicious code is received, the malicious code submitted by the user will be cached according to the number of concurrent submissions using a message queue (such as RabbitMQ, Redis, ActiveMQ, etc.), and sent sequentially according to the first-in-first-out (FIFO) principle. To the labeling server, that is, for a malicious code, send it to the benchmark labeling server and the deep labeling server respectively.
[0172] Include the following steps:
[0173] The information digest of each malicious code in the PE file of the malicious code is obtained as the information digest signature of the malicious code.
[0174] It should be noted that if the PE file of the malicious code is directly sent to the baseline annotation server and the deep annotation server at the same time, both the baseline annotation server and the deep annotation server need to obtain the same information abstract as the information abstract signature. In order to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com