Multi-search supporting design method for encrypted database middleware
A design method and database technology, applied in the field of information security, can solve problems such as data leakage, privacy security concerns, and inability to support querying of database aggregation functions, so as to ensure consistency and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Below in conjunction with accompanying drawing, the present invention is described in further detail.
[0025] 1. Architecture
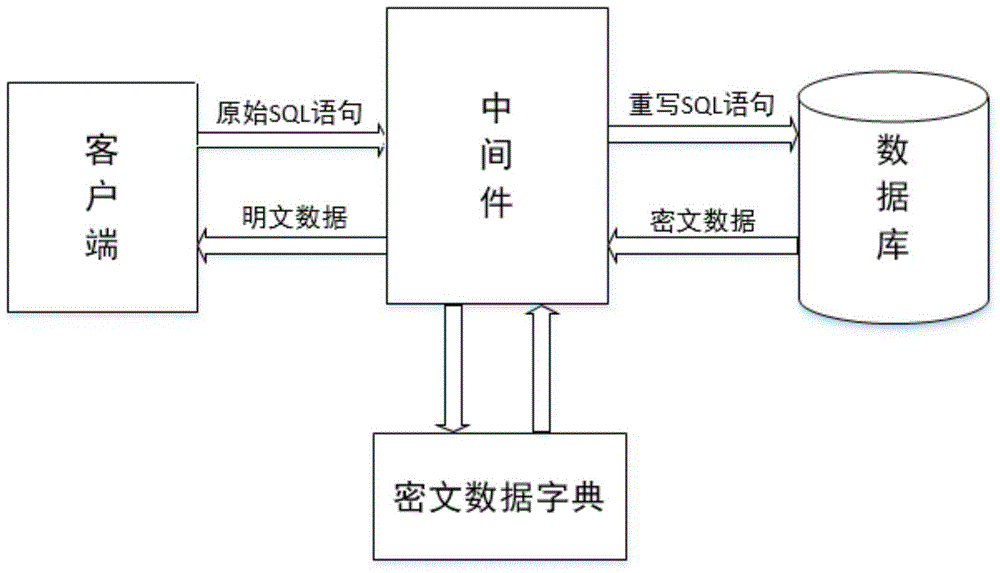
[0026] Such as figure 1 As shown, the middleware system of the present invention is built between the client and the database, the original SQL statement of the client is received by the multi-query middleware system, and the database is realized by rewriting the SQL statement on the basis of establishing a ciphertext data dictionary. Data encryption and relational schema anonymization. The system can receive the query results of encrypted data in the database, and decrypt the ciphertext data through the established ciphertext data dictionary, so that the client can obtain usable plaintext data. This architecture can realize the transparency of the client to the database, only needs the client to use the standard SQL statement, and does not modify the original structure of the database, and can realize the query of the ciphertext data of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com