Method and device for detecting Android malicious software in batch
A malware detection method technology, applied in the field of Android platform application security analysis, can solve the problems of insufficient features and inability to detect malware, and achieve the effect of high accuracy and few omissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
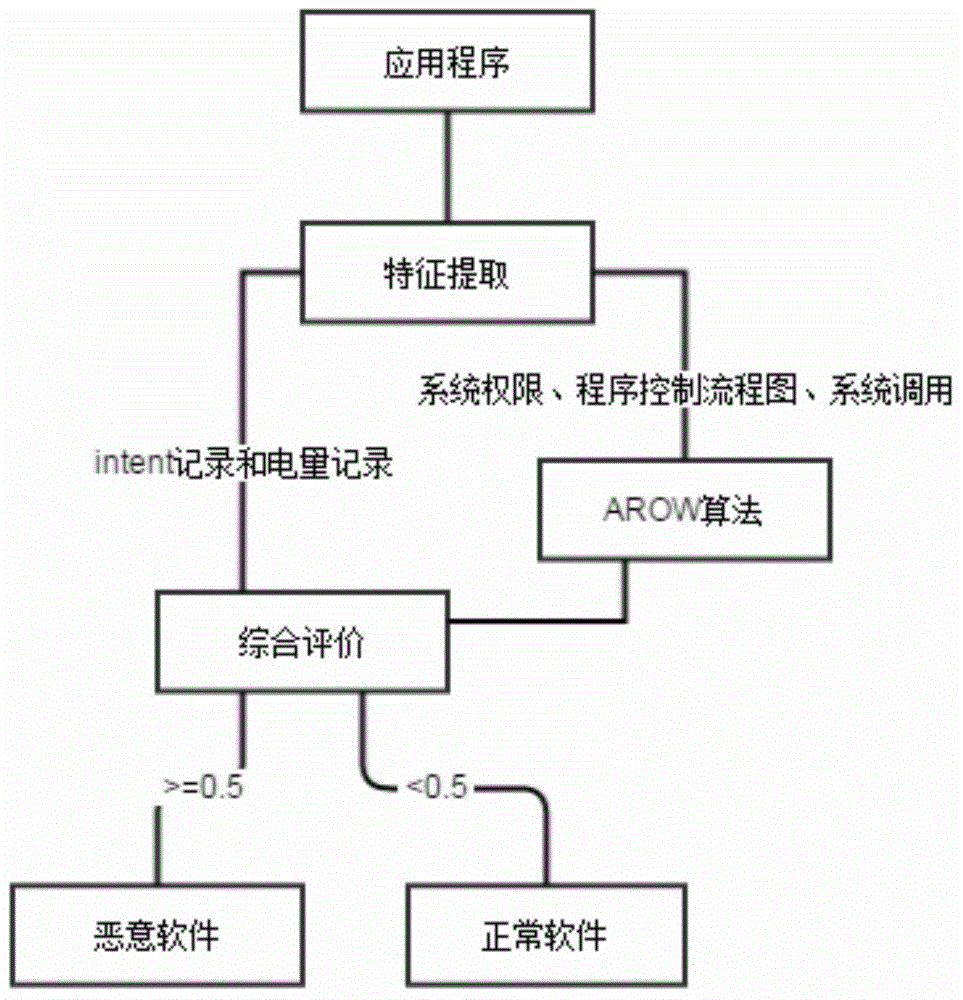
[0023] The malicious software detection flow chart of the embodiment of the present invention is as follows figure 1 shown. The flowchart is mainly divided into three modules: feature extraction module, AROW (an online classification algorithm) classifier module, and comprehensive evaluation module.
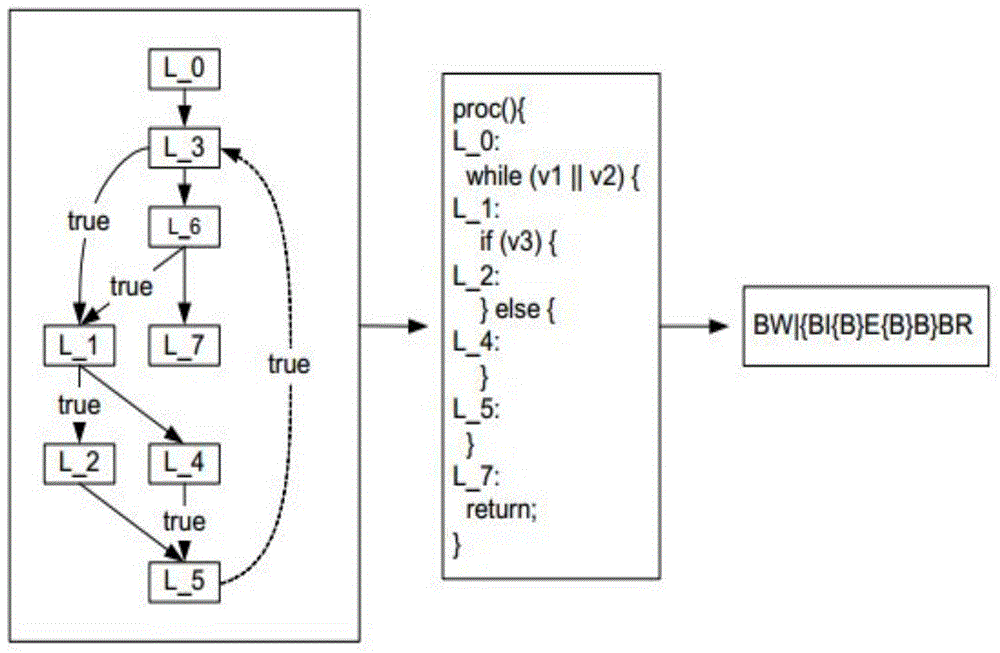
[0024] The feature extraction module extracts the system authority features, program control flow chart features and system call features of the application program, calculates the frequency vectors of each feature (respectively the first frequency vector, the second frequency vector, and the third frequency vector), and combines them into The eigenvectors are integrated, and then the AROW algorithm is used to classify, and the classification result is weighted with the first contribution value of the power record to the malware detection and the second contribution value of the intent record to the malware detection to judge the application program.
[0025] In the feature extr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com