Network evidence taking content tracing method based on multiple fingerprint Hash bloom filters
A Bloom filter and filter technology, applied in the direction of instruments, special data processing applications, electrical digital data processing, etc., can solve the problems of traceability and insufficient traceability, and achieve strong traceability and efficiency, high processing efficiency and accuracy rate, the effect of high compression ratio
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be further described below through specific embodiments and accompanying drawings.
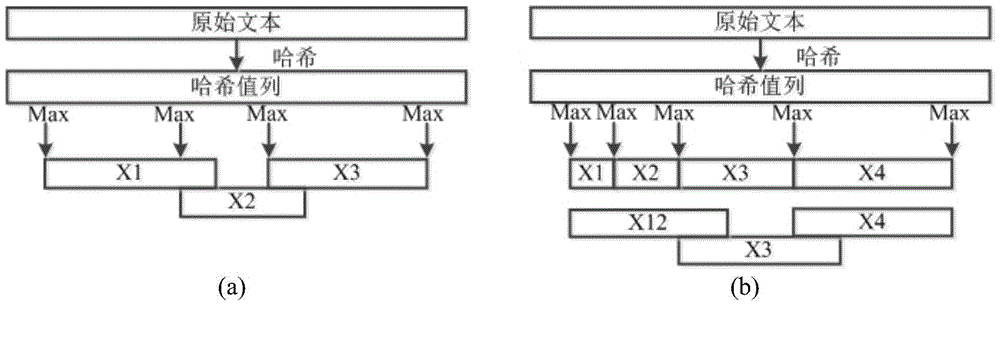
[0032] In order to realize content traceability in network security incidents, the present invention provides a network forensics content traceability method and system based on an enhanced fingerprint multi-hash Bloom filter (EWMB), and the system is referred to as CAS. It mainly includes two aspects: (1) the design of network forensics content traceability system (CAS) architecture; (2) a data structure of enhanced fingerprint multi-hash Bloom filter (EWMB) is proposed.
[0033] The structure diagram of the network forensics content traceability system (CAS) of the present invention is as follows figure 1 As shown, it includes the following three parts:
[0034] (1) Data reorganization: reorganize the original network traffic data packets ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com