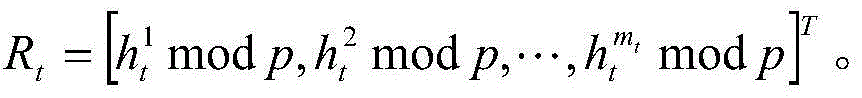Privacy protection type attribute matching method based on symmetrical encryption
A technology for attribute matching and privacy protection, applied in the field of matching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with specific drawings and embodiments.
[0035] Such as figure 1 Shown: In order to be able to resist man-in-the-middle attacks and matching result spoofing attacks without any trusted third party, and to effectively save computing and communication overhead, the present invention performs privacy-preserving attribute matching in social networks based on symmetric keys And secure channel establishment method, use the public attribute shared between users to generate a key, use the key to encrypt the connection establishment request and secure channel key, and use symmetric encryption to significantly reduce computing overhead, so as to meet various social needs The network responds to the needs of user privacy protection and computational efficiency. Therefore, the method for attribute matching includes the following steps:
[0036] Step 1. Each user v in the social network k Both create a file A w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com