Distributed type (k, n) threshold certificate-based encrypting method and system
An encryption method and distributed technology, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve the problem of no security in the system, weak ability to resist denial of service attacks and certificate server failures, master key Weak ability to leak, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
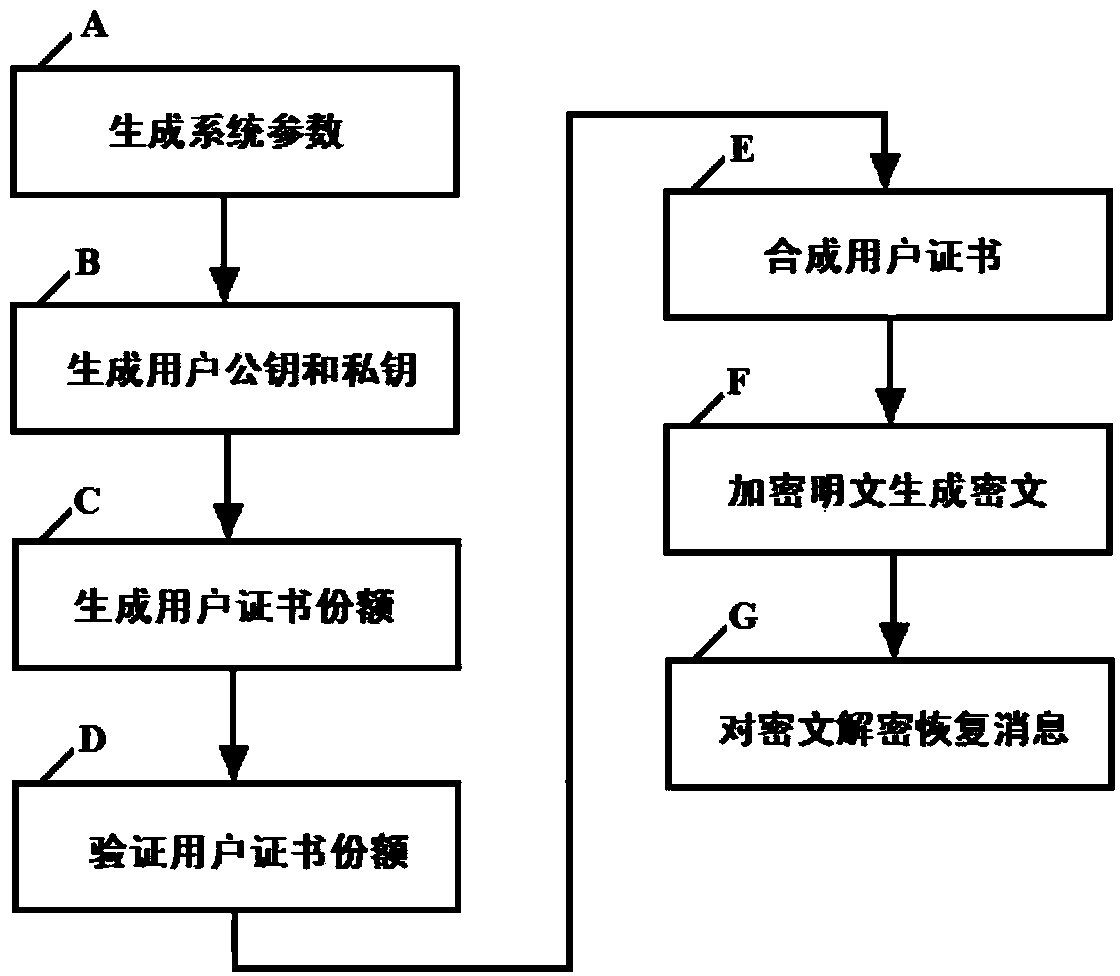
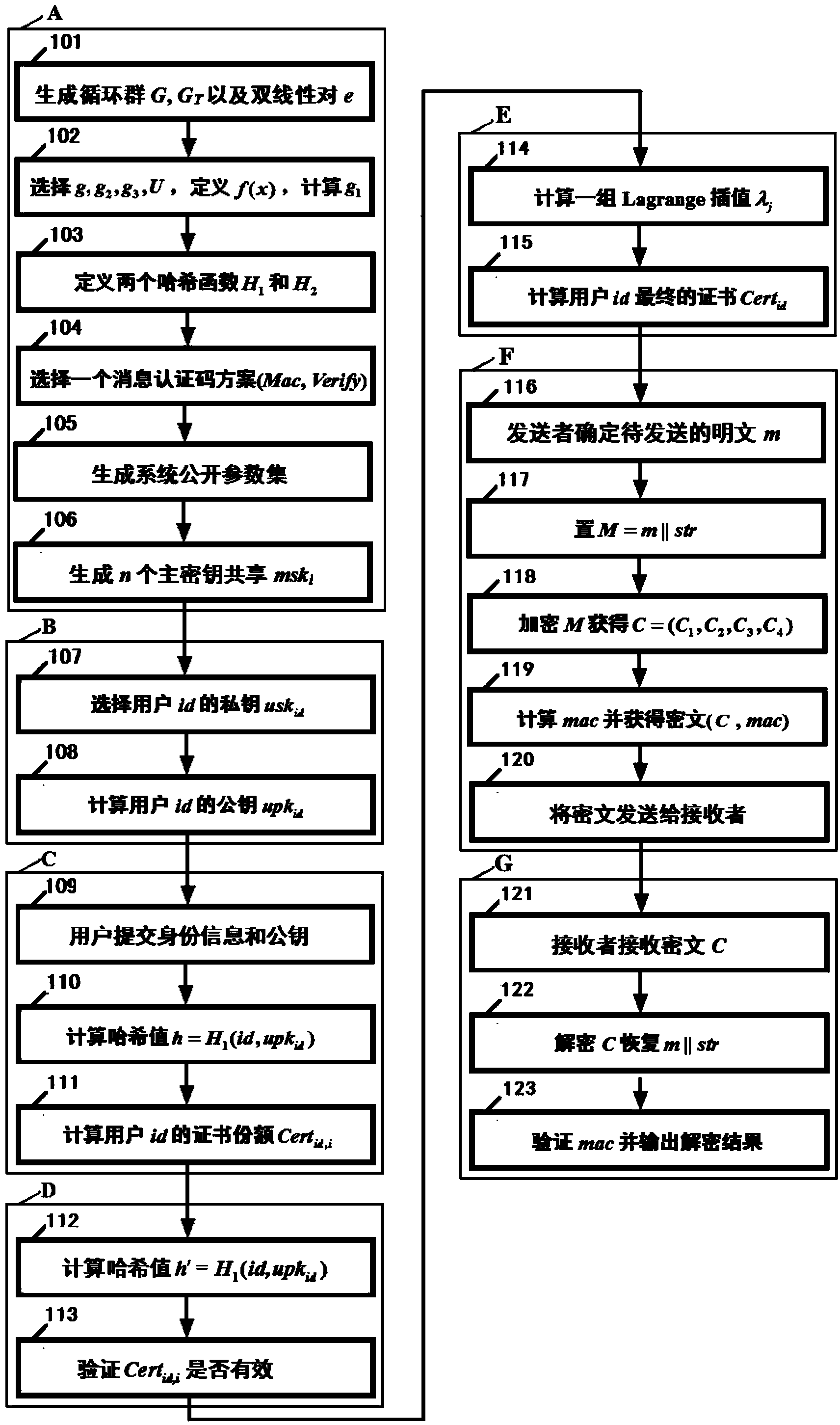
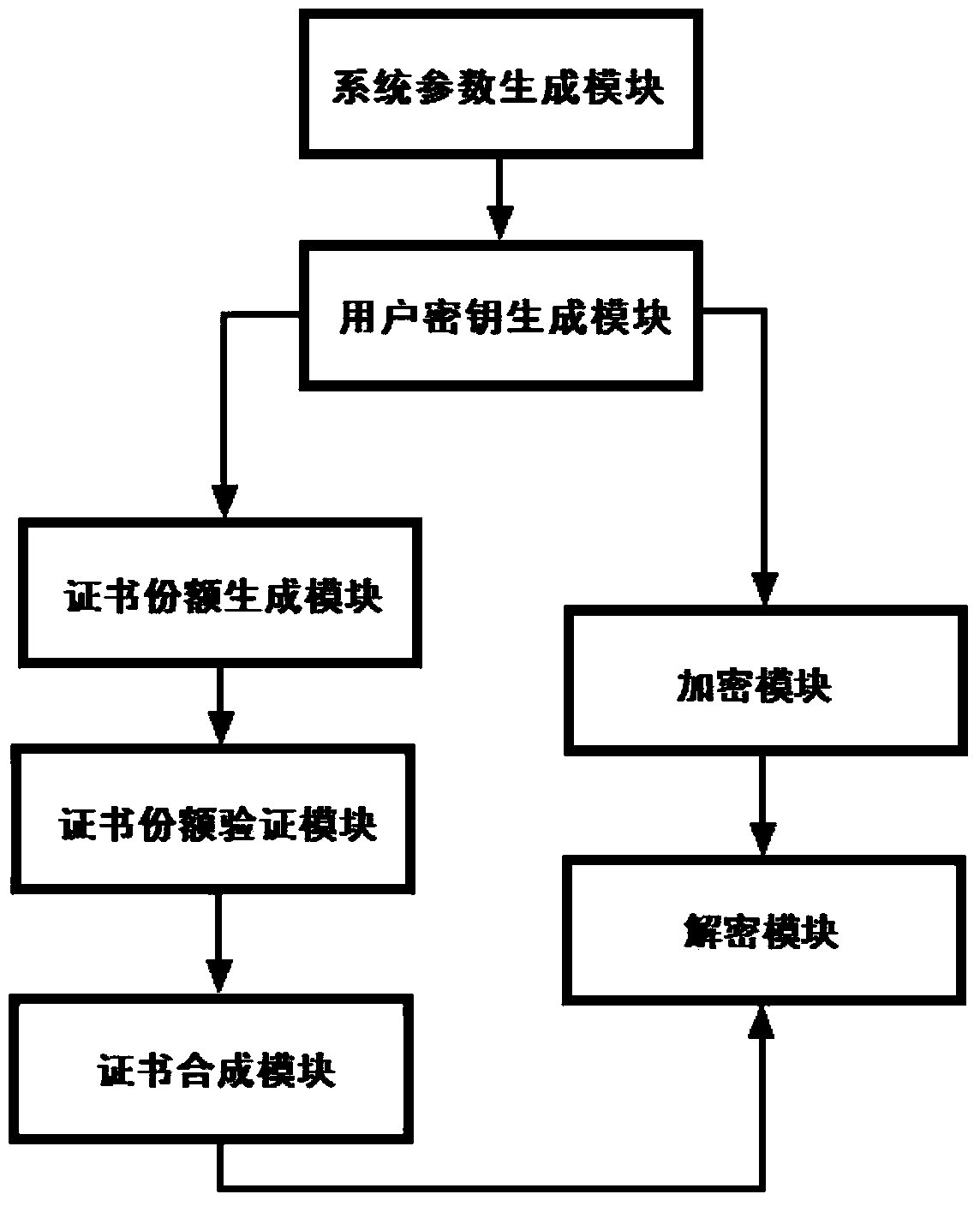
[0072] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
[0073] The encryption method based on (k, n) threshold certificates in the present invention can be realized based on bilinear pairing and Shamir secret sharing technology. The bilinear pairing and Shamir secret sharing technology will be briefly introduced below.
[0074] Let G and G T are two p factorial cyclic groups, where p is a large prime number and g is the generator of the group G. Suppose G and G T The discrete logarithm problem on both groups is hard. If defined in groups G and G T Previous mapping e:G×G→G T Satisfy the following three properties, then the mapping is called a valid bilinear pairing. Bilinear pair e: G×G→G T is the Cartesian product G×G to the group G T The mapping, that is, the bilinear pairing e:G×G→G T Refers to the function z=e(u,v), where u, v∈G are independent variables, z∈G T as the dependent variable.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com