Industrial control identity authentication method and device with state cryptographic algorithms
A technology of identity authentication and industrial control, applied in user identity/authority verification, digital data authentication, public key for secure communication, etc., can solve national information security threats and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
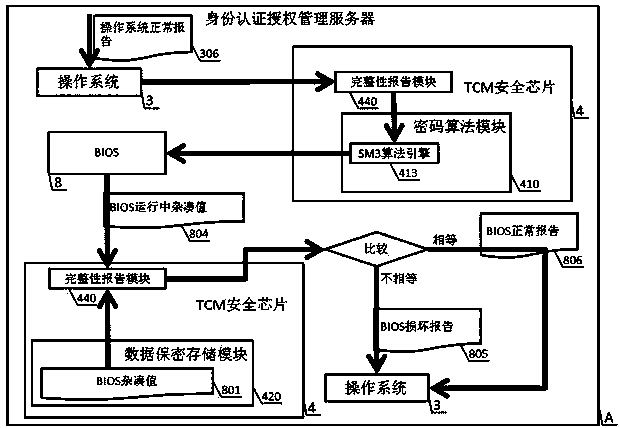
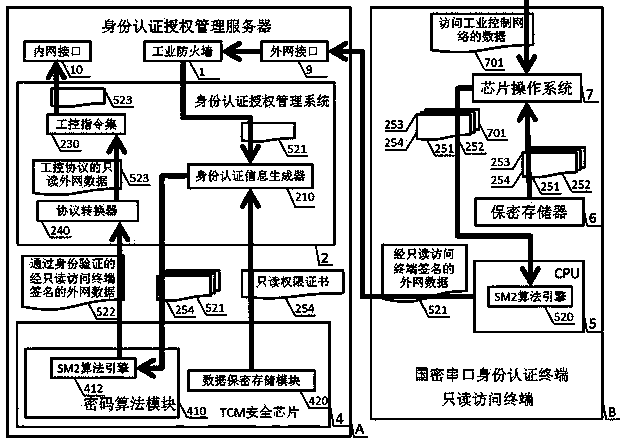
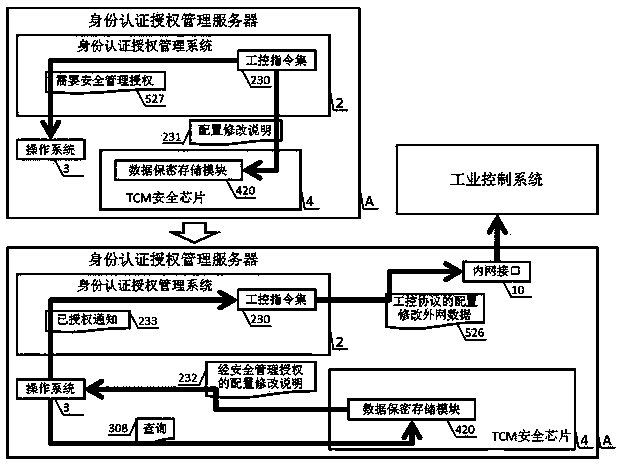
[0071] see Figure 1 to Figure 26 , to realize an industrial control identity authentication method and device applying the national secret algorithm of the present invention, which is composed of two parts: an identity authentication authorization management server A and a national secret serial port identity authentication terminal B. An identity authentication and authorization management server A is composed of a TCM security chip 4, an operating system 3, an identity authentication and authorization management system 2, an industrial firewall 1, an external network interface 9, an internal network interface 10, and BIOS8; it consists of an SM1 algorithm engine 510 and an SM2 algorithm engine 520, the CPU 5 of the SM3 algorithm engine 530, the secure memory 6, and the chip operating system 7 form the national secret serial port identity authentication terminal B. The TCM security chip 4 is composed of a cryptographic algorithm module 410, a data security storage module 420...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com