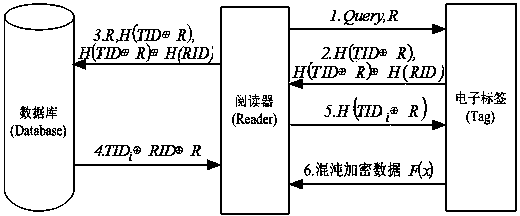
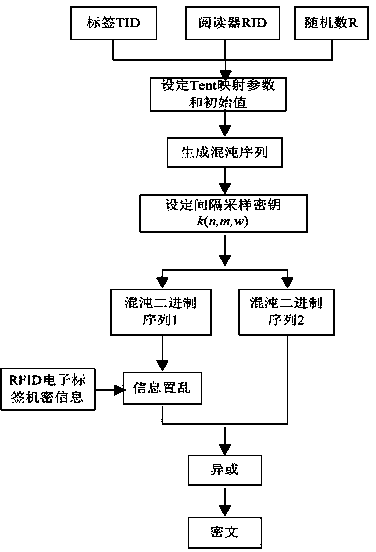
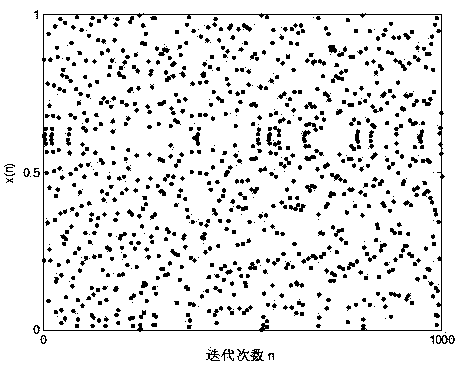
Bidirectional authentication method of radio frequency identification system
An identification system and two-way authentication technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] The invention will be further illustrated by the following examples.
[0080] Specific simulation standard data selection.
[0081] (1) The tag TID is 1000100010001000; the corresponding tent mapping initial value:
[0082] x 0 =(1000100010001000) 2 '1.5259'10 -5 =0.5348.
[0083] (2) The RID of the reader is 0010001000100010; the corresponding Tent mapping parameters:
[0084] α= (0010001000100010) 2 '1.5259'10 -5 =0.1337.
[0085] (3) The random number R generated by the reader during the authentication process is 0000000000111010; according to the "set interval sampling key" introduced in the encrypted technical solution S4 in the summary of the invention k ( n , m , w )", the key can be obtained:
[0086] k ( n , m , w )=(0000000000111010) 2 ⊕(2 16 -1)=(1111111111000101) 2 = k (512,3,10).
[0087] (4) Suppose the confidential information text stored in the RFID tag is "one world one dream", and the ASCII code corresponding to the information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com